RBAC vs IAM: The Definitive Guide to Modern Access Governance
Find the critical distinction between IAM (the 'Who') and RBAC (the 'What') to streamline compliance, automate user lifecycles, and secure your organization against modern threats.
Find the critical distinction between IAM (the 'Who') and RBAC (the 'What') to streamline compliance, automate user lifecycles, and secure your organization against modern threats.

Firewalls are no longer effective in establishing security perimeters today; identity is now the key factor. Today, every data breach costs an average of $4.88 million, but organizations can’t afford to have weak access controls or monitoring on their information because they need to know who is coming into their cyberspace (IAM) and what they do in there (RBAC).
In order to move effectively through the complicated cybersecurity terrain, it is important for someone to make a differentiation between the broad structure of governance and particular enforcement engines. This differentiation forms the basis of the argument in RBAC as opposed IAM. Although these terms are used interchangeably a lot in casual talk, they refer to different levels within security stack.
| Feature / Dimension | RBAC (Role-Based Access Control) | IAM (Identity & Access Management) |
|---|---|---|
| Primary Focus | Authorization (The “What”). Managing permissions based on roles. | Holistic Identity Governance (The “Who”). Managing the full lifecycle of identities. |
| Scope | Narrow: A specific mechanism for access control. | Broad: A framework including RBAC, SSO, MFA, Auditing, and Governance. |
| Key Question Answered | “What is this user allowed to do?” | “Is this user who they say they are, and should they have access?” |
| Granularity | Coarse-grained (typically). Access is binary based on role assignment. | Variable. Can manage coarse roles or fine-grained attributes depending on the solution. |
| Management Unit | Roles and Permissions. | Users, Identities, Credentials, and Policies. |
| Dynamic Capability | Generally static. Permissions are pre-defined. | Dynamic. Can enforce conditional access (e.g., “MFA required if off-network”). |
| Implementation | Defined within applications or Directory groups. | Implemented as a centralized platform (e.g., Okta, Azure Entra ID). |
| Primary Benefit | Operational efficiency in permission assignment. | Security consistency, compliance, and lifecycle automation. |
| Relationship | A component/subset of IAM. | The umbrella framework that utilizes RBAC. |
RBAC is a specific access control mechanism, which is a strategy employed within the broader IAM framework. RBAC simplifies the complex administration of permissions by associating them with roles (e.g., "Nurse," "Financial Analyst," "DevOps Engineer") rather than assigning privileges directly to individual users. In this model, a user acquires permissions only by being assigned a role, and that role is defined by a specific set of operations it can perform on specific objects.
In a non-RBAC environment, onboarding a new employee involves a tedious checklist of individual permissions: "Give Alice read access to Folder X, write access to Database Y, and login access to App Z." With RBAC, the administrator simply assigns Alice the "Marketing Specialist" role. The system automatically provides the thousands of underlying discrete permissions.
Organizations make certain that a user can only have access of what is strictly necessary for his work by assigning roles that follow job descriptions to the letter. This helps to contain breaches. In the event that there is compromise on a user’s login details, then the hacker will be limited by the confines of the specific role assigned to that user and not have free reign in the entire system.
Various data protection regulations such as GDPR, HIPAA, and SOX require organizations to implement access controls on sensitive data. RBAC provides a structured audit trail by documenting role assignments and permission changes, making compliance audits more efficient.
Rather than checking what each user is allowed to do, it is possible for auditors to analyze the rights given to specific roles and see if they are assigned to users for those roles.
For example, in the healthcare sector, RBAC enables organizations to enforce that billing clerks cannot access clinical notes, and such segregation is very important when trying to comply with HIPAA.
As organizations scale, managing user permissions individually becomes operationally infeasible and introduces significant security risk. This is achieved through RBAC where users are separated from having certain permissions, thereby enabling linear scaling of the system. It takes a few simple steps like giving out predefined roles to one thousand additional employees as opposed to setting up thousand different permission packages.
This happens when companies create overly specific roles. For instance, developing "Nurse - ER - Night Shift - Level 3" rather than just "Nurse" with some context attributes. After some years, there may be 4,000 different roles instead of the 5,000 administrative advantages for an organization with about 5,000 employees.
A user might transfer from Finance to HR but retain their Finance role permissions due to inadequate joiner-mover-leaver (JML) processes, creating toxic combinations that violate segregation of duties principles. This accumulation creates toxic combinations that can facilitate fraud or data exfiltration. Identity governance and administration (IGA) platforms with SoD violation detection capabilities are required to identify these toxic combinations automatically.
The conventional RBAC is static. It states, "Managers can see this document." Nevertheless, it does not commonly consider the following context questions: “Has the Manager logged in using an expected device? What about 3:00 AM on Monday? Is it located within a problematic geopolitical area?” This kind of contextual blindness poses one of the greatest challenges of implementing zero trust with the RBAC of today.
Role: Doctor. Permission: Read/Write Patient Charts, Prescribe Medication.
Restriction: Cannot access Billing Records.
Role: Nurse.
Permission: Read/Update Patient Vitals, Administer Meds.
Restriction: Cannot Prescribe Meds.
Role: Medical Biller.
Permission: Access Billing Records, View Insurance Data.
Restriction: Cannot View Clinical Notes (Diagnosis details).
EHR systems like Epic or Cerner implement RBAC to enforce segregation of duties, ensuring billing staff cannot access or modify clinical data such as medication orders. This prevents both accidental errors and intentional fraud. The access control is enforced at the application layer through UI restrictions and API-level authorization checks.
IAM (Identity and Access Management) is the comprehensive framework of policies, processes, and technologies for managing digital identities throughout their lifecycle. It includes various components like policies, procedures, and technology all of which are geared towards making sure that only authorized persons can enter specific areas within a given time and for a proper reason. Identity and Access Management (IAM) seeks to establish if a user is legitimate and track the continuous usage of granted access.
With IAM centralization, security policies can be uniformly applied. For example, in case there is a breach or vulnerability found, the admin can enforce multi-factor authentication or change all users’ passwords at once.
While security is often perceived as creating friction, well-designed IAM actually improves user experience through capabilities like Single Sign-On (SSO), adaptive authentication, and self-service password management. SSO (Single Sign-On) reduces authentication friction by allowing users to access multiple applications with a single set of credentials.
Self-service capabilities like password reset and account unlock reduce helpdesk burden while improving user productivity. Automated provisioning enables immediate access to required resources, reducing time-to-productivity from days to hours and improving new hire experience.
Password reset requests typically account for 20-30% of helpdesk tickets. Self-service password reset (SSPR) capabilities can reduce helpdesk costs by $10-20 per incident while improving user satisfaction and reducing resolution time from hours to minutes.
Organizations often have a "spaghetti" architecture of legacy on-premises applications, modern SaaS tools, and shadow IT. Integrating these disparate systems into a unified IAM framework is a massive engineering challenge.
If the HR system has inconsistent job titles or missing department codes, the IAM system cannot accurately assign roles. "Garbage in, garbage out" leads to users having incorrect access, which frustrates employees and creates security gaps.
Successful IAM implementation requires cross-functional alignment between HR, IT, Security, and business stakeholders. Common challenges include resistance to centralized access governance, perceived productivity impacts from security controls (e.g., MFA), and competing priorities. Executive sponsorship and clear communication of business benefits are critical success factors.
The question "Can you use both?" is slightly misleading; in a mature enterprise, you must use both. They are not mutually exclusive alternatives, but rather layers of the same stack.
It authenticates the user via SSO and MFA, and then queries the directory to find the user's attributes (Department: Sales, Title: Manager).
RBAC as the Map: Based on those attributes, the IAM system assigns the user to specific logical groups or roles (e.g., "Sales_Manager_Role").
Application Enforcement: When the user tries to access a CRM application, the application checks the user's role. The RBAC policy within the application says, "Sales_Manager_Role allows 'View_Revenue_Reports'."
Feedback Loop: The IAM system monitors this access. If the user behaves anomalously (e.g., downloading 5,000 reports in an hour), the IAM system might trigger a "step-up authentication" or revoke the session, effectively overriding the static RBAC permission.
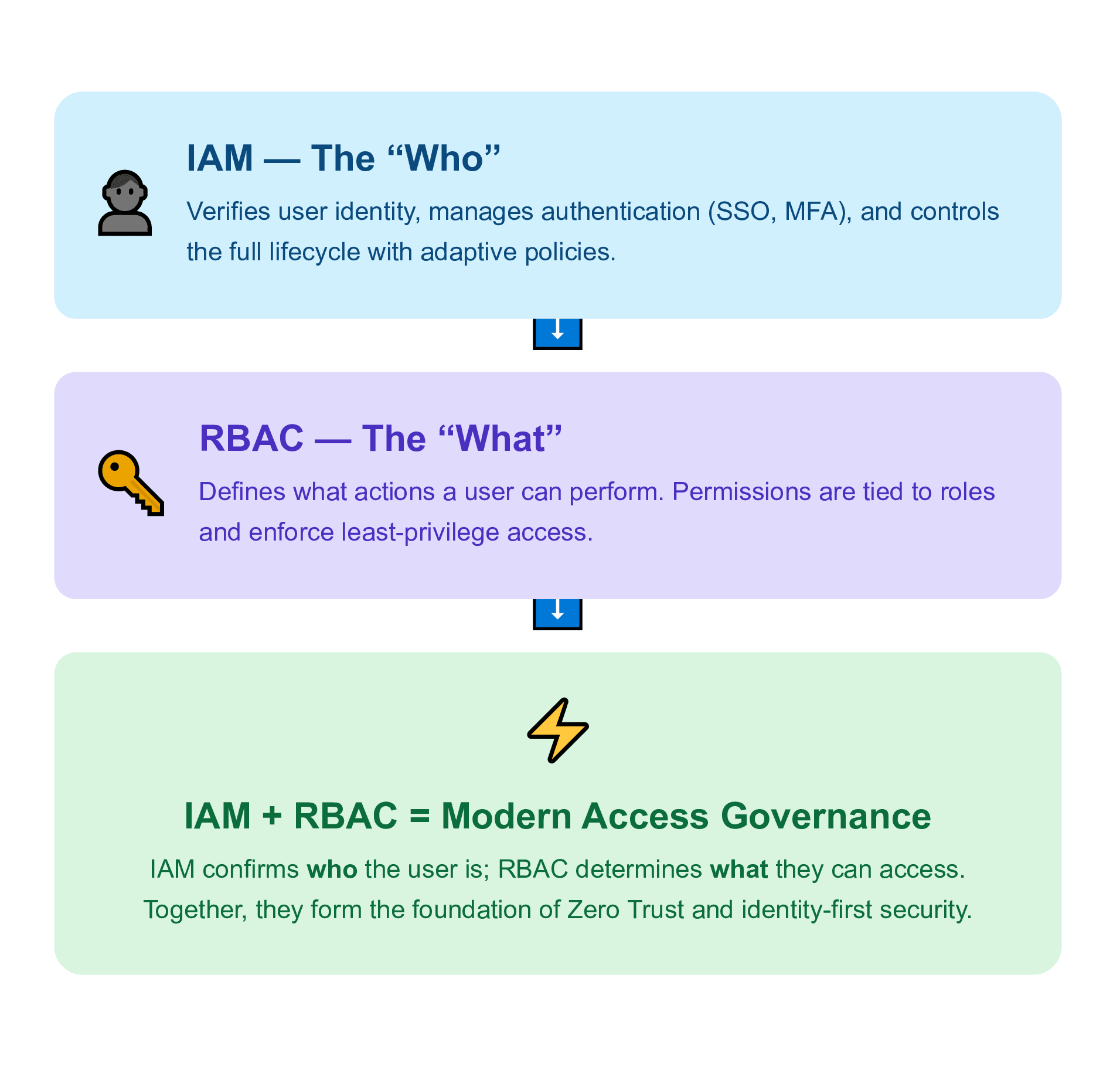
RBAC (Role-Based Access Control) is a security method where access to computer resources is restricted based on the role a user holds within an organization. Instead of giving permission to "Alice," you give permission to the "Manager" role and then assign Alice to that role.
IAM (Identity and Access Management) is the overarching framework of business processes, policies, and technologies that facilitate the management of electronic identities. It ensures that the right people have the right access to the right resources at the right time.
Yes, absolutely. They are complementary. IAM manages the user's identity (logging in, MFA), while RBAC manages what the user can do once the user is logged in. Most modern IAM platforms (like Azure Active Directory or Okta) use RBAC as their primary method of enforcing access rights.
RBAC is vital because it enforces the "Principle of Least Privilege." It limits users to only the access they need to do their jobs, reducing the potential damage from insider threats or compromised credentials. It also simplifies the auditing process for regulations like GDPR and HIPAA.
The structural logic of permissions in RBAC can be described as the "what" and "how" of access, while IAM offers identity governance in totality, answering the questions "who" and "when".
Any organization that wants to protect its resources from cyber attacks must commit itself to securing these things in pairs. As traditional network perimeters dissolve in cloud and remote work environments, organizational security increasingly depends on robust identity governance rather than perimeter defenses.
Identity has become the new security perimeter. The integration of RBAC within a mature IAM strategy is the only viable path to achieving the resilience required in the modern threat landscape.
A high-severity VMware vulnerability is being exploited in the wild and federal agencies have less than three weeks to fix it.
Shadow IT is growing fast — here are 10 proven strategies to find it, manage it, and stop it from becoming a security nightmare.

Your security stack isn't failing because you have too few tools; it's failing because too many of them are working against each other.