How Can Automation Handle Tier 1 Security Investigations?
Discover how Digital Security Teammates automate Tier 1 investigations, cutting response times by 45-55% while keeping humans in control of every decision.
Discover how Digital Security Teammates automate Tier 1 investigations, cutting response times by 45-55% while keeping humans in control of every decision.

Tier 1 analysts are often buried under a mountain of repetitive alerts, leading to burnout and missed threats. Automation solves this by instantly triaging, enriching, and validating incidents, acting as an "always-on" teammate that filters out noise so humans can focus on complex investigations.
Imagine walking into a room where a thousand alarms are ringing at once, and your job is to figure out which one actually matters before the building burns down. This is the daily reality for Tier 1 security analysts, who are drowning in a sea of false positives and low-fidelity alerts. The traditional "eyes-on-glass" approach is failing; human analysts simply cannot scale at the speed of modern cyber threats, leading to dangerous fatigue and critical oversights.
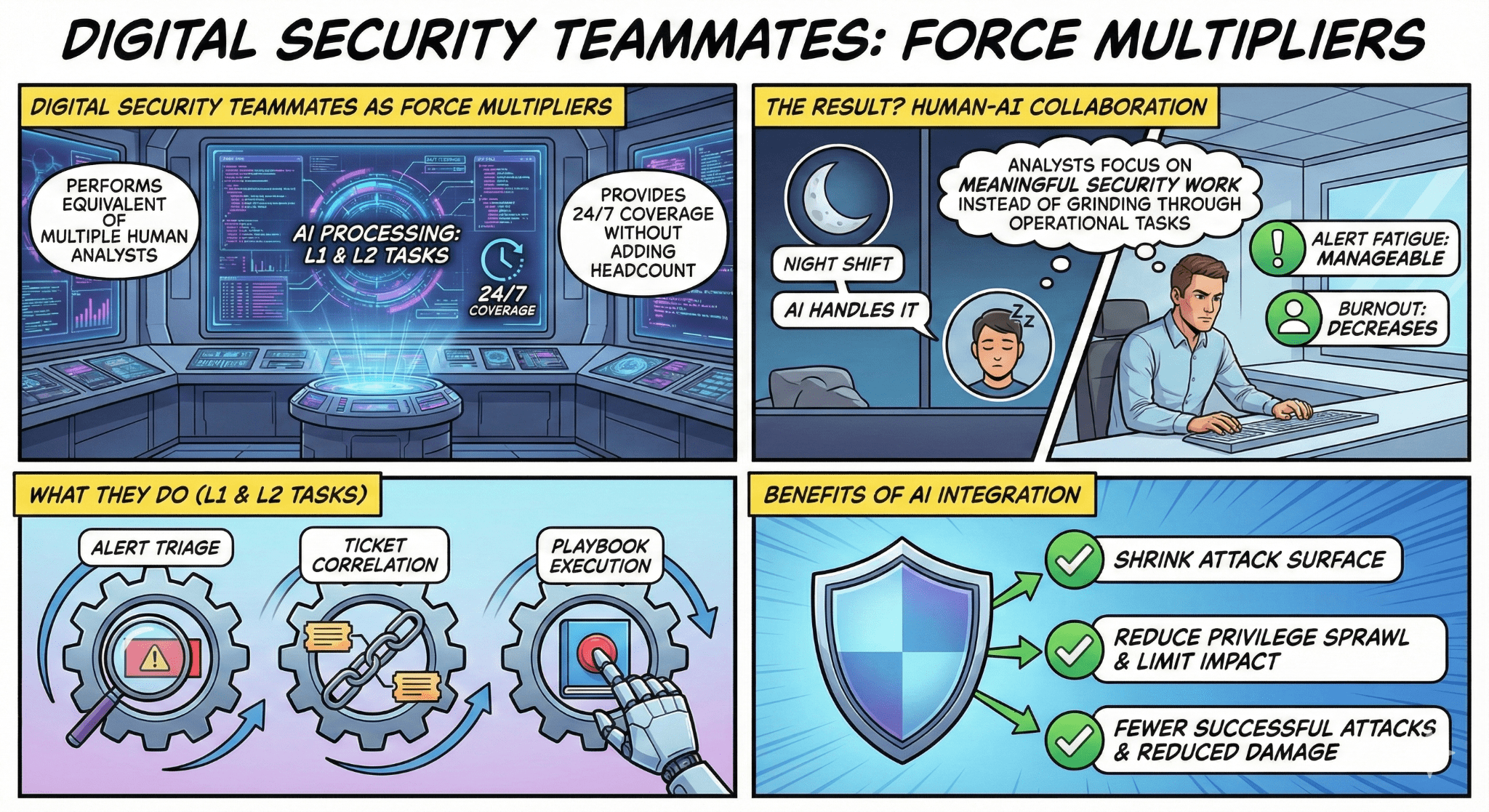
Enter Digital Security Teammates, which is the force multiplier that changes the game from "survival" to "strategy." By delegating the grunt work of data collection and initial triage to machines, organizations can transform their Tier 1 operations from a reactive bottleneck into a proactive defense engine.
It's not about replacing the analyst; it's about augmenting their capabilities so they can focus on what humans do best: strategic thinking and complex investigation, ensuring that when a human does step in, they are armed with answers, not just questions.
SOC automation refers to AI-powered workflows that detect, triage, enrich, and respond to security alerts without requiring manual intervention at every step. These systems follow an automation framework that handles repetitive triage, context gathering, and correlation across tools in seconds rather than hours.
Traditional SOCs struggle with MTTR measured in days. Each incident requires manual investigation, evidence gathering across multiple tools, coordination with different teams, and documentation.
Digital Security Teammates compress this timeline dramatically. By automating evidence collection, correlation, and initial containment actions, response times drop by 45-55% (MTTR reduction), with many incidents resolved in minutes.
Detection speed determines breach impact. Every hour of undetected compromise increases the attacker's advantage and your eventual recovery cost. Traditional SOCs detect threats in hours or days.
Digital Security Teammates monitor continuously, correlate events across your entire security stack in real-time, apply threat intelligence automatically, and identify anomalies based on behavioral baselines rather than signature-based detection.
The average enterprise operates between 60 and 75 security tools. Each tool adds visibility but also friction. Analysts jump between dashboards, each with its own alert logic, severity scale, and data schema. Manual correlation becomes impossible at scale.
SOC automation platforms act as a unified layer across your security stack. Integration with 500+ tools reduces tool sprawl complexity, with organizations reporting significant time savings on management tasks through consolidation.
Analysts waste hours writing complex queries to pull data from SIEMs, EDRs, and other tools. The process is manual, error-prone, and requires deep technical knowledge that junior analysts often lack.
Digital Security Teammates answer questions in plain language; the AI teammate translates natural language into the appropriate queries, searches across connected systems, and returns results. Natural language query interface reduces query complexity, with documented improvements in analyst efficiency. Analysts spend time analyzing results instead of fighting with query syntax.
Compliance audits consume massive analyst time, which includes collecting evidence, generating reports, documenting controls, and proving adherence to frameworks like ISO 27001, SOC 2, PCI DSS, or HIPAA.
Automated compliance workflows can reduce compliance task burden by 60%, with organizations reporting up to 10 hours per week saved and audit cost reductions, and auditors receive complete documentation instead of scattered spreadsheets.
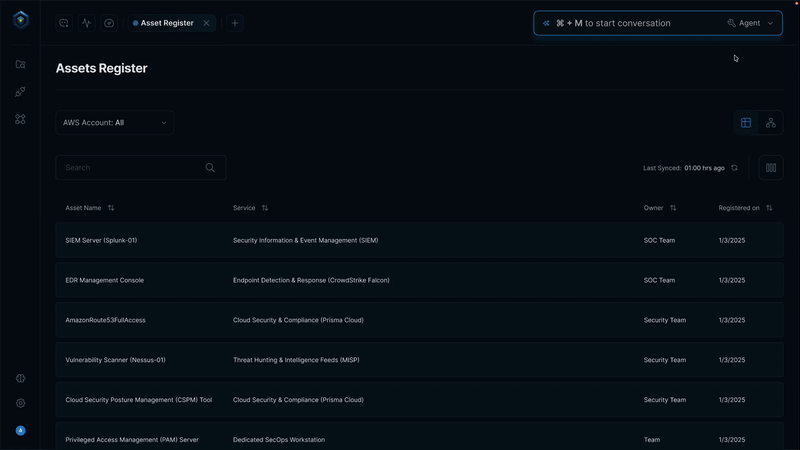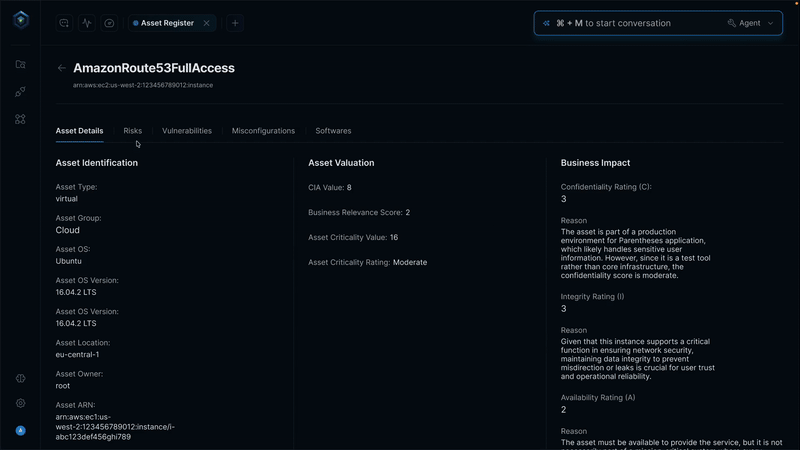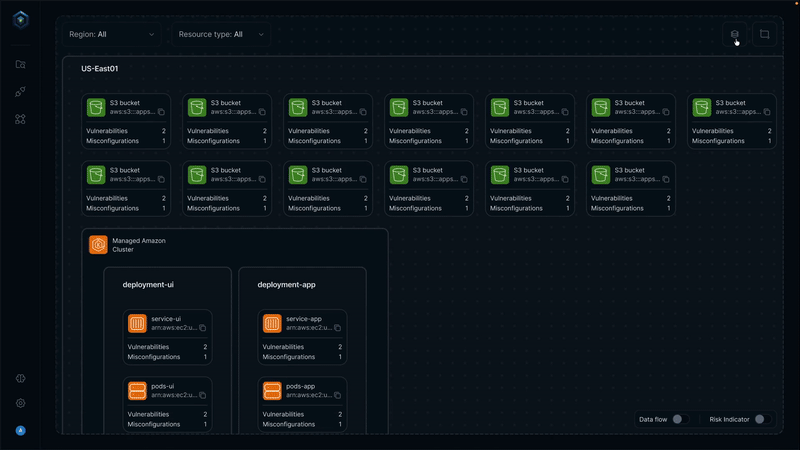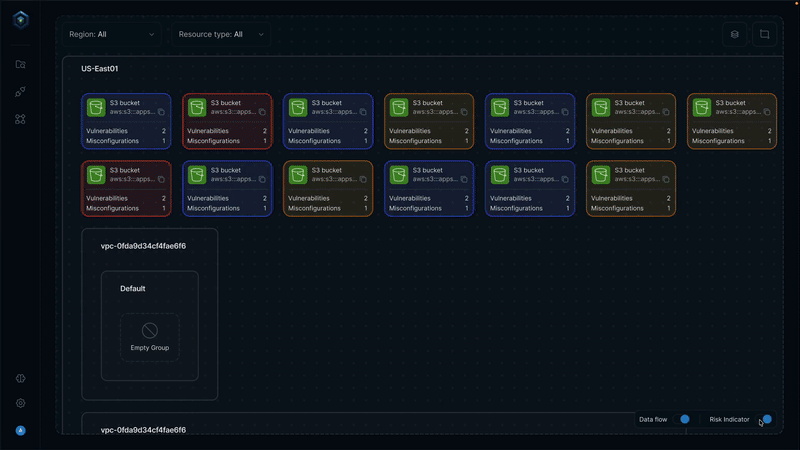
Manual risk assessment struggles with consistency. Different analysts may prioritize the same vulnerability differently based on their judgment, experience level, and current workload.
AI-powered risk assessment applies consistent logic based on blast radius, asset sensitivity, business impact, and ownership. AI-powered risk assessment applies consistent logic, with documented improvements in assessment accuracy (50% improvement) and resource allocation efficiency through better resource allocation.
Traditional security operations have coverage gaps. Shadow IT that never gets inventoried, configuration drift between scans, identity sprawl across cloud services, and overnight monitoring limitations when analysts aren't available.
Continuous, agentless discovery across cloud, SaaS, and endpoints catches shadow IT automatically. Real-time visibility replaces periodic scans. AI teammates monitor 24/7 without fatigue, eliminating the blind spots that attackers exploit.
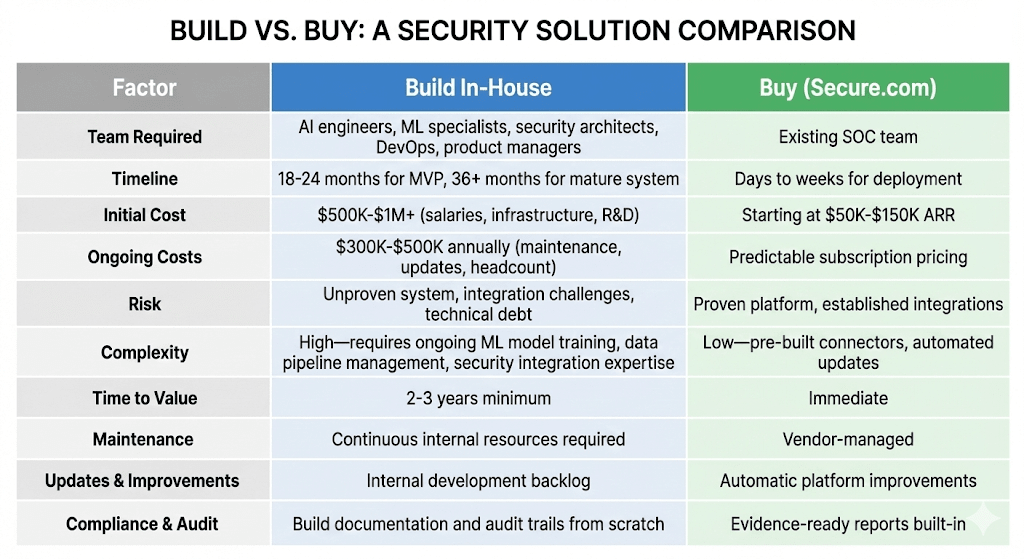
The cost comparison is stark. Hiring additional SOC analysts means salaries averaging $75,000-$100,000 plus benefits, recruitment costs, 6-month ramp time, and ongoing training needs.
Digital Security Teammates can reduce operational costs through automated case handling, with organizations reporting significant cost savings compared to traditional analyst hiring, avoiding 2-3 additional hires to handle alert volume, faster incident resolution that reduces breach impact costs, and compliance audit prep time reduced by 90%.
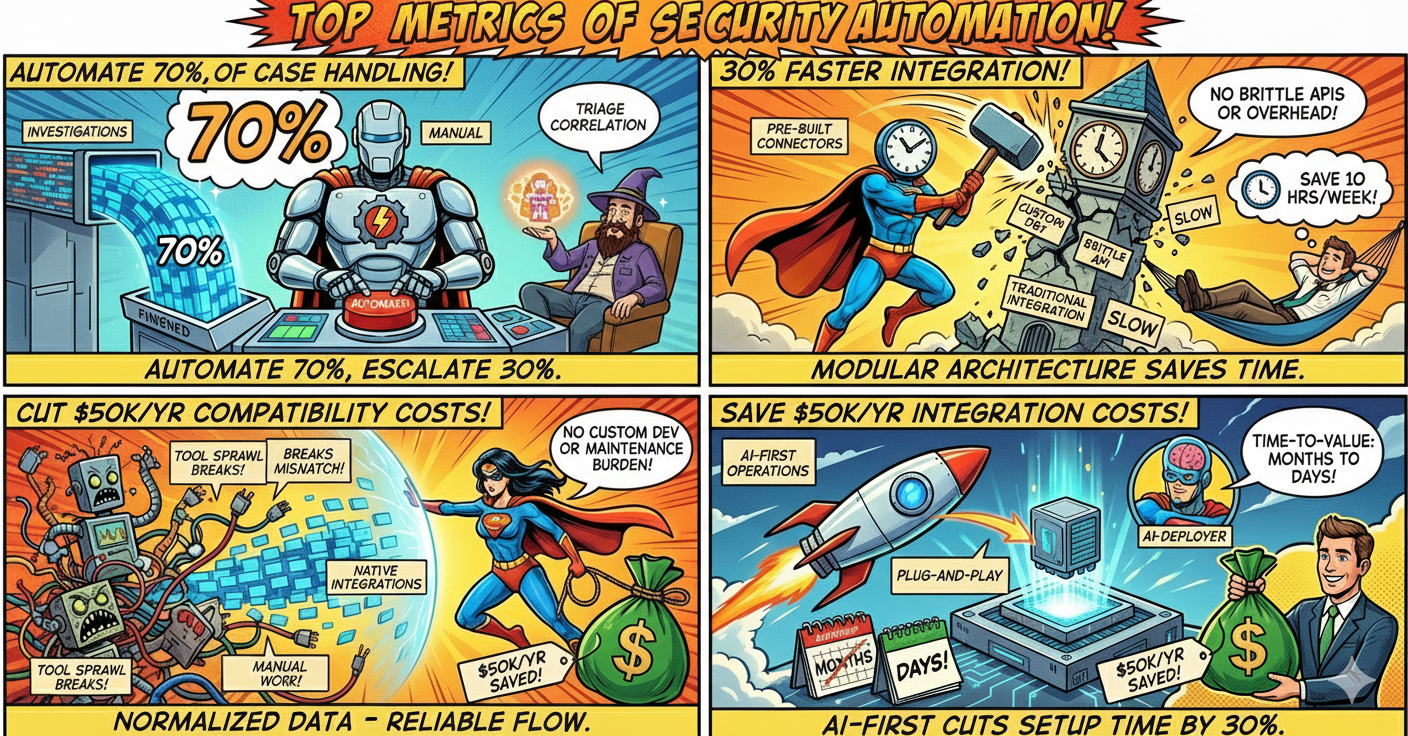
Triage, enrichment, correlation, and prioritization all happen without human intervention. The remaining 30% gets escalated to analysts with complete context and recommended actions already prepared.
500+ integrations with pre-built connectors reduce integration complexity and setup time.
Native integrations and normalized data schemas can significantly reduce compatibility costs through consolidated vendor management by eliminating custom development, reducing maintenance burden, and ensuring reliable data flow.
AI-first architecture with 30-minute deployment reduces time-to-value from months to days. Time-to-value drops from months to days.
Yes, when implemented correctly. Look for platforms with multi-tenant architecture that strictly isolates customer data, end-to-end encryption for data in transit and at rest, immutable audit trails for all AI actions, and SOC2, ISO 27001, or equivalent compliance certifications.
No. Digital Security Teammates augment your team, not replace it. They handle repetitive L1 and L2 tasks—alert triage, evidence gathering, initial correlation—freeing your analysts for work that requires human expertise: complex investigations, threat hunting, and strategic security initiatives.
The SOC headcount crisis isn't resolved. The threat landscape continues to scale. Tool sprawl keeps generating more work, not less. But Digital Security Teammates change the equation. Digital Security Teammates don't eliminate security challenges but they change what's possible. Teams achieve broader coverage and faster response without proportional headcount growth.

Tracking the right cybersecurity metrics transforms security from "we think we're protected" to "we can prove we're reducing risk."

SIEM collects and correlates security data—SOAR automates the response, and together they transform reactive SOCs into proactive defense operations.

The Jordan Effect proves what lean security teams already know: scaling isn't about hiring more analysts—it's about multiplying what your existing team can accomplish.