Active vs. Passive Asset Discovery: Finding What's Really on Your Network
Learn why combining active scanning with passive traffic monitoring is the only way to close visibility gaps before attackers exploit them.
Learn why combining active scanning with passive traffic monitoring is the only way to close visibility gaps before attackers exploit them.

Active discovery scans your network directly to find devices and gather detailed configuration data. Passive discovery listens to network traffic to detect assets without generating additional load. Neither method alone provides complete visibility—65% of connected assets fall outside traditional IT tracking.
The hybrid approach combines both: active scans find dormant assets and provide deep intelligence for compliance, while passive monitoring delivers real-time detection of new devices. Organizations using unified platforms like Secure.com reduce manual asset tracking by 80%+ while maintaining continuous, accurate inventories across on-premises, cloud, and hybrid environments. While maintaining continuous, accurate inventories across on-prem, cloud, and hybrid environments.
Last Tuesday, your CISO asked a simple question: "How many devices are on our network right now?"
Three different spreadsheets later, you still don't have an answer. One list says 847 devices. Another claims 1,203. The firewall logs show traffic from 1,890 endpoints. Nobody knows which one is right.
This isn't incompetence—it's how most organizations operate. According to a 2024 Gartner report, only 17% of organizations can accurately identify 95% or more of their assets. Meanwhile, recent research analyzing over 10 million devices across 700 organizations found that 65% of connected assets fall completely outside traditional IT visibility.
Between shadow IT, IoT gadgets, and forgotten lab devices, your network holds more than anyone realizes. The 2025 Verizon Data Breach Report drives this home: 20% of confirmed breaches started with exploited device vulnerabilities on assets that teams didn't even know existed.
Asset discovery isn't just about keeping neat records. It's about knowing what's actually out there before attackers do. Active vs. passive asset discovery represents two fundamentally different approaches to uncovering devices—and understanding both is critical to maintaining control over an environment that changes every single day.
Asset discovery automatically identifies and catalogs every device, virtual machine, or application running across your network. Endpoints, servers, IoT devices, cloud instances—all of it.
Without accurate discovery, you're flying blind:
According to Ivanti's 2025 research, 55% of organizations struggle with siloed IT and security data, making it nearly impossible to identify and prioritize exposures. Another 51% admit to running end-of-life software they can't even properly inventory.
You can't protect what you can't see. That's why choosing the right discovery approach—or more accurately, the right combination of approaches—determines whether you're managing your network or just reacting to surprises.
For organizations still tracking assets manually, the reality is even worse. The hidden costs of spreadsheet-based asset tracking compound daily as networks evolve faster than humans can keep up Excel updates.
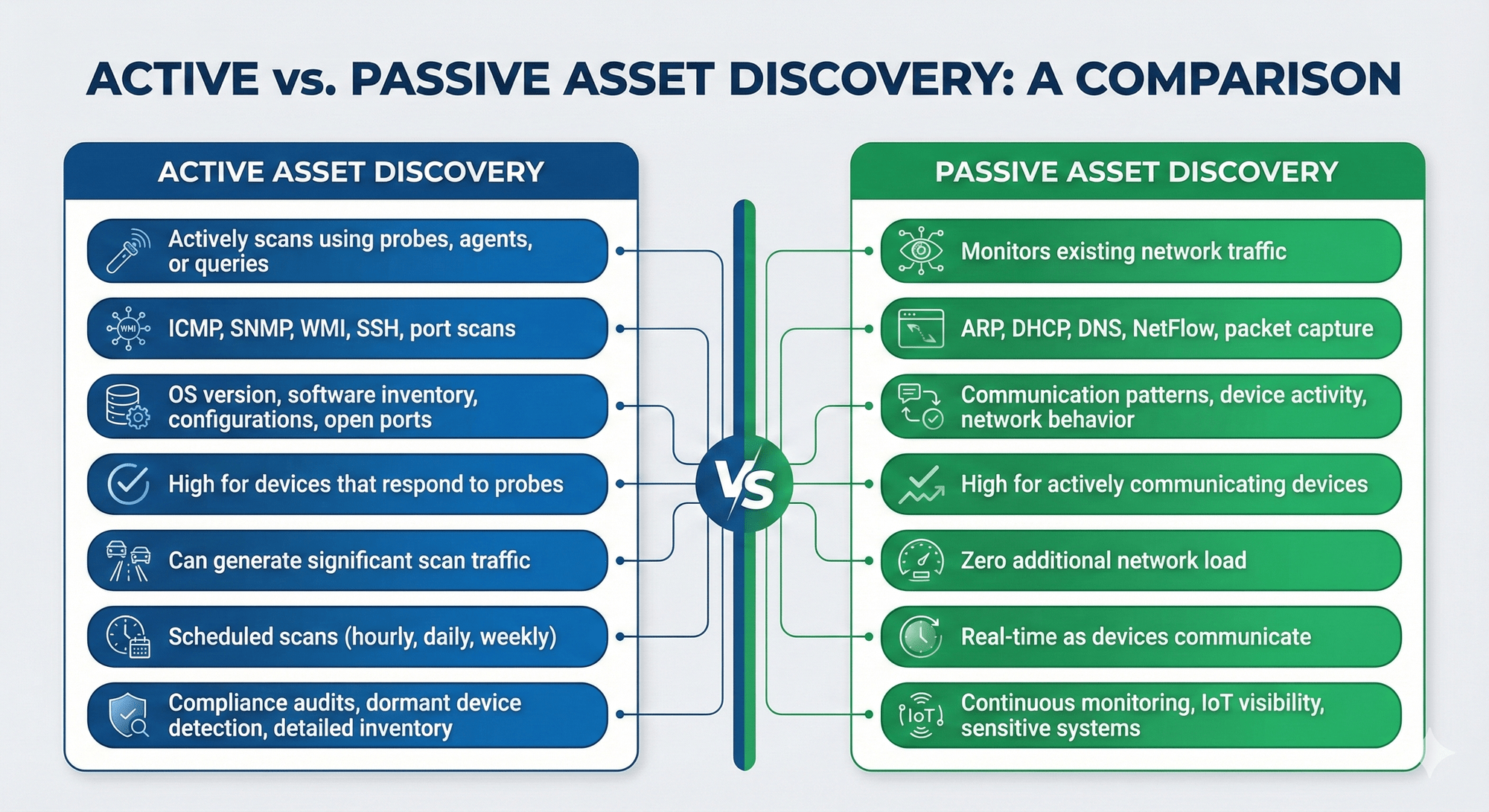
Active asset discovery directly scans your network infrastructure to identify devices and gather detailed configuration intelligence about them.
Think of it as sending out a census taker who knocks on every door. Tools actively probe the network using protocols like ICMP pings, SNMP requests, WMI queries, or port scans. They interrogate endpoints to collect OS versions, installed software, open ports, and configuration details.
Active scanners typically operate through:
These scans can run on schedules—daily, weekly, or on-demand—depending on how dynamic your environment is.
Active scanning provides precision that passive methods can't match:
Active discovery isn't without tradeoffs:
Active discovery excels in compliance-driven environments or organizations with frequent device turnover where detailed asset intelligence justifies the overhead.
Consider: Passive asset discovery takes the opposite approach. Instead of actively probing devices, it operates as a network observer, analyzing traffic patterns to infer device presence and behavior.
Passive tools monitor network traffic flows—ARP requests, DHCP handshakes, DNS queries, NetFlow data—to infer which devices are communicating. They watch silently from the sidelines, identifying assets based on their network behavior rather than interrogating them directly.
Passive discovery operates by:
Because it relies on existing traffic, passive discovery runs continuously without generating any additional network load.
Passive monitoring offers unique advantages:
Passive discovery has blind spots:
Passive discovery shines in dynamic environments where continuous, non-intrusive monitoring matters more than exhaustive device interrogation.
Both methods aim to answer the same question: what's on my network?—but they get there very differently. Neither approach is inherently better. Each solves different problems.
Here's the uncomfortable truth: your network changed multiple times in a week.
Someone spun up three cloud instances for testing. Marketing added a new SaaS tool nobody told IT about. A contractor plugged in their laptop. The break room got a smart TV. Two domain controllers were patched and rebooted.
Quarterly asset scans can't keep up with this pace. By the time you finish documenting what you found, the environment has already evolved. This is the fundamental problem with treating discovery as a periodic activity instead of a continuous capability.
Static CMDBs suffer from what practitioners call "configuration drift"—the inevitable gap between what your records say and what's actually running. Shadow IT creates blind spots that traditional scanning simply can't close, because unsanctioned devices and services often operate specifically to avoid detection.
Research shows that in cloud-native environments, assets are provisioned and decommissioned constantly. Ephemeral workloads might exist for hours or minutes. Weekly scans miss them entirely. Monthly scans are practically fiction.
This is why modern asset intelligence requires combining both active and passive approaches into a unified, always-on discovery strategy.
Organizations that treat active and passive discovery as competing options miss the point. The best visibility comes from combining them.
Active scans find dormant and offline assets—the forgotten servers, decommissioned endpoints still plugged in, and lab equipment nobody touches. Passive monitoring catches live devices the instant they connect—IoT sensors, contractor laptops, rogue access points, cloud workloads.
Together, they deliver complete coverage: what's currently running AND what exists but isn't talking right now.
Passive discovery provides real-time awareness as your environment changes. Active scans validate and enrich that data with detailed configuration intelligence on a scheduled basis.
This dual-layer approach means you're never working from stale information, but you also have the deep asset context needed for compliance and security analysis.
When a new device appears on your network, passive discovery flags it immediately. Active scanning can then interrogate it to determine if it's patched, configured correctly, and compliant with policy.
Speed matters. According to IBM research, breaches that took over 200 days to identify and contain averaged $5.5 million in costs. Early detection through continuous asset visibility dramatically shrinks that window.
The hybrid model keeps your Configuration Management Database synchronized with reality. Passive discovery updates the CMDB as changes happen. Active scans periodically verify and enrich those records.
The result? A living CMDB that actually reflects your environment instead of becoming an out-of-date spreadsheet that nobody trusts.
In today's hybrid and multi-cloud environments, this isn't optional. Organizations that combine active and passive discovery turn asset management from a compliance checkbox into a strategic security control.
Manual asset tracking doesn't scale. Spreadsheets can't keep up. Point solutions create more silos.
Our Asset Insights module continuously detects, classifies, and monitors every asset across on-prem, cloud, and hybrid environments without requiring constant manual intervention.
Secure.com employs a hybrid discovery strategy that combines:
When a new device connects, passive monitoring flags it instantly. Active scans then interrogate it to gather OS version, patch status, and configuration details. The platform correlates this data with existing records, updates the CMDB automatically, and flags any anomalies for review.
Beyond basic inventory, Secure.com generates interactive network topology diagrams that show how assets connect and depend on each other. You can filter by compliance scope (PCI, HIPAA), overlay vulnerabilities, and drill down from visual nodes to detailed asset records—all within minutes of initial setup.
Organizations using Secure.com report:
With Secure.com, teams move from reactive spreadsheets to proactive control. You gain the clarity to manage every device connected to your network—and the confidence to know you're not missing anything critical.
Active asset discovery scans your network by sending probes and queries to devices, gathering detailed configuration data like OS version, software inventory, and open ports. Passive asset discovery monitors existing network traffic (ARP, DHCP, DNS) to detect devices without generating additional network load. Active methods provide deep device intelligence but can impact network performance, while passive methods offer real-time, non-intrusive monitoring but may miss inactive devices.
No. Passive discovery relies on observing network traffic. If a device isn't currently communicating—because it's powered off, disconnected, or sitting idle—passive methods won't detect it. This is why a hybrid approach combining passive monitoring with periodic active scans provides the most complete visibility.
It depends on how dynamic your environment is. Organizations with frequent changes (cloud-heavy, DevOps-driven, high employee turnover) should run active scans daily or even multiple times per day. More stable environments might scan weekly. However, relying solely on periodic scans creates gaps. The best practice is combining scheduled active scans with continuous passive monitoring for real-time accuracy.
Healthcare, finance, manufacturing, and government sectors benefit significantly because they face strict compliance requirements (HIPAA, PCI DSS, NIST) while operating sensitive systems that can't tolerate disruptive scanning. Hybrid discovery provides them with both detailed audit data from active scans and non-intrusive, real-time monitoring from passive methods, meeting compliance needs without operational disruption.
Absolutely. Cloud environments are highly dynamic—resources provision and deprovision constantly, creating visibility gaps. Passive discovery detects new cloud instances the moment they connect, while active scanning via cloud APIs (AWS, Azure, GCP) pulls detailed configuration and compliance data. Together, they close blind spots in multi-cloud and hybrid environments where traditional tools struggle.
How does Secure.com handle shadow IT and rogue devices?
Secure.com's passive monitoring continuously watches network traffic for new connections. The instant an unauthorized device or unknown asset appears, the platform flags it and triggers an active scan to gather details. Assets are automatically classified, assigned risk scores, and compared against approved inventories. Security teams receive alerts about rogue devices immediately, enabling rapid response before they become security incidents.
Your network isn't static. It evolved multiple times this week, and it'll change again tomorrow.
Active and passive asset discovery aren't competing methods—they're complementary capabilities that together deliver the complete, continuous visibility modern security operations require. Active scans provide the deep device intelligence needed for compliance and detailed analysis. Passive monitoring delivers real-time awareness as your environment changes.
If you're still managing assets with quarterly scans and spreadsheets, you're already behind. Adopt a hybrid discovery strategy—or better yet, a platform like Secure.com that combines both automatically—to uncover every asset, close every blind spot, and stay ahead of whatever connects next.
Complete visibility isn't a luxury. It's the foundation on which everything else depends on.
AI-powered automation transforms incident response by cutting MTTR by 45-55%, turning hours-long investigations into minutes through intelligent triage, automated root cause analysis, and self-healing remediation.

SIEM detects threats through log analysis while SOAR automates response—together they create a powerful defense that cuts incident response times from hours to minutes.
Ivanti releases emergency patches for two critical zero-day vulnerabilities in EPMM that enable unauthenticated remote code execution, with CISA mandating federal agencies to patch by February 1, 2026.