Enhance Security with Effective IT Asset Discovery
With 40% of data breaches involving assets spread across multiple environments and costing over $5 million to remediate, knowing exactly what's in your IT environment isn't optional anymore.
With 40% of data breaches involving assets spread across multiple environments and costing over $5 million to remediate, knowing exactly what's in your IT environment isn't optional anymore.

Without proper Asset Discovery, organizations risk unknown devices, compliance issues, and a larger attack surface. While Active Discovery asks devices directly for information, Passive Discovery monitors network traffic without directly interacting with devices, and agentless methods use APIs, network protocols, and hypervisor integration to collect data. A well-planned Asset Discovery program helps organizations maintain security, stay compliant, and respond to issues faster.
A Fortune 500 healthcare provider discovered 847 cloud applications in use, but IT had approved only 42. The remaining 805 represented shadow IT, each one a potential compliance violation and security risk. This discovery came not from a data breach, but from implementing automated Asset Discovery.
The bottom line is you can't protect what you don't know exists. As organizations move to the cloud, support remote work, and use IoT devices, traditional asset spreadsheets are no longer enough. Modern attack surfaces grow every day, yet Gartner finds that 30% of critical assets often go undiscovered.
Asset discovery takes the guesswork out of security. By continuously identifying and tracking every device, application, cloud instance, and network endpoint, organizations get clear visibility to manage vulnerabilities, stay compliant, and shrink their attack surface.
Asset Discovery is the automated process of identifying, cataloging, and continuously monitoring every digital resource in your IT environment. Think of it as taking inventory, but instead of counting boxes in a warehouse, you're tracking servers, laptops, cloud instances, applications, IoT devices, and everything else connected to your network.
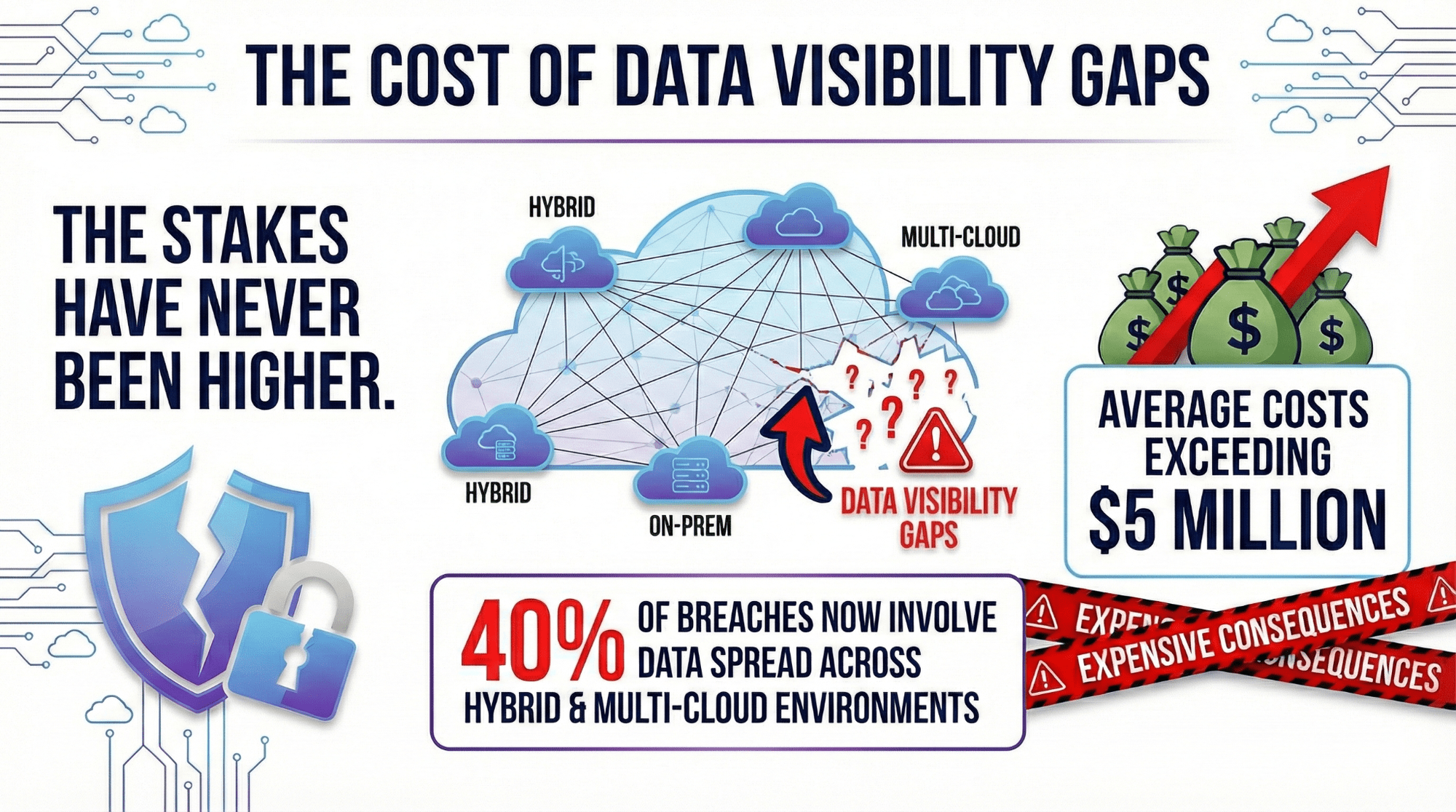
The stakes have never been higher. Data visibility gaps are proving expensive as 40% of breaches now involve data spread across hybrid and multi-cloud environments, with average costs exceeding $5 million.
The complexity of tracking assets across these fragmented environments extends breach lifecycles to an average of 283 days. Every undiscovered asset represents a potential entry point that attackers can exploit before your security team detects the threat.
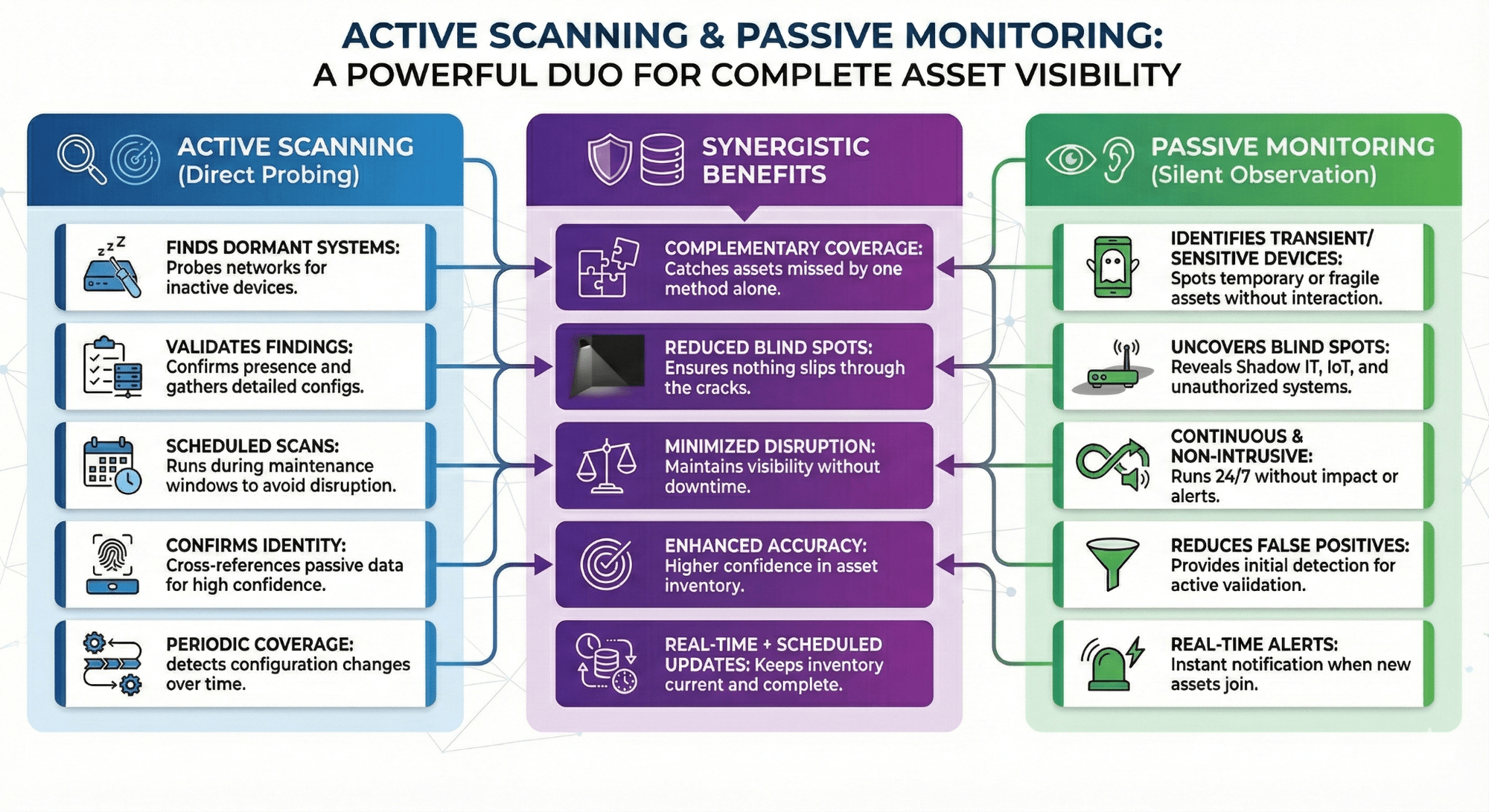
When it comes to finding all your assets, there are two main approaches: active and passive discovery.
Active Discovery scans devices and systems on your network using protocols to gather detailed configuration and state information. This method is fast, identifies all devices quickly and thoroughly, and is unlikely to miss anything. However, sometimes it may slow down the network or trigger alerts.
Passive Discovery monitors network traffic and does not directly interact with devices. It monitors ongoing communication patterns and provides real-time visibility without slowing down operations or performance. On the downside, it may not detect devices that are powered off or not on the network.
See Also - Active vs. Passive Asset Discovery
Generally, organizations use both approaches. Passive Discovery runs continuously to detect and capture all changes as they occur. Scheduled Active Discovery scans can submit evidence for verification of all devices, even those that are silent or hiding. The combination of these approaches provides comprehensive views of your IT environment and reduces blind spots, ultimately enhancing your security posture.
Traditional network scans can't provide adequate visibility. Organizations rely on various SaaS applications, multi-cloud infrastructure, containerization, serverless workloads, and connected devices, all of which can move quickly, be temporary, or not amenable to installing a traditional agent.
It helps identify all cloud applications in use, including unsanctioned "shadow IT," ensuring every application is monitored for security and compliance risks.
It leverages APIs from providers such as AWS, Azure, and GCP to continuously track virtual machines, containers, serverless functions, and other cloud services. This approach ensures dynamic environments are always accounted for, even when resources are spun up or decommissioned within minutes.
It monitors assets without requiring software installation. Using network protocols, hypervisor integration, and cloud-native APIs, it efficiently collects data from devices and services that are difficult or impossible to reach with agents.
The aforementioned specialized methods provide the foundation for continuous, accurate visibility into an organization's entire IT environment. These discoveries enable organizations to be more proactive in managing vulnerabilities, reducing their attack surface, providing evidence for compliance, and allowing their security teams to focus on high-value risk mitigation rather than guessing the presence of assets within their IT environment.
Asset Discovery gives you visibility, but the real security benefit comes from acting on that information. Knowing what assets exist isn't enough; you need a clear strategy to reduce your attack surface and strengthen security across your organization.
Begin by identifying every device, application, cloud instance, and network endpoint. Active scanning, passive monitoring, SaaS discovery, and agentless methods are all ways to enhance your confidence that nothing is overlooked. By maintaining an accurate, up-to-date inventory, you can improve vulnerability management and risk prioritization.
Asset Discovery shouldn't exist in isolation. Send discovery data into your attack surface tools, vulnerability scanners, CMDB, and incident response systems so security teams always know what's exposed, what needs scanning, and what's impacted during an incident.
Solutions like Secure.com demonstrate integrated asset discovery through agentless methods and a unified knowledge graph. Organizations can deploy and begin discovering assets within 30 minutes, with continuous discovery providing real-time visibility across cloud resources, SaaS applications, and on-premises infrastructure.
This reduces manual inventory work by 90% (saving 176+ hours per month) and enables contextual risk prioritization. When Asset Discovery feeds directly into automated security operations, teams shift from tracking spreadsheets to actually preventing threats.
Your environment changes constantly: new devices appear, configurations drift, and cloud resources spin up and down. Continuous monitoring gives real-time visibility, while scheduled scans catch hidden or inactive assets. Set alerts for rogue devices and automate investigation and cleanup.
Use your inventory to remove unnecessary risk: harden or retire internet-facing systems, decommission outdated or unpatched software, remove unused accounts and services, and eliminate shadow IT or abandoned cloud instances.
Track each asset from Discovery to decommissioning: Identify it > classify it > apply security baselines > monitor for changes > securely remove it at end-of-life.
What is the difference between Active and Passive Asset Discovery?
Active Discovery scans devices directly to gather detailed information, but it can sometimes impact network performance. Passive Discovery quietly watches network traffic for real-time visibility, yet it may miss inactive devices. Most teams use both passive monitoring for constant awareness and active scans for deeper, scheduled checks.
How often should Asset Discovery scans be performed?
Scan frequency depends on environment dynamics: • Highly dynamic cloud environments: Every 5-15 minutes • Hybrid cloud and on-premises: Continuous passive monitoring + daily active scans • Stable on-premises environments: Weekly scans • Static environments with minimal change: Monthly scans Most organizations benefit from continuous passive monitoring combined with scheduled active scans.
Can Asset Discovery tools identify IoT and other non-traditional endpoints?
Yes. Modern Asset Discovery tools can spot IoT devices, operational technology (OT) systems, and innovative building equipment by watching network traffic, actively scanning, and recognizing device behavior. Companies with lots of IoT devices should use platforms that specifically support IoT and OT environments.
Is Asset Discovery required for compliance frameworks like NIST, PCI DSS, or HIPAA?
Yes. Accurate, up-to-date asset inventories are required for major frameworks. NIST CSF emphasizes asset management (ID.AM category), PCI DSS requires maintaining an inventory of system components (Requirement 2.4), and HIPAA mandates tracking systems that store, process, or transmit ePHI. Automated Discovery ensures continuous compliance and provides auditors with clear evidence.
Asset discovery provides the foundation for effective security by delivering complete visibility into your IT environment. By continuously identifying and tracking all devices, applications, and cloud resources, organizations can proactively manage vulnerabilities, maintain compliance, and reduce their attack surface before threats materialize.
Organizations that implement comprehensive asset discovery programs experience measurable improvements:
However, visibility alone isn't sufficient. Asset discovery delivers maximum value when integrated with vulnerability remediation, security hardening, and continuous risk monitoring, transforming inventory into actionable security outcomes. You can't protect what you can't see, and this is why comprehensive asset discovery is the essential first step in building a resilient security posture.

Half of all SIEM detection failures stem from log collection problems—here's how to fix them and improve your threat detection.

Learn the four phases of the incident response life cycle and discover proven best practices that help security teams detect, contain, and recover from cyber threats faster.

Palo Alto Networks has patched two denial-of-service vulnerabilities in PAN-OS that let unauthenticated attackers knock firewalls offline — no credentials required.