Understanding SOAR and SIEM Differences in Cybersecurity
SIEM collects and correlates security data—SOAR automates the response, and together they transform reactive SOCs into proactive defense operations.
SIEM collects and correlates security data—SOAR automates the response, and together they transform reactive SOCs into proactive defense operations.

SIEM aggregates and analyzes security data to detect threats, while SOAR automates incident response workflows. Modern SOCs need both—SIEM for detection and visibility, SOAR for automation and orchestration with integration points for threat exposure management, asset discovery, and attack surface intelligence to close the gap between detecting threats and actually stopping them.
Your SIEM just triggered 847 alerts overnight. Three are marked critical. Twelve show high-priority. The rest sits in a queue labeled "investigate when possible." It's 8 AM and your sole SOC analyst starts clicking through alerts, gathering context from five different tools for each one. Twenty minutes per alert. Three hours later, she's cleared 9 alerts—6 turned out to be false positives, meaning only 3 were legitimate threats requiring action.
While she's stuck in manual triage, attackers who compromised a credential at 3 AM have already moved laterally—industry data shows attackers achieve lateral movement in under 60 minutes on average. And it's exactly why Secure.com built Digital Security Teammates to bridge the gap between detection and response. SIEM provides detection. SOAR provides automation. Neither works optimally without the other.
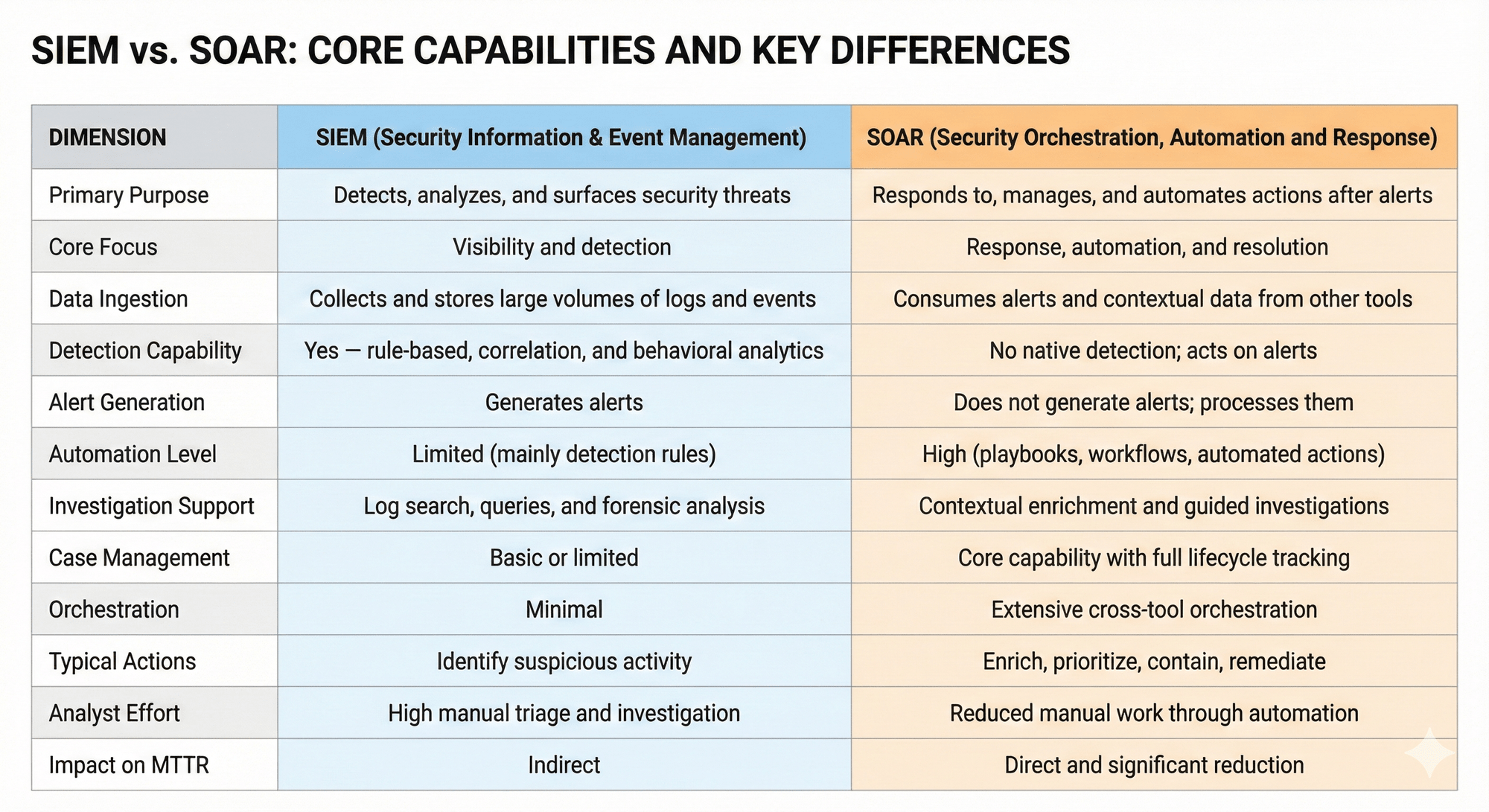
SIEM provides visibility and detection, while SOAR operationalizes response. Together, they form the foundation of effective security operations. Modern security operations are evolving toward AI-native platforms that unify detection, automation, and response.
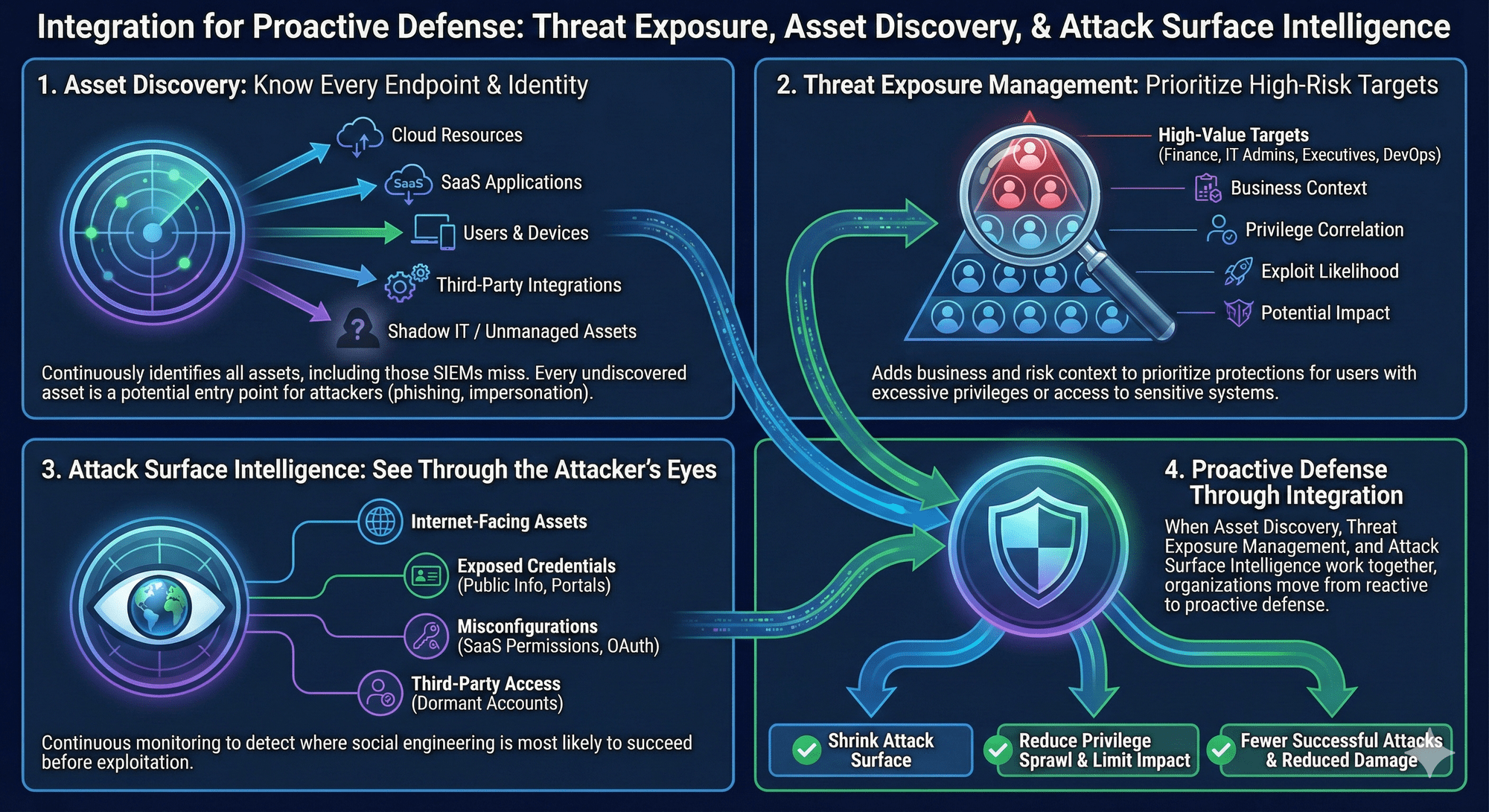
Asset Discovery continuously identifies users, devices, cloud resources, SaaS applications, and third-party integrations including shadow IT and unmanaged assets that traditional SIEM deployments miss. Every undiscovered asset is a potential entry point for attackers using phishing, impersonation, or credential abuse. Without this visibility, organizations leave critical gaps in their defenses.
Threat Exposure Management (TEM) adds business and risk context to your assets correlating identities, privileges, and access paths with exploit likelihood and potential business impact. It highlights which users hold excessive privileges, which credentials access sensitive systems, and which access paths could cause the greatest business impact if compromised. This allows security teams to prioritize protections for high-value targets such as finance, IT admins, DevOps, and executives who are most frequently targeted in social engineering attacks.
Attack Surface Intelligence provides an attacker's-eye view of your organization—continuously mapping internet-facing assets, exposed credentials, misconfigurations, and third-party access that expand your exploitable perimeter. It identifies public employee information, exposed login portals, misconfigured SaaS permissions, dormant accounts, OAuth tokens, and third-party access that expand the human attack surface. Continuous monitoring helps teams detect where social engineering is most likely to succeed before an attacker exploits it.
When Asset Discovery, Threat Exposure Management, and Attack Surface Intelligence work together, organizations move from reactive to proactive defense. Security teams can shrink the attack surface, reduce privilege sprawl, remove unnecessary access, and limit the impact of any compromised identity. The result: fewer successful social engineering attacks and reduced damage when one inevitably occurs.
Yes. TEM integrates via APIs, webhooks, and syslog forwarding.
It ensures all assets are visible, closing blind spots and improving response accuracy.
It provides context for alerts and enables automated remediation actions.
Both are needed for effective security operations. SIEM detects, SOAR automates response. Using one alone leads to alert fatigue or ineffective automation.
SIEM and SOAR aren’t rivals—they work together. Modern SOCs need both to be effective. Detection without context creates noise, automation without insight leads to mistakes, and visibility without intelligence doesn’t improve security. Secure.com's Digital Security Teammates unify detection, contextual intelligence, and automated response for efficient, scalable security operations.

Security posture assessment evaluates your organization's overall cybersecurity strength, identifying vulnerabilities and providing a roadmap to enhance your defense against evolving threats.

A major source code leak exposes how routine age-verification selfies for popular apps are feeding a massive government surveillance and reporting machine.

A severe vulnerability in popular Grandstream desk phones gives attackers root access to listen to calls and pivot into corporate networks—highlighting a major blind spot for small businesses.