Attack Surface vs Attack Vector in Cybersecurity
The attack surface represents what can be attacked, your exposed assets and entry points. Attack vectors are how attacks happen, the specific exploitation techniques used to breach those exposures.
The attack surface represents what can be attacked, your exposed assets and entry points. Attack vectors are how attacks happen, the specific exploitation techniques used to breach those exposures.

Attack surface is what can be attacked (your exposed assets and entry points), while attack vectors are how attacks happen (the specific techniques used to exploit those exposures). Effective security requires managing both.
Security teams often use "attack surface" and "attack vectors" interchangeably, which leads to incomplete security strategies and misallocated resources.
The distinction matters: Attack surface answers "what can be attacked"—the exposed entry points in your infrastructure. Attack vectors answer "how attacks happen"—the specific techniques attackers use to breach those points.
Both require different defensive approaches. Your attack surface determines what you must protect. Attack vectors determine how you protect it. The relationship between them determines your actual security posture.
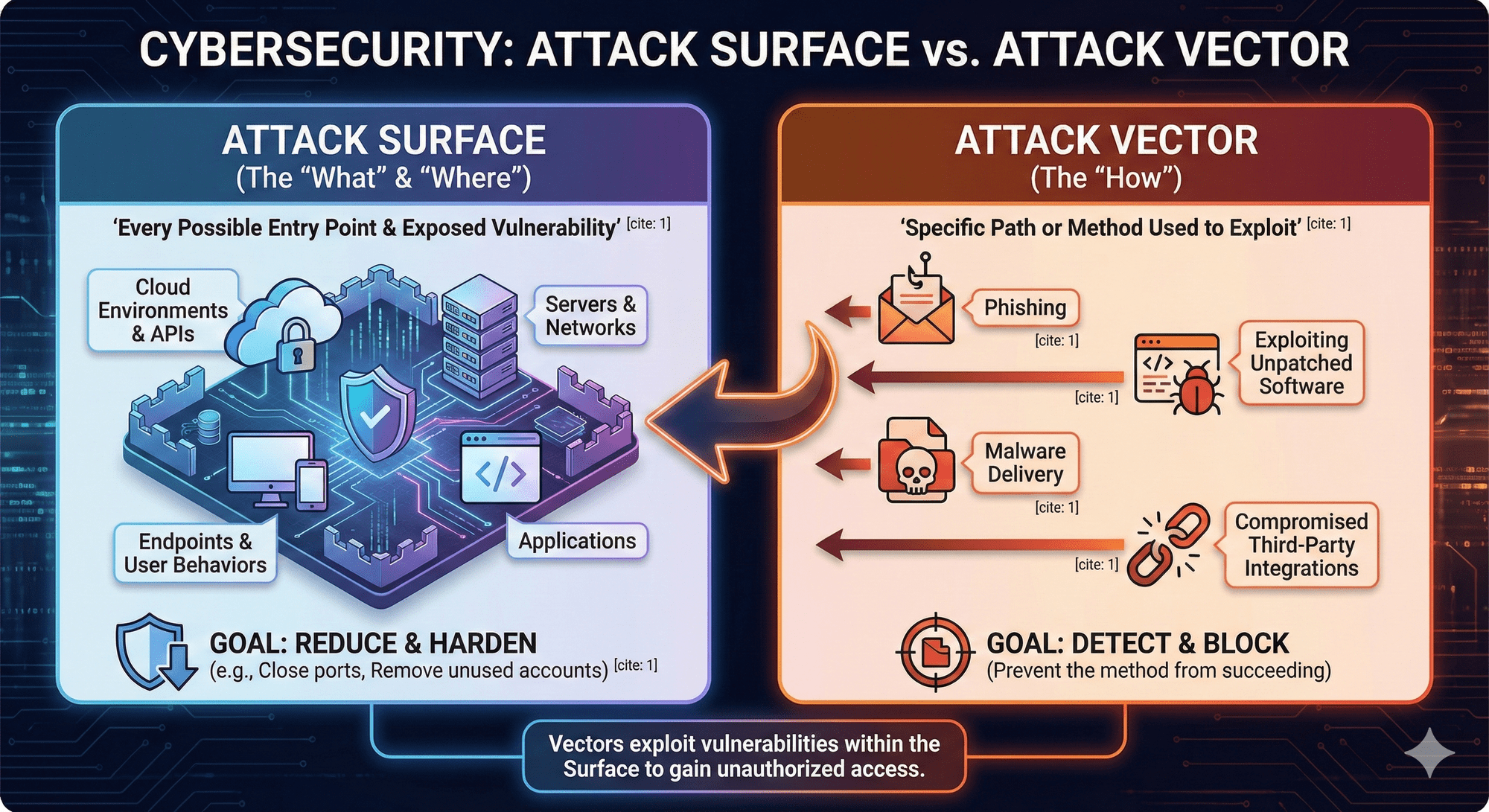
Think of your attack surface as every possible entry point an attacker could target in your systems. It's everything that's exposed and potentially vulnerable—your network, servers, cloud environments, applications, endpoints, APIs, and even user behaviors. The larger your attack surface, the more opportunities an attacker has to find a weakness.
For example, a company using multiple cloud platforms, remote work devices, and third-party apps has a bigger attack surface than a small office network with only a few systems. The goal of security teams is to reduce the attack surface wherever possible—by closing unnecessary ports, removing unused accounts, and ensuring that only essential services are exposed.
An attack vector, on the other hand, is the specific path or method an attacker uses to exploit a vulnerability within that attack surface. It's how an attacker actually gets in.
Common attack vectors include:
Using the earlier example, if your attack surface includes a cloud database, the attack vector might be a misconfigured permission that allows unauthorized access, or stolen credentials from a phishing attack.
Think of it like this: your attack surface is all the doors and windows in your house—every possible way someone could get in. An attack vector is the specific method a burglar uses to break in. Security teams work to reduce the number of doors and windows (shrinking the attack surface) and strengthen the ones that remain to block likely entry points (defending against attack vectors).
By understanding both concepts, organizations can prioritize defenses more effectively: shrink the attack surface to reduce exposure and protect against known attack vectors to prevent exploitation.
Attack vectors exploit specific elements within your attack surface. Your attack surface provides the landscape; attack vectors are the paths through that landscape.
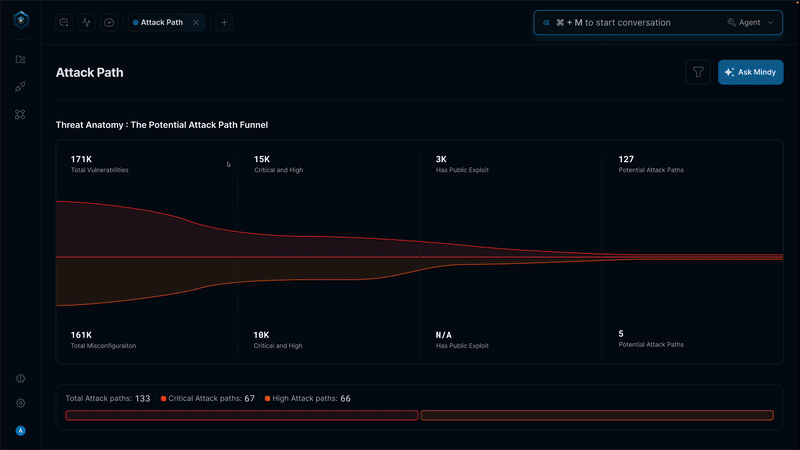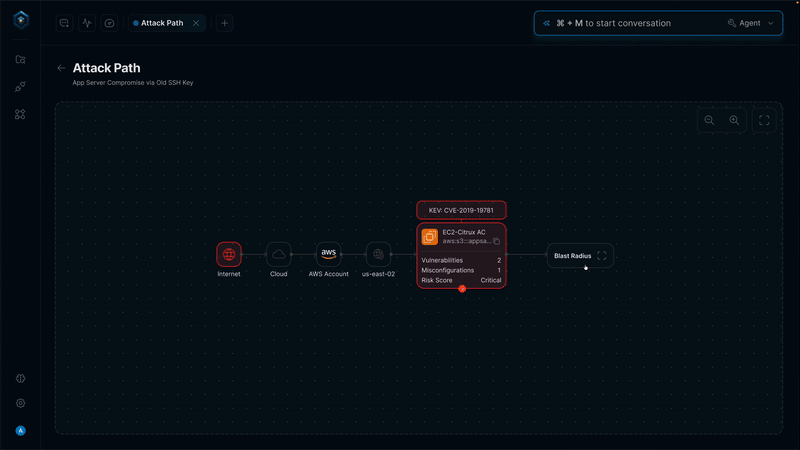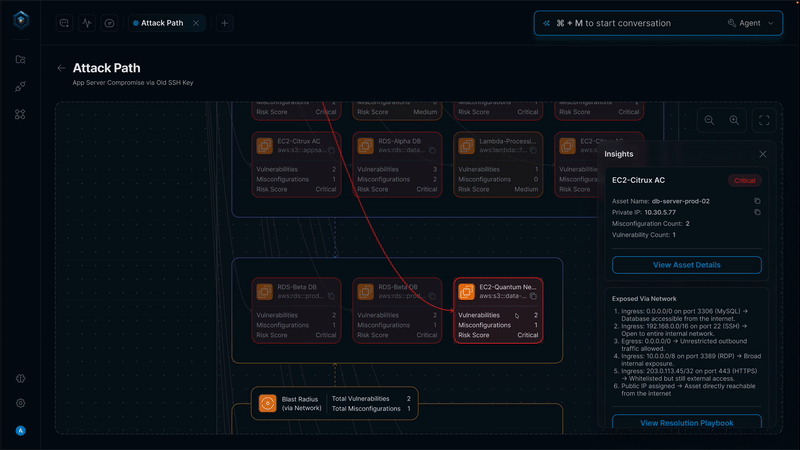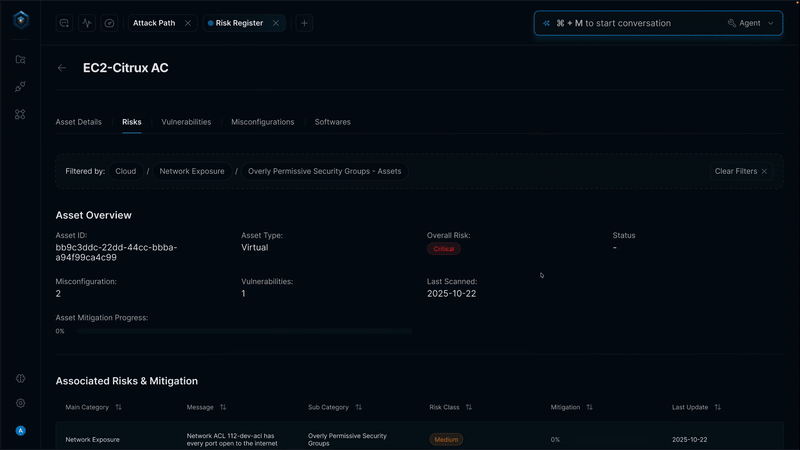
Attackers first identify your attack surface through reconnaissance—scanning exposed IP addresses, enumerating cloud resources, discovering employee email addresses, and mapping DNS records. This reveals which assets are exposed, what data they hold, and where the weakest points exist.
Every new system expands your attack surface and creates opportunities for multiple attack vectors. For example, a misconfigured cloud storage bucket might be vulnerable to 5-10 attack vectors, ranging from unauthorized access to data exfiltration to privilege escalation.
Incident response differs fundamentally when addressing attack surface vulnerabilities versus attack vectors—the focus, timeline, and actions required are distinct:
These are the structural weaknesses in your environment—like exposed servers, misconfigured cloud storage, or unused accounts. Response focuses on strategic fixes: patching systems, removing unnecessary services, segmenting networks, and decommissioning orphaned accounts. The goal is to reduce opportunities for attackers across the board.
These are the specific ways attackers try to exploit your systems—like phishing emails, malware, or credential stuffing. Response is tactical: investigate incidents, contain the attack, block malicious activity, and remediate affected systems. The goal is to stop active threats before they succeed.
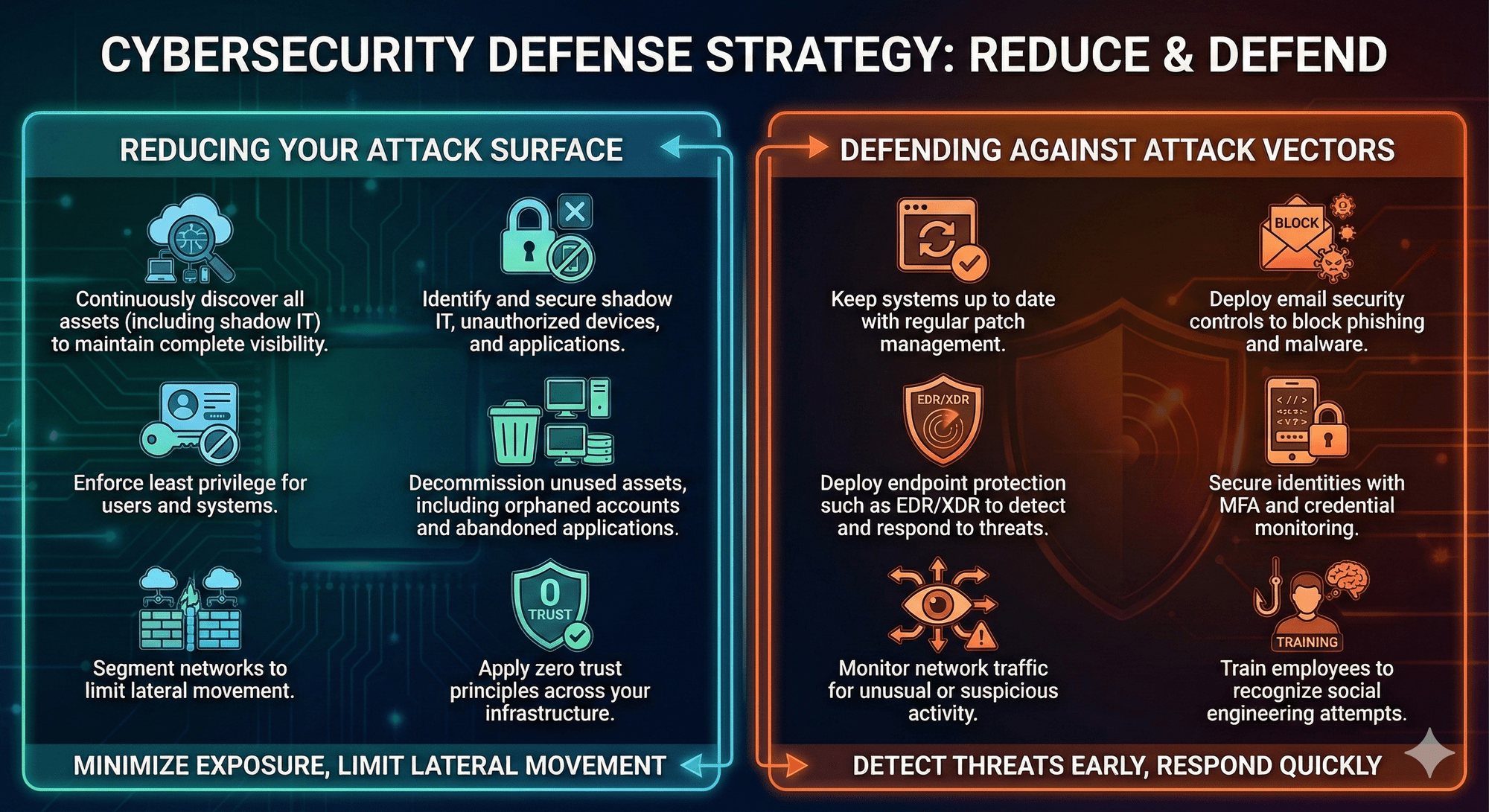
Neither approach works alone. Shrinking the attack surface limits opportunities for attackers, while defending against attack vectors stops them from exploiting weaknesses. Together, they create a layered, defense-in-depth strategy that significantly strengthens your overall security.
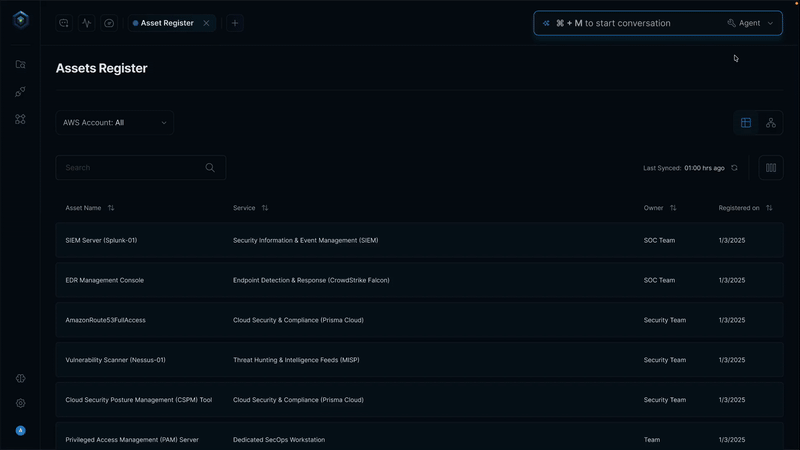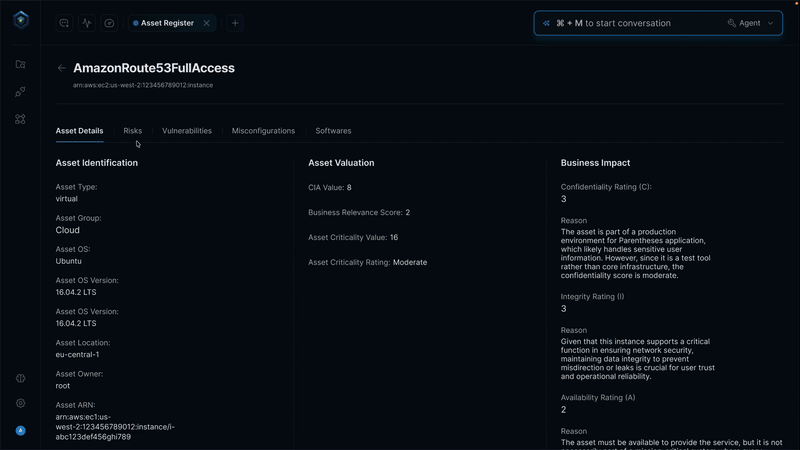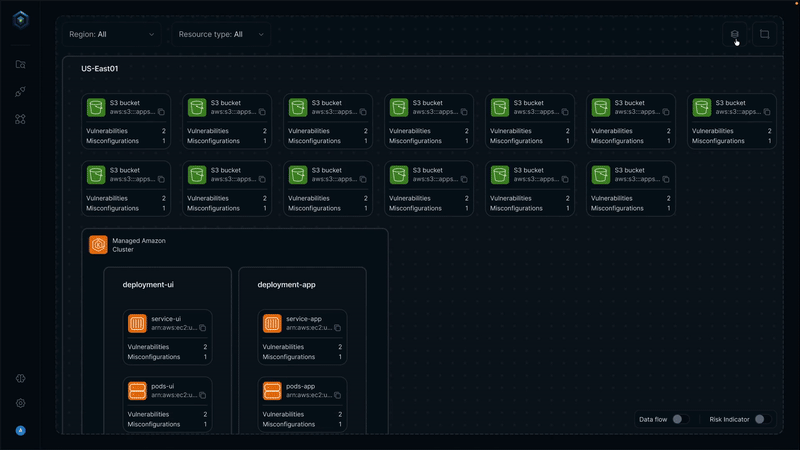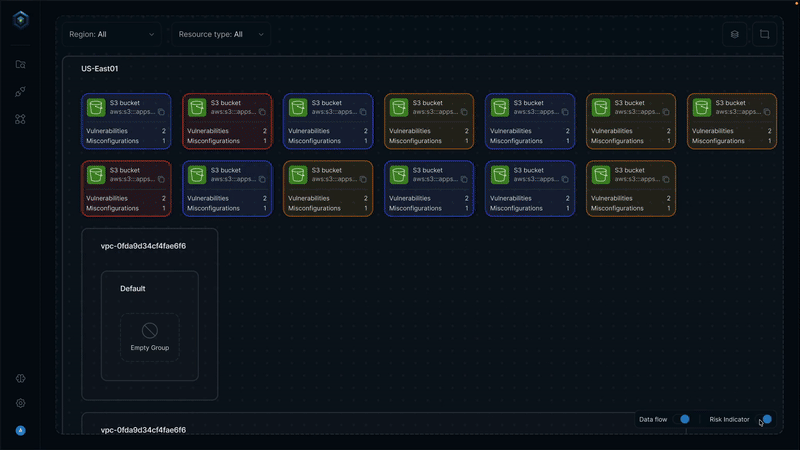
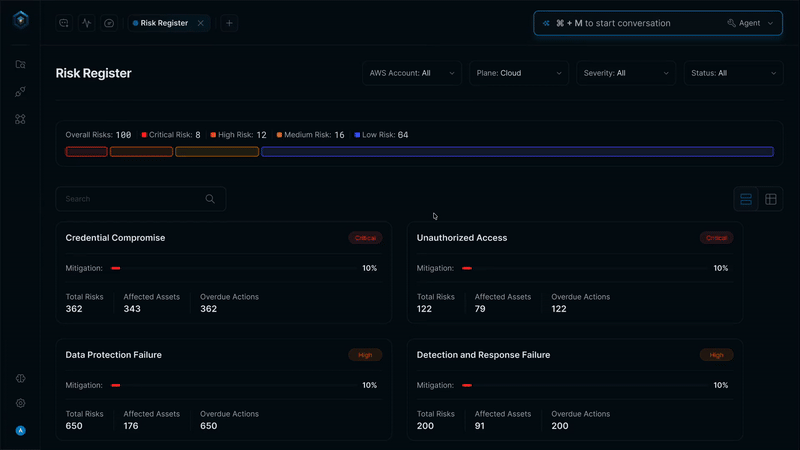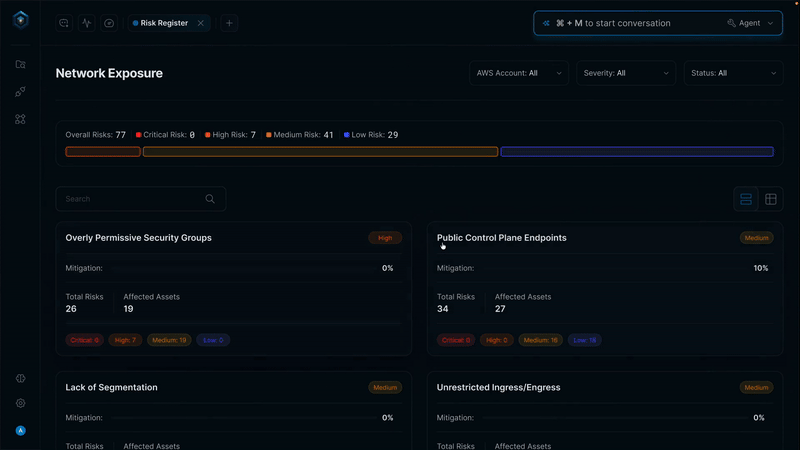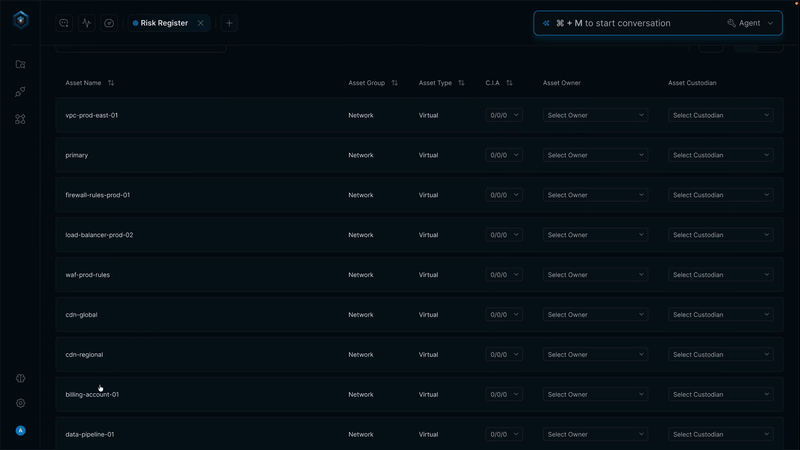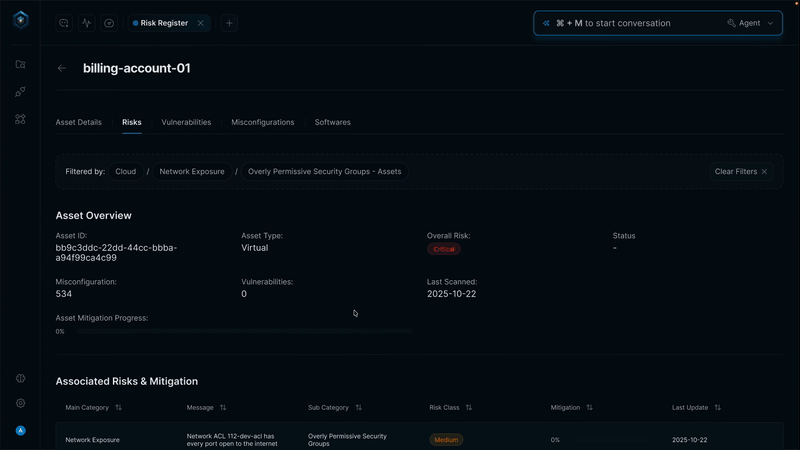
Secure.com continuously discovers assets across all environments and maps your attack surface in real time with clear visualizations. It detects shadow IT, identifies misconfigurations, and prioritizes risks based on business criticality, so you know what matters most.
Digital Security Teammates work 24/7 to keep your environment safe. They automatically detect threats and execute approved response workflows (with human approval for sensitive actions), while AI-powered case management helps your team triage incidents faster, reducing MTTR by 45-55%. Combined with threat intelligence and behavioral analytics, they spot unusual activity early, before it turns into a breach.
All your assets, users, identities, and vulnerabilities connect through a knowledge graph that provides a single, unified view of your security posture. Context-aware risk scoring and automated workflows link remediation and response, ensuring both attack surface reduction and vector defense work together seamlessly.
Yes. A single web application (small attack surface) might be vulnerable to SQL injection, XSS, credential stuffing, brute-force attacks, and CSRF (multiple attack vectors). Surface size doesn't determine vector vulnerability—security posture and secure development practices do.
Continuously. Modern cloud-native environments change too rapidly for periodic assessments—new assets spin up in minutes, configurations drift, and shadow IT emerges constantly. Effective attack surface management requires real-time monitoring with automated discovery.
Both. Vendors expand your attack surface through connection points, API integrations, and data sharing. They introduce attack vectors when their security is weak—such as supply chain attacks, compromised credentials, malicious code injection, and vulnerable dependencies.
Both approaches are essential, but reducing your attack surface offers longer-lasting risk reduction. Closing an exposed database, for example, eliminates all attack vectors targeting it in a single action, preventing SQL injection, unauthorized access, data exfiltration, and privilege escalation simultaneously. That said, critical systems must remain accessible. Focus on reducing the surface wherever possible, and defend against attack vectors where exposure is unavoidable.
Zero trust architecture addresses both dimensions of security. It shrinks the attack surface by enforcing least privilege and microsegmentation, while defending against attack vectors through continuous verification, context-aware access controls, and assume-breach principles. Zero trust provides a framework for effectively managing both the attack surface and attack vectors.
Attack surface and attack vectors are closely linked, but they're not the same, and understanding the difference matters. Your attack surface is everything that could be targeted. Attack vectors are the specific paths attackers use to exploit those weaknesses.
Adequate security means tackling both: reducing your exposure and defending against potential attacks. Incident response varies too—remediating the surface is more about architecture, while stopping attack vectors is tactical. With attack surface intelligence, you get the visibility needed to manage both effectively.
Secure.com gives you a unified view of your attack surface and active attack vectors—with continuous asset discovery, context-aware risk prioritization, and automated response workflows (with human approval for sensitive actions).
Book a demo to map your exposures and strengthen your defenses.

Most apps today run on open source code — and 84% of those codebases carry at least one known security vulnerability.
AI handles repetitive work. Your L1 and L2 analysts handle everything else.

SOC 1, SOC 2, and SOC 3 are not levels — they're three separate audit reports that serve completely different purposes. Here's how to tell them apart.