Why Passing Security Audits Is Not the Same as Being Secure
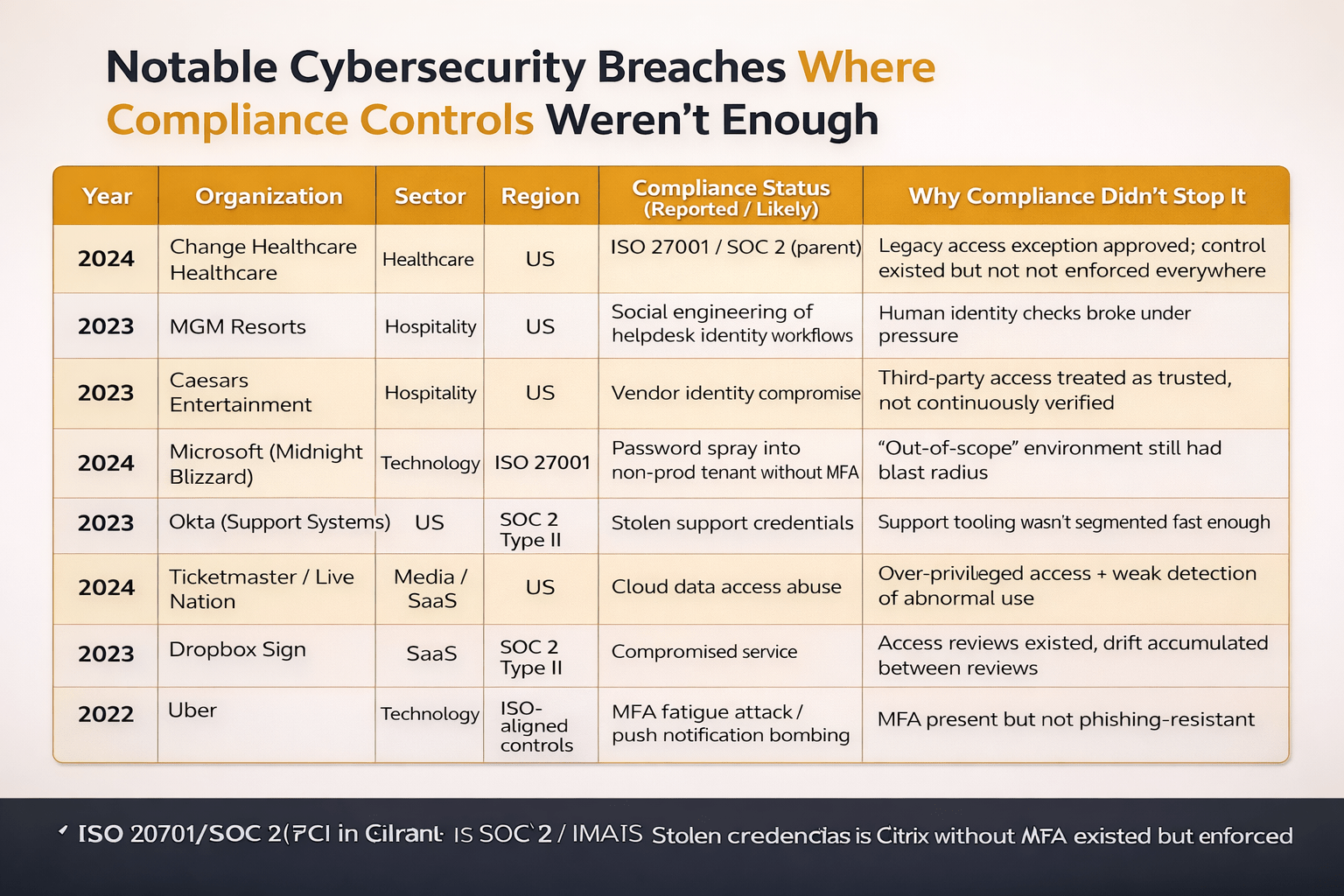
Major organizations with ISO 27001 and SOC 2 compliance suffered devastating breaches because controls existed on paper, not continuously in practice.
Major organizations with ISO 27001 and SOC 2 compliance suffered devastating breaches because controls existed on paper, not continuously in practice.

Over the last three years, major organizations suffered catastrophic breaches despite holding ISO 27001 and SOC 2 certifications. These incidents occurred because controls existed only on paper, not in practice. Compliance programs answer "Can you demonstrate controls existed at a point in time?" while attackers ask "Where does reality deviate from policy right now?" Between those two questions lies the breach.
In the past three years, major organizations in healthcare, finance, SaaS, hospitality, and technology faced devastating cyber incidents, even while ISO 27001 or SOC 2 Type II certified.
These breaches occurred because controls were documented but not active.
Compliance programs answer: “Did controls exist at the audit?”
Attackers ask a very different question: “Where does reality deviate from policy right now?”
Between those two questions lies the breach.
Multiple 2024–2025 reports now confirm this gap is widening, not shrinking:
Compliance didn’t fail because it was ignored. It failed because it was treated as the end state, rather than a minimum baseline.
Verizon’s 2025 Data Breach Investigations Report shows that stolen credentials appear in 88% of breaches involving web application attack patterns, making identity (not malware) the primary failure point.
Verizon reports third-party involvement rising to 30% of breaches, while exploitation of vulnerabilities increased 34% year-over-year—a pace no annual audit can keep up with.
IBM’s Cost of a Data Breach Report 2025 pegs the global average breach cost at $4.4M, with identity-driven incidents taking longer to contain and costing more over time.
Pattern
Why compliance fails
Healthcare environments routinely approve risk exceptions to maintain uptime. Those exceptions become permanent entry points for attackers.
Reality
Pattern
Why compliance fails
Vendor reviews are point-in-time attestations, not real-time enforcement.
Reality
Pattern
Why compliance fails
Non-production systems are often:
Reality
Identity: MFA everywhere without exceptions, phishing-resistant MFA for admins, continuous credential monitoring, just-in-time access. Would have stopped: Change Healthcare, Microsoft, Uber, MGM, Caesars.
Service Accounts: Continuous inventory, drift detection, automated expiration, blast-radius modeling. Would have stopped: Dropbox Sign, Ticketmaster, Okta.
Third-Party: Time-bound access, continuous validation (not annual), real-time monitoring. Would have limited: Caesars, healthcare/fintech incidents.
Effectiveness: Prove controls work today, continuous assurance, attack-path simulation, compliance as baseline, not a goal. It would have changed almost every outcome.
Compliance frameworks weren't designed to: detect real-time drift, enforce continuously, reason about attack paths, or govern machine identities. They establish minimums at points in time.
When minimums become the goal, security lags adversaries who operate continuously, adaptively, without scope boundaries.
The reframing: Compliance should be the exhaust of a strong security program—not its engine. Treat compliance as evidence, security as continuous enforcement, identity as primary perimeter, and exceptions as temporary monitored liabilities.
Organizations preventing breaches implement: continuous control enforcement, automated drift detection (hours, not months), phishing-resistant MFA everywhere, temporary exceptions with monitoring, continuous vendor validation, and unified visibility. Compliance asks, "Did we have controls during the audit?" Security asks, "Are controls enforced right now, everywhere?"
SOC 2 validates controls that existed during the audit months. It doesn't prove controls enforced today, cover all systems, prevent drift, or stop real-time attacks. Change Healthcare was compliant when breached. Compliance = minimum controls existed. Security = continuous enforcement everywhere.
Compliance satisfies audits. Security stops attackers. Compliance is validated periodically; security is enforced continuously. Compliance allows documented exceptions; security treats exceptions as an attack surface. Compliance focuses on in-scope; security covers what attackers reach. Every major breach satisfied compliance but failed against attacks.
Invert: make compliance output of continuous security. Implement real-time enforcement, automated drift detection, eliminate MFA exceptions, treat non-prod like production, and continuous vendor validation. Measure by "stopping attacks today," not "passed audit."
Identity—88% of breaches. Phishing-resistant MFA everywhere (especially "exempt" systems), continuous credential monitoring, just-in-time access, and review documented exceptions. Time-bound third-party credentials. These address the gaps of Change Healthcare, MGM, Microsoft, and Caesars.
2022-2025 shows: compliance certifications don't prevent breaches. Change Healthcare, MGM, Microsoft, Okta, and Ticketmaster were ISO 27001 or SOC 2certified when compromised. The failure was in treating compliance as the finish line.
Stolen credentials are responsible for 88% of web application breaches. Third-party involvement has doubled. Legacy systems with documented "acceptable risk" become entry points for attackers. The pattern repeats because compliance validates what existed during the audit, while attackers exploit what's happening right now.
Organizations that avoid these breaches don’t use compliance as a strategy. They enforce controls across all systems, remove MFA exceptions, validate vendors in real time, and prove controls work now—not just last quarter.
Compliance should be the exhaust of a strong security program—not its engine. When you build security that actually stops attackers, passing audits becomes automatic. When you build to pass audits, breaches become inevitable.
Don't just pass your next SOC2 audit—prove your controls work today. Ask your team: Are we preventing real threats right now, across all systems, including those outside audit scope? Shift from compliance checklists to continuous security enforcement. Make real-time protection your standard, not periodic validation.

Learn how Attribute-Based Access Control (ABAC) enables fine-grained, context-aware access decisions by evaluating user, resource, and environmental attributes replacing static role-based models with dynamic, adaptive security.

Cybercriminals are exploiting trusted PDF files and legitimate cloud infrastructure to harvest Dropbox credentials in a sophisticated new phishing campaign that bypasses traditional email security defenses.

Move beyond reactive alerts with a comprehensive guide to Data Loss Prevention (DLP)—transforming data security into a proactive, automated defense that secures sensitive assets across cloud, endpoints, and networks.