Effective Attack Surface Management for Cybersecurity
Learn how modern ASM gives lean security teams full visibility, intelligent prioritization, and real-time defense without enterprise headcount.
Learn how modern ASM gives lean security teams full visibility, intelligent prioritization, and real-time defense without enterprise headcount.

Attack Surface Management (ASM) helps you see and secure everything in your digital environment. It keeps track of cloud systems, external applications, and any assets that attackers could reach. Using automated discovery, smart prioritization, and real-time monitoring, ASM reduces the risk of breaches. Today’s platforms even use AI to map potential attack paths, identify blind spots, and give security teams the insight they need to stay ahead of emerging threats.
Every application deployed, cloud service activated, and API endpoint created expands your organization's attack surface—the sum of all potential entry points adversaries can exploit. As businesses accelerate digital transformation, the attack surface grows faster than traditional security tools can track, creating dangerous blind spots where threats hide undetected.
Attack surface management has evolved from periodic vulnerability scanning to continuous, AI-driven visibility across your entire digital ecosystem. For security teams managing hundreds or thousands of assets across cloud, on-premises, and SaaS environments, effective ASM provides the automated discovery, risk intelligence, and prioritization needed to stay ahead of attackers.
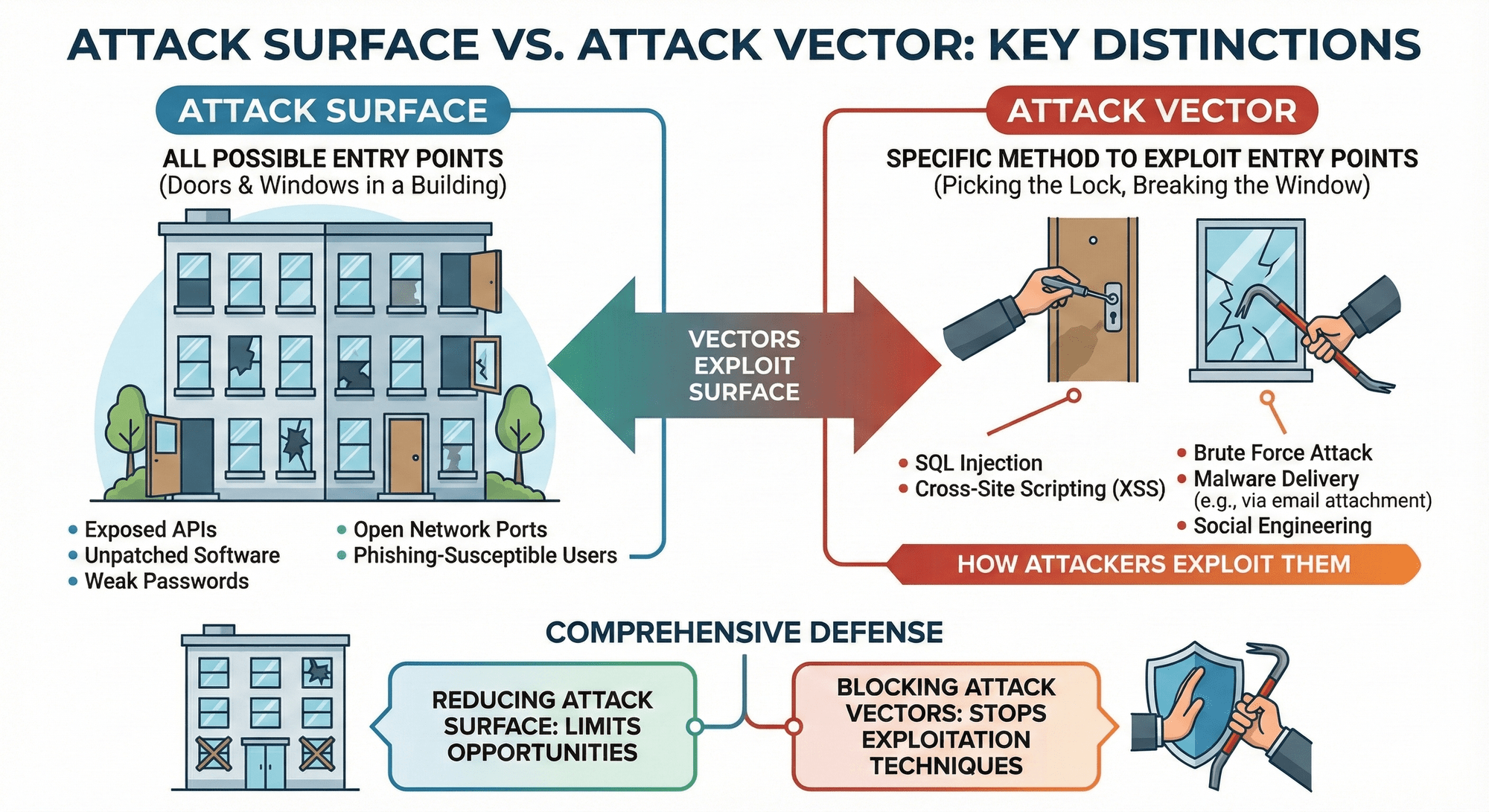
Your attack surface is every place an attacker could try to get into your systems. That includes your digital assets apps, APIs, cloud instances, databases—anything that stores or moves important data. Your physical assets matter too. Laptops, servers, routers, and other devices all create openings that need to be secured.
The attack surface represents all possible entry points, think of it as the doors and windows in a building. An attack vector, by contrast, is the specific method an adversary uses to exploit one of those entry points—the technique for picking the lock or breaking the window.
Understanding both concepts matters for comprehensive defense. You need to know where vulnerabilities exist (surface) and how attackers might exploit them (vectors). For example, an exposed API represents part of your attack surface, while SQL injection is the attack vector that exploits it. Reducing your attack surface limits opportunities, while blocking attack vectors stops specific exploitation techniques.
Cloud environments bring unique visibility challenges that traditional security tools often can’t handle. Resources are spun up and torn down constantly, sometimes without the security team even knowing. Any misconfiguration in IaaS, PaaS, or SaaS setups can leave sensitive data exposed or open doors for unauthorized access.
Cloud providers operate under a shared responsibility model: they secure the infrastructure (physical servers, networks, hypervisors), while you're responsible for securing your applications, configurations, data, identity management, and access controls. Misunderstanding this division creates dangerous security gaps.
Containers and serverless functions present unique visibility challenges due to their ephemeral nature. They're created and destroyed dynamically, often within minutes or seconds. Traditional security tools that rely on periodic scanning miss these short-lived assets entirely, requiring continuous, real-time discovery and monitoring.
Multi-cloud environments require monitoring each platform individually due to varying security configurations and compliance requirements. Knowing who is responsible for what helps keep everything safe.
Modern Attack Surface Management (ASM) goes beyond simply listing assets, it continuously maps and secures your digital environment. The core capabilities of ASM include:
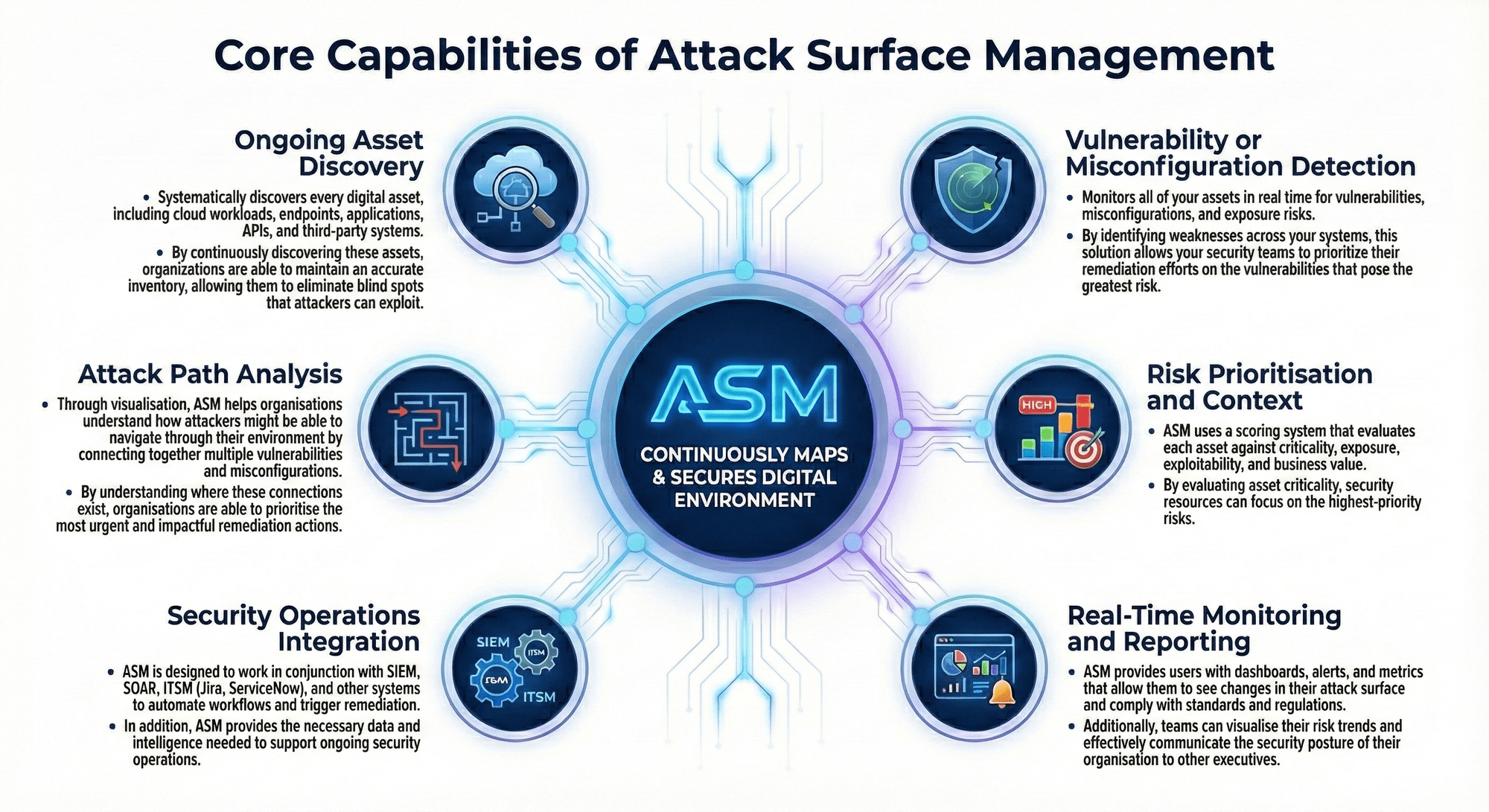
ASM systematically discovers every digital asset, including cloud workloads, endpoints, applications, APIs, and third-party systems. By continuously discovering these assets, organizations are able to maintain an accurate inventory, allowing them to eliminate blind spots that attackers can exploit.
ASM monitors all of your assets in real time for vulnerabilities, misconfigurations, and exposure risks. By identifying weaknesses across your systems, this solution allows your security teams to prioritize their remediation efforts on the vulnerabilities that pose the greatest risk.
Through visualisation, ASM helps organisations understand how attackers might be able to navigate through their environment by connecting together multiple vulnerabilities and misconfigurations. By understanding where these connections exist, organisations are able to prioritise the most urgent and impactful remediation actions.
Not all vulnerabilities or assets pose the same level of risk to your business. ASM uses a scoring system that evaluates each asset against criticality, exposure, exploitability, and business value. By evaluating asset criticality, security resources can focus on the highest-priority risks.
ASM is designed to work in conjunction with SIEM, SOAR, ITSM (Jira, ServiceNow), and other systems to automate workflows and trigger remediation. In addition, ASM provides the necessary data and intelligence needed to support ongoing security operations.
ASM provides users with dashboards, alerts, and metrics that allow them to see changes in their attack surface and comply with standards and regulations. Additionally, teams can visualise their risk trends and effectively communicate the security posture of their organisation to other executives.
Moving past basic CVSS scores means evaluating real-world risk, not just numerical ratings. A good risk assessment asks a few key questions at the same time:
Prioritizing high-value systems, especially internet-facing assets, allows teams to focus limited resources where they have the greatest impact. Smart filtering eliminates distractions by suppressing low-risk issues that do not require immediate attention.
When remediation aligns with business priorities, security becomes a business enabler rather than a cost center. By protecting the things that matter, you reduce your actual risks and do not waste time looking for “perfect security” that negatively impacts the performance of your organisation.
Continuous exposure validation replaces point-in-time assessments with ongoing verification of security posture. Combining ASM with vulnerability management creates comprehensive risk visibility, knowing what assets exist and what weaknesses they contain.
Active threat intelligence feeds provide real-time information about exploitation activity, emerging threats, and adversary campaigns. Attack simulation and red team findings validate whether identified exposures are actually exploitable in your environment. Measuring and reducing mean time to remediation (MTTR) turns exposure data into operational improvement, tracking how quickly security and IT teams eliminate risks after discovery.
Automated Remediation and Response Workflows through No-Code Workflow Automation enable security teams to create automated fixes for routine issues without scripting.
Secure.com's Workflows module provides a drag-and-drop builder with 500+ pre-built integrations, allowing teams to orchestrate remediation across their entire security stack, from alert triage to ticket creation to automated patching, with every action immutably logged for audit compliance.
Integrations with existing tools, such as Jira or ServiceNow, enable organizations to automatically create and assign tasks to appropriate teams.
Updates and critical patches can be automatically applied when immediate corrective action is required, significantly reducing time, effort, and human error.
Continuous monitoring detects configuration drift when systems deviate from secure baselines, and can automatically revert them to last known-good configurations, preventing security degradation over time.
Additionally, policies enforced across all cloud environments ensure that new resources are secure by default, preventing future vulnerabilities.
Tracking asset coverage percentage shows what portion of your infrastructure the ASM platform successfully monitors. Unknown asset discovery rate measures how many previously invisible assets the system identifies, indicating shadow IT prevalence and discovery effectiveness.
Mean time to remediation (MTTR) measures how quickly issues are resolved after detection. Faster remediation improves security posture. Discovering shadow IT and remediating exposures validates policy effectiveness. Audit readiness demonstrates compliance adherence. Preventing incidents through proactive remediation demonstrates measurable ROI.
Modern attack surface management isn’t just a tool you turn on—it’s a structured approach that combines continuous discovery, smart prioritization, and coordinated remediation. Here’s how organizations can put it into practice effectively:
Begin by mapping every asset across your environment—cloud, on-prem, SaaS, APIs, shadow IT, third-party integrations, and identities. The goal is to build a living inventory that updates automatically as new resources appear or old ones disappear.
Once assets are discovered, label them by type, owner, business function, and criticality. Context makes it easier to understand which exposures actually matter, instead of treating every issue the same.
Use attack surface intelligence to focus on exposures that are exploitable, business-critical, and likely to be targeted. This helps teams avoid wasting time on low-impact issues and concentrate on what truly reduces breach risk.
ASM works best when connected to your SIEM, IAM, CMDB, vulnerability scanners, cloud platforms, and workflow systems. Integration makes detection faster and remediation smoother.
Set up automated playbooks for common issues—misconfigurations, expired certificates, exposed assets, or over-privileged accounts. Human review can remain for high-risk decisions, but automation should handle routine fixes.
Assign asset owners, define escalation paths, and establish timelines for remediation. Clear accountability prevents exposures from lingering unnoticed.
Track metrics like MTTR, number of high-risk exposures, shadow IT trends, and cloud misconfigurations over time. These insights show whether your security posture is improving and where gaps still exist.
As your business adopts new cloud services, APIs, or tools, regularly update ASM rules, integrations, and workflows. A modern ASM program is never “done”—it grows with the organization.
Vulnerability management identifies weaknesses in known assets, while attack surface management first discovers all assets—including unknown ones—across your entire digital footprint, then assesses vulnerabilities within that complete inventory. ASM provides the "what do we have" foundation that vulnerability management needs to be effective.
ASM continuously monitors cloud infrastructure through API integrations with AWS, Azure, and GCP, automatically discovering resources as they're provisioned. It detects misconfigurations against security baselines (CIS, NIST), identifies exposed services, and tracks configuration drift in real-time, providing visibility that manual audits and periodic scans cannot achieve in dynamic cloud environments.
External ASM provides an attacker's perspective by continuously scanning your internet-facing assets, domains, IP addresses, web applications, APIs, and exposed services. Internal ASM maps assets within your network, tracking lateral movement paths, privilege escalation risks.
Modern attack surfaces require continuous monitoring, not periodic scans. In cloud-native environments, assets are created and modified constantly—weekly or monthly scans leave dangerous gaps. Effective ASM platforms provide real-time discovery and 24/7 monitoring to catch new exposures immediately.
Yes, with AI-driven ASM platforms designed for lean teams. Modern solutions automate asset discovery, provide intelligent risk prioritization, and offer no-code remediation workflows—enabling small teams to achieve coverage that previously required large security operations centers.
Leading ASM platforms integrate with SIEM systems, vulnerability scanners, cloud security posture management (CSPM) tools, ticketing systems, and identity providers. This creates a unified security ecosystem where asset intelligence flows automatically to inform threat detection, response, and remediation.
Attack path analysis maps how adversaries could chain exploits—combining vulnerabilities, misconfigurations, excessive IAM permissions, and network access—to reach crown jewel assets. By visualizing these multi-stage attack scenarios, security teams can identify chokepoints where a single remediation breaks multiple attack chains, maximizing the impact of limited resources.
Attack surface intelligence focuses on your environment: your assets, their criticality, ownership, vulnerabilities, and how they’re connected. Threat intelligence, on the other hand, provides insights into attacker tactics, campaigns, and indicators of compromise. When you combine the two, you get contextual risk scoring: for example, “This vulnerability exists on a critical, internet-facing system, and it’s currently being exploited in the wild,” helping teams act smarter and faster.
Implementing ASM allows you to reduce risk proactively, identifying and remediating exposures before attackers exploit them, shifting from reactive incident response to preventive security.
Continuous asset discovery, intelligent prioritization, and automated remediation provide your company with the visibility and control to protect your digital ecosystem, no matter how small or under-resourced your security team may be.
The most successful ASM implementations treat attack surface visibility as a foundational capability, not a standalone tool. Secure.com's unified platform combines asset discovery, vulnerability management, attack path analysis, and automated remediation into a single command center, giving security teams complete visibility and control without tool sprawl.
By integrating ASM with SIEM, case management, and compliance workflows, Digital Security Teammates enable lean teams to focus on protecting what matters most: the assets attackers actually target.

Tracking the right cybersecurity metrics transforms security from "we think we're protected" to "we can prove we're reducing risk."

Discover how Digital Security Teammates automate Tier 1 investigations, cutting response times by 45-55% while keeping humans in control of every decision.

SIEM collects and correlates security data—SOAR automates the response, and together they transform reactive SOCs into proactive defense operations.