How to Prevent Cloud Misconfiguration for Secure IT
Misconfigurations are the #1 cause of cloud breaches—discover how to move from "finding" them to "fixing" them with AI-driven guardrails.
Misconfigurations are the #1 cause of cloud breaches—discover how to move from "finding" them to "fixing" them with AI-driven guardrails.

Cloud misconfiguration—not advanced malware—is the leading cause of cloud data breaches. It occurs when security settings (like storage buckets, firewalls, or IAM roles) are left on default or set up incorrectly. While traditional tools drown teams in alerts (many of them false positives), the solution lies in unified visibility, automated remediation, and AI-driven governance that catches drift before attackers do.
It is the open secret of the cybersecurity world: You probably won’t get hacked by a zero-day exploit; you’ll get hacked because someone left a digital door unlocked.
According to industry analysis from Gartner and IBM, up to 99% of cloud security failures through 2025 will be the customer’s fault, primarily due to misconfigurations.
This isn't about negligence—it's a complexity problem that overwhelms even skilled IT and SecOps teams. For instance, a Reddit user recently disclosed that their fresh cloud security instrument identified 847 “critical” flaws on the first day, but then they found out that 782 of them were false alarms. It is difficult for teams to identify the actual threats amongst the countless alarms; therefore, real threats, such as having an unencrypted Redis database or granting too much authority to an IAM role may go unnoticed.
In this guide, we break down what cloud misconfiguration actually looks like, why it happens, and how to stop chasing alerts and start enforcing security.
Cloud misconfiguration refers to errors, gaps, or weaknesses in the security settings of a cloud environment. Instead of a flaw in the software code itself, it is a flaw in how that software is deployed or managed.
Imagine buying a state-of-the-art bank vault (the cloud provider's infrastructure) but propping the door open with a brick (your misconfiguration). In this case, even though the vault functions as expected, the breach occurred because of your actions.
Common examples include leaving storage buckets public, granting admin rights to short-term contractors, or failing to enable database encryption.
Based on data from SentinelOne, UpGuard, and Vectra AI, these are the most common offenders:
Why do smart engineers make these mistakes?
The consequences go beyond a "slap on the wrist" from an auditor.
Manual checklists can't keep pace with cloud-native environments. Effective identification requires a layered, continuous approach:
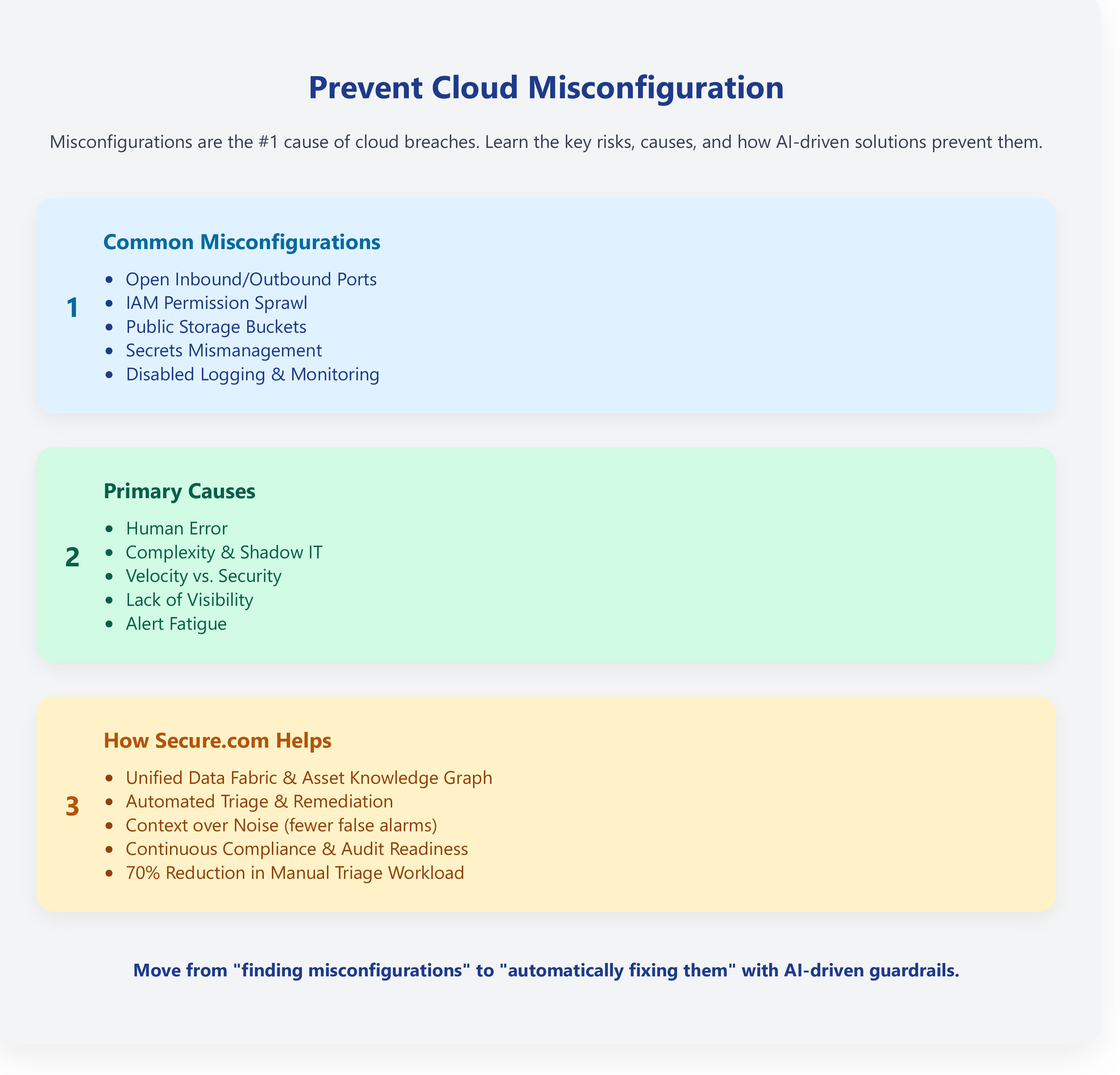
Traditional tools shout about problems; Secure.com fixes them. We built Secure.com to close the gap between "knowing" and "doing." Instead of dumping a CSV of 1,000 alerts on your overworked team, our Digital Security Teammates augment your staff.
The Result: Organizations using Secure.com report 70% reduction in manual triage workload and 45-55% faster Mean Time to Respond (MTTR).
The top errors are leaving security group ports wide open (0.0.0.0/0) and exposing cloud storage buckets to the public—both create significant breach risk.
No. The Shared Responsibility Model means the cloud provider secures the infrastructure (hardware, datacenters, hypervisor), but you're responsible for securing everything you put in the cloud—your data, applications, configurations, and access controls.
Continuously. Clouds change by the minute. You can’t just check once a month because that’s not enough to see if there has been any “drift” or change over time that might cause problems when it’s detected too late in your monitoring.
Cloud misconfiguration is a solvable problem, but it requires a shift in mindset. You cannot manually manage millions of configuration settings. The future of secure IT is governed by autonomy, where AI and automation are employed to keep security at a certain level all day, every day, and throughout the year.
By using technology that provides context instead of noise, you can close security gaps faster, protect customer data, and keep your team focused on innovation instead of alert triage.
Ready to stop chasing alerts? Meet your new Digital Security Teammate.

A critical RCE (CVSS 10.0) in n8n exposes automation pipelines and stored secrets to full compromise—upgrade to version 1.36.1 immediately.

Pre-production checks cannot secure a dynamic cloud. Find out how AI bridges the visibility gap between deployment and defense to catch what Shift-Left misses.

A new vulnerability allowed attackers to manipulate Google Gemini into leaking private data simply by embedding malicious text in a calendar invitation.