Enhance Security with Asset Discovery Techniques
Asset discovery techniques reveal every network endpoint (from servers to IoT devices) giving security teams the visibility needed to defend against modern cyber threats
Asset discovery techniques reveal every network endpoint (from servers to IoT devices) giving security teams the visibility needed to defend against modern cyber threats

Asset discovery is foundational to cybersecurity, revealing all devices connected to your network. Combining active and passive discovery methods ensures comprehensive visibility across traditional IT assets, IoT devices, and non-traditional endpoints.
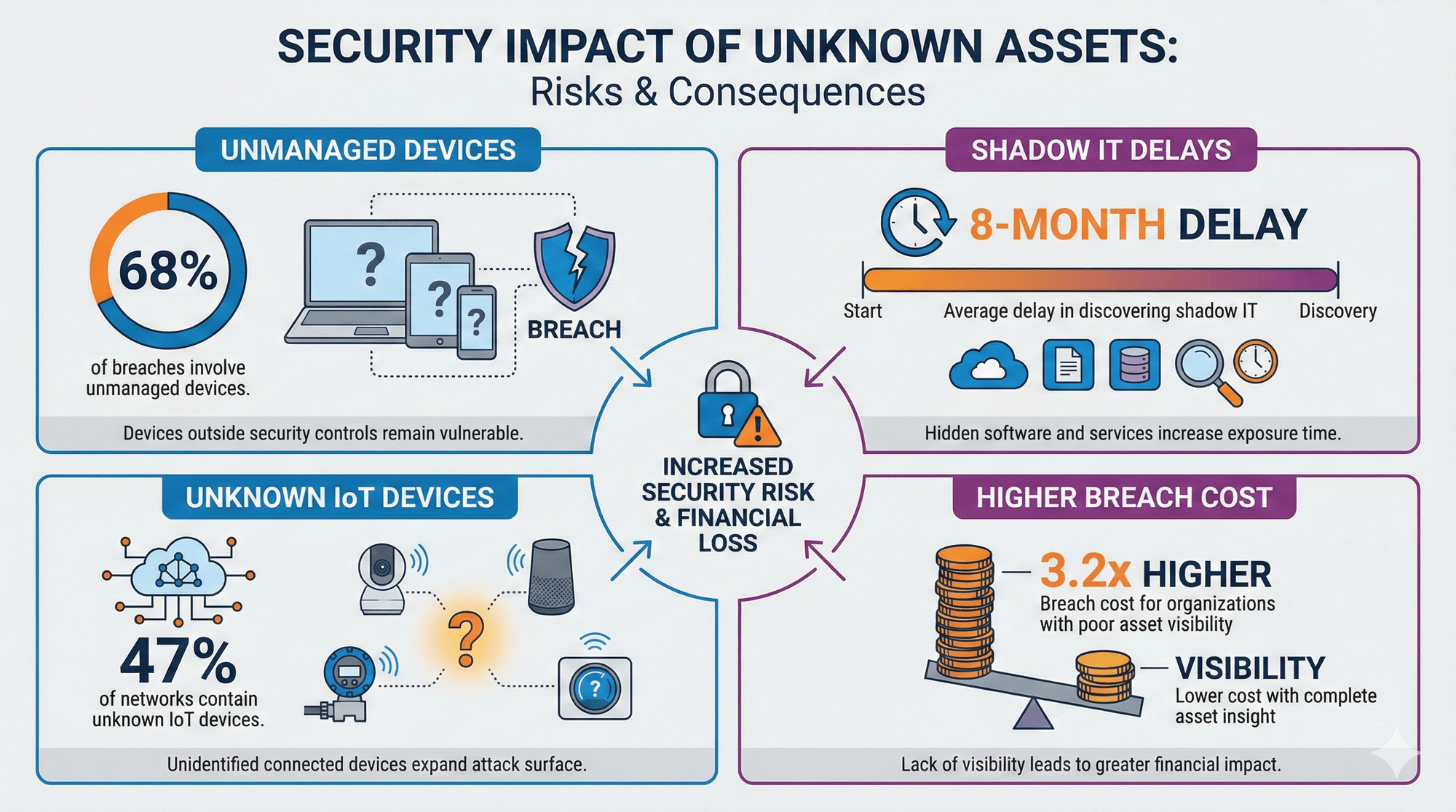
Security teams face a tough reality: they can't protect what they don't know exists. With networks growing to include cloud resources, remote workers, and IoT devices, keeping an accurate inventory is increasingly challenging—but attackers only need one unmonitored endpoint to gain access.
Asset discovery gives teams the visibility they need. By identifying every device, application, and service on the network, it shifts security from reactive guesswork to proactive defense. Whether it's preventing breaches, managing vulnerabilities, or meeting compliance requirements, thorough asset discovery is the foundation of effective cybersecurity.
There's a simple truth in cybersecurity: you can't protect what you don't know exists.
And in most organizations today, a surprising number of assets are completely invisible to security teams.
Cloud environments spin up and down every hour. Employees install new SaaS tools without telling IT. Developers launch test environments and forget to shut them down. Devices connect to the network and disappear just as quickly. In this kind of chaos, a static inventory or old CMDB (Configuration Management Database) doesn't stand a chance.
That's where asset discovery comes in — and why it's become non-negotiable for modern security programs.
1. Your attack surface changes all the time
New services, new identities, new cloud resources — they appear daily. Asset discovery helps you keep track so you're not blindsided by something you didn't even know was there.
2. You can't manage risk without knowing your assets
Every vulnerability, misconfiguration, and exposure ties back to an asset. If it's not discovered, it can't be protected, patched, or prioritized.
3. Shadow IT is unavoidable — unless you can see it
Teams will always adopt tools quickly to get work done. Discovery shines a light on the things that don't go through formal approval.
4. Incidents are easier to investigate
When something goes wrong, responders need instant context: What is this asset? Who owns it? How important is it? A complete inventory speeds everything up.
5. Your CMDB stays accurate automatically with continuous asset discovery
Instead of chasing spreadsheets or manually updating entries, continuous discovery keeps your data fresh and trustworthy.
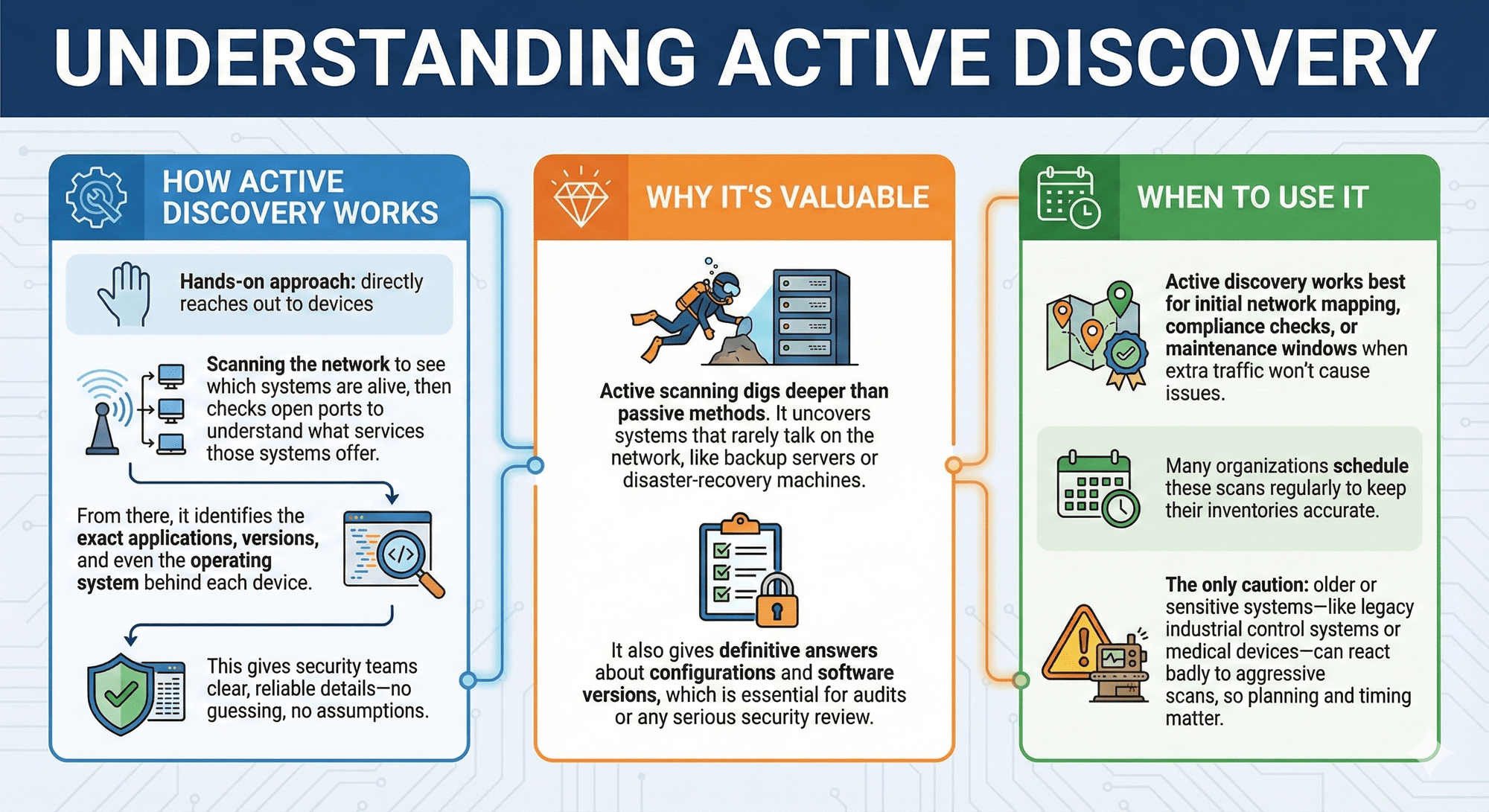
Active asset discovery takes a hands-on approach: it directly reaches out to devices to figure out what they are and what they're running. It starts by scanning the network to see which systems are alive, then checks open ports to understand what services those systems offer. From there, it identifies the exact applications, versions, and even the operating system behind each device.
This gives security teams clear, reliable details—no guessing, no assumptions.
Active scanning digs deeper than passive methods. It uncovers systems that rarely talk on the network, like backup servers or disaster-recovery machines. It also gives definitive answers about configurations and software versions, which is essential for audits or any serious security review.
Active discovery works best for initial network mapping, compliance checks, or maintenance windows when extra traffic won't cause issues. Many organizations schedule these scans regularly to keep their inventories accurate. The only caution: older or sensitive systems—like legacy industrial control systems or medical devices—can react badly to aggressive scans, so planning and timing matter.
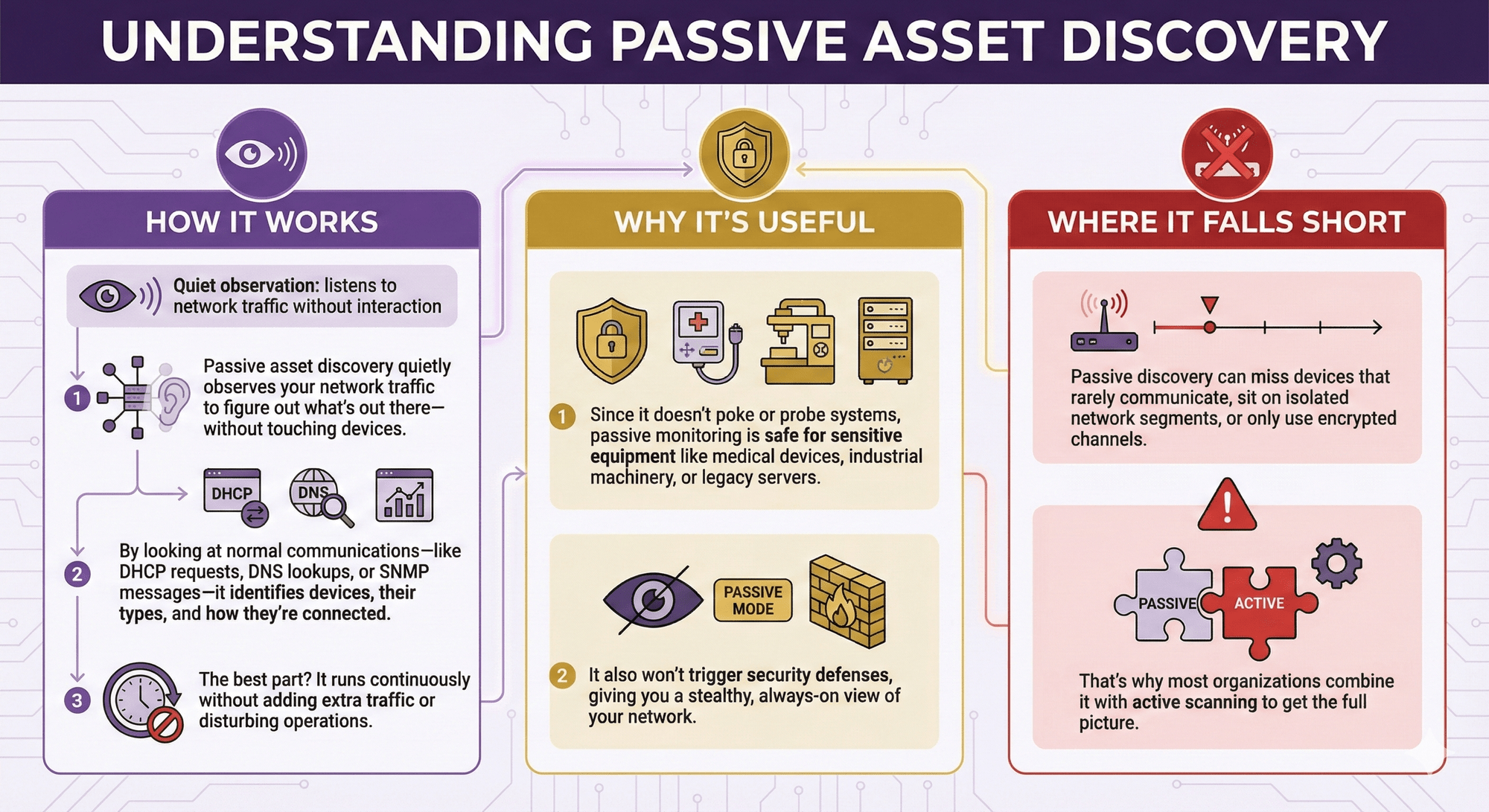
Passive asset discovery quietly observes your network traffic to figure out what's out there—without touching devices. By looking at normal communications—like DHCP requests, DNS lookups, or SNMP messages—it identifies devices, their types, and how they're connected. The best part? It runs continuously without adding extra traffic or disturbing operations.
Since it doesn't poke or probe systems, passive monitoring is safe for sensitive equipment like medical devices, industrial machinery, or legacy servers. It also won't trigger security defenses, giving you a stealthy, always-on view of your network.
Passive discovery can miss devices that rarely communicate, sit on isolated network segments, or only use encrypted channels. That's why most organizations combine it with active scanning to get the full picture.
Trying to rely on just one method (active or passive discovery) leaves gaps. Passive monitoring gives you an always-on view of your network, spotting devices the moment they communicate. Active scans dig deeper, verifying details and finding dormant or rarely used systems that passive tools might miss. Together, they create a complete, reliable picture.
Passive monitoring continuously collects data about your network by analyzing network traffic patterns, protocol behaviors, and device communications—without sending probes or queries that could disrupt operations or trigger security alerts.
With passive monitoring, you're always able to track new devices, as well as detect when devices come back online or go offline so that you can manage your devices effectively. Modern platforms that combine active and passive discovery methods provide one complete, up-to-date inventory of your devices with minimal guesswork.
Using both passive and active discovery gives complete coverage without disrupting operations. Sensitive systems—like medical devices, industrial networks, or legacy infrastructure—remain protected under passive monitoring, while active scans can run during low-impact times. Differences between the two approaches also help spot potential issues, such as segmentation gaps or unexpected access.
By blending passive and active discovery, organizations gain complete, accurate visibility across their networks—without putting operations at risk.
Today's networks are more than just laptops and servers. Smart cameras, sensors, badge readers, and other IoT devices are everywhere—and often added without IT knowing. These devices are easy targets for attackers because they're always connected but rarely monitored.
IoT devices don't follow standard rules, so traditional scans often miss them. Effective discovery looks at behavior, vendor info from MAC addresses, network protocols, and even certificates to identify devices safely and accurately.
Employees bring their own devices, and teams adopt cloud apps without approval. Integrating discovery with tools like NAC, MDM, and CASB helps track all devices and services—even the ones outside traditional IT channels.
Networks constantly change. Combining multiple discovery methods and continuously reconciling inventories keeps your asset list accurate and ensures no device slips through the cracks.
A discovery tool only works if your team can actually use it. If it's too complex, asset discovery often gets abandoned.
Dashboards and visualizations should be easy to understand, showing device relationships, network segmentation, and communication patterns at a glance.
Rapid deployment is important. Tools that take months to configure or integrate rarely deliver value before needs change. Quick-start, agentless solutions provide early wins and build confidence.
Avoid data silos. Your discovery tool should automatically feed other security systems using APIs, webhooks, or standard formats.
Connect with vulnerability management so newly discovered assets are scanned right away, closing security gaps before attackers can exploit them.
SIEM integration adds valuable context—device type, criticality, behavior patterns, and ownership—helping teams make faster, more accurate decisions.
CMDB integration keeps IT and security on the same page, making sure new assets are tracked and retired systems aren't mistakenly monitored.
Passive discovery only spots devices that are actively talking on the network. Machines that are turned off, isolated, or otherwise dormant can slip through. Encrypted traffic or unusual communication patterns can also make identification harder.
Not entirely. Passive discovery finds devices that are online and communicating, but quiet or offline devices won't show up. Combining passive monitoring with active scanning gives the best results.
Yes. Modern discovery tools can detect IoT devices, sensors, cameras, and even industrial equipment by analyzing traffic, protocols, and identifiers.
DHCP, DNS, ARP, SNMP, NetFlow, sFlow, mDNS, LLDP, CDP, plus application-level clues from device communications.
Absolutely. Passive monitoring gives real-time visibility while active scans uncover dormant systems and detailed configurations. Using both offers the clearest picture of your environment.
Asset discovery is fundamental to cybersecurity and cannot be deferred if you want effective security controls and protection against unauthorized access. Unknown assets equal unmanaged risk—and attackers only need one unnoticed endpoint to get inside.
The strongest approach combines the right tools, reliable processes, and continuous visibility. As networks evolve—cloud, IoT, remote devices—asset discovery must keep pace. Continuous monitoring ensures you stay ahead of threats in a constantly changing environment.