We Read 100 Cybersecurity Confessions So You Can Be Better Prepared
After analyzing 100 real security confessions, the story is clear: analysts are drowning in endless alerts, overloaded with tools, and often left without growth or recognition.
After analyzing 100 real security confessions, the story is clear: analysts are drowning in endless alerts, overloaded with tools, and often left without growth or recognition.

After reading 100 SOC confessions, the story is clear: analysts are drowning in endless alerts, overloaded with tools, and often left without growth or recognition. Burnout is tied to false positives, tool chaos, and poor metrics that prize ticket counts over real security outcomes. Yet brilliance shines through in shadow automation, ingenuity, and resilience. The path forward is smarter tuning, Digital Security Teammates or automated workflows and leadership that values outcomes over dashboards.
After analyzing 100 real security confessions from Reddit, industry forums, anonymous SOC diaries, and late-night Substack posts, it becomes clear that the modern SOC is equal parts battlefield and burnout factory. These aren’t just rants. They’re survival logs from analysts trying to keep up with the blinking, buzzing chaos of alerts, tools, dashboards, and expectations that rarely match reality.
Across all these confessions, the same themes surfaced again and again: Relentless alert fatigue, tool overload, career stagnation, metrics that reward the wrong behavior, and moments of quiet brilliance where analysts automate their way out of chaos.
This blog distills those stories into six core patterns that reveal what’s failing, what’s working, and what leaders must pay attention to if they want healthier, more resilient security teams.
Confession: “The job of an SOC analyst is destroying my life. We’re short-staffed, working double overnights. My mental and physical health can’t take it anymore.” – Reddit
If you’ve ever felt like your job was literally sucking the soul out of you, this confession probably stings with recognition. And it’s not an exaggeration.
Studies show SOCs deal with over 11,000 alerts per day on average, and with 67% going uninvestigated or unresolved due to resource constraints. That's like trying to drink from a firehose - while the building burns down around you.
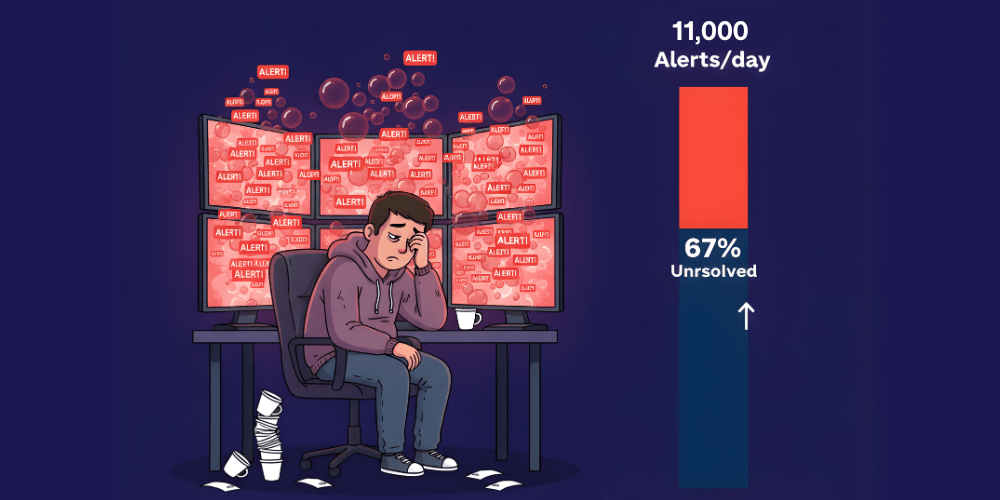
The result? Alert fatigue. Analysts get bombarded with so many false positives that their ability to spot the real threats plummets.
No wonder 70% of SOC teams admit they’re emotionally overwhelmed. One report even ties 31–34% of analyst burnout directly to nonstop alerts.
Two patterns keep showing up:
Burnout is not a badge of honor. SOCs need smarter tuning through SIEM optimization, better staffing, and leaders who value long-term focus over short-term heroics.
Confession: “I spend more time copying and pasting between dashboards than actually responding to threats.” – Radiant
Tool sprawl is the SOC's silent killer. 71% of teams use 10+ tools, and nearly half juggle 20 or more. Each comes with its own alerts, metrics, and dashboards. Integration? That’s a fairytale.
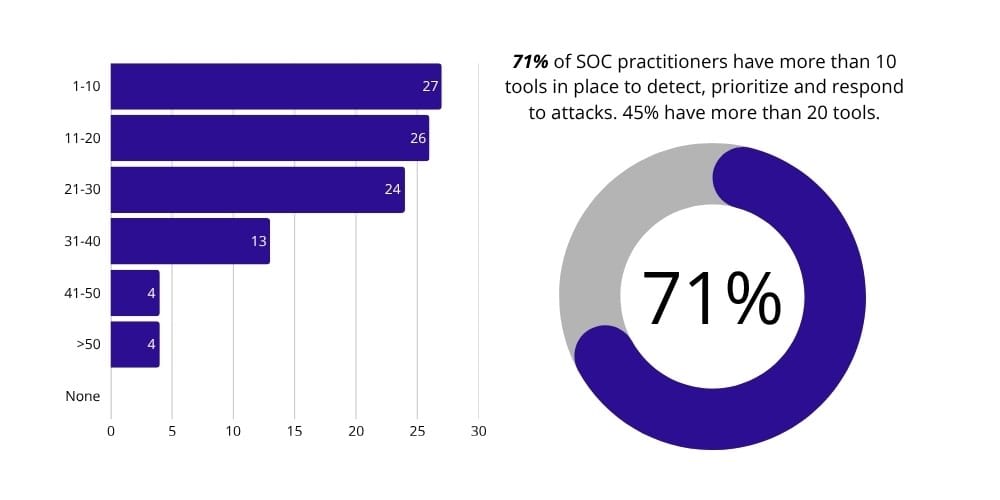
The patterns here are painfully clear:
No wonder analysts vent: “When everything is measured, nothing is clear.”
Every tool must earn its keep. SOCs should integrate systems through SOAR frameworks that actually reduce noise and connect workflows, not multiply dashboards.
Confession: “Got caught running scripts again. First Python, then PowerShell. Now I’m sneaking batch files just to survive.” – Reddit
When tools fail, humans hack the system. Analysts quietly build their own scripts, automating tasks leadership forgot to fix. It’s ingenious, and risky.
Patterns here:
SOC analysts are turning into accidental engineers just to keep them alive. But shadow automation also creates compliance risks and detection blind spots.
Don’t punish it, formalize it. Enable analysts to innovate safely through governance, reviews, and version control, keeping human-in-the-loop to guide safe automation practices.
Confession: “I feel like I’m constantly stuck with low-level tasks. It’s monotonous and I’m losing interest.” – Reddit
This is the quieter pain point: career stagnation. Analysts don’t just burn out from alerts; they burn out from feeling invisible.
Patterns:
The result is imposter syndrome, high turnover, and silent disengagement. One confession captured it best: “We’re the backbone of security but the least recognized.”
Leaders must create visible ladders (SOC → Detection Engineering → Threat Hunting). Recognition and rotation matter as much as tooling, and tracking MTTR can help measure actual improvement instead of vanity metrics.
Confession: “We’re measured on how many alerts we close, not how much risk we reduce. It’s all a security theater.” – Quora
If there’s one thing SOC analysts agree on, it’s this: The system loves numbers more than it loves outcomes. Leadership obsesses over dashboards full of “alerts closed,” while analysts roll their eyes because they know the real threats are often buried under noise.

The Data Behind the Drama:
Patterns:
SOCs must stop obsessing about numbers. The only metric that matters is “Can we reduce the risk?” Shift from volume-driven dashboards to outcome-driven reporting. Tie SOC works directly to business security goals instead of playing “alert whack-a-mole.”
Confession: Like, if a routine malware scan finds something malicious but it never executed is that an incident? What about if it attempts to execute but EDR stops it immediately? What about phishing? If someone clicks a link but it's like a Google form asking for contact information and they don't enter anything, is that an incident? - Reddit
Confessions reveal a surprising amount of hope too. Many analysts see the SOC as a stepping stone, if they’re given rotations, mentorship, and room to grow. Without that, even the most brilliant analysts burn out under pressure.
The Data Behind the Drama:
Patterns emerging from the confessions:
A healthy SOC is built on culture, not dashboards. When leaders reduce friction, encourage safe innovation, and invest in growth, analysts stop burning out—and start leveling up into the engineers, hunters, and architects every security program desperately needs.
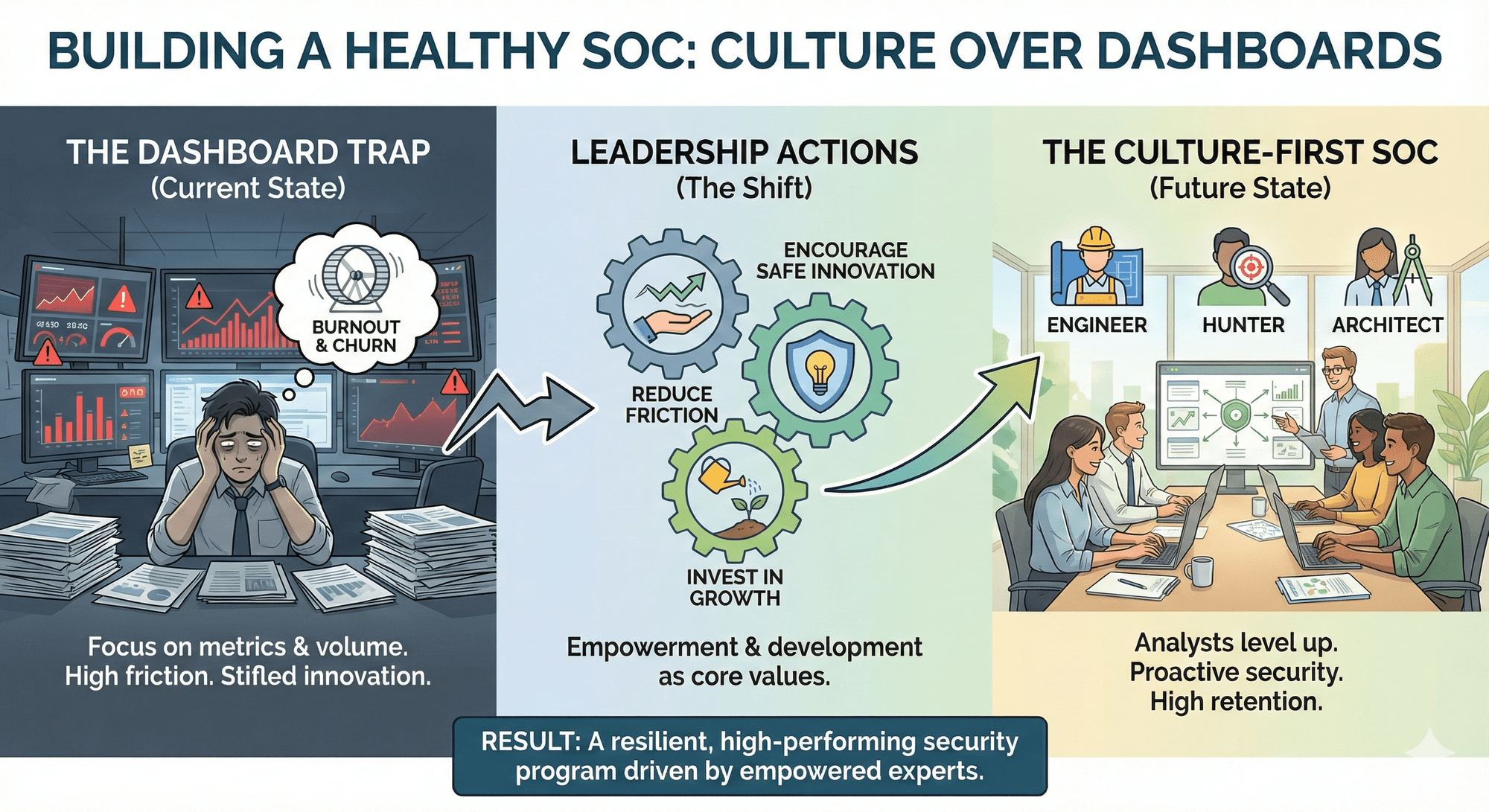
A hundred confessions later, the SOC feels like both a burnout factory and a brilliance incubator. Analysts confess to exhaustion, but also to hacking their way through chaos with humor, grit, and ingenuity.
The lesson? Security resilience doesn’t come from more dashboards. It comes from leaders reducing friction, recognizing effort, and building cultures where analysts don’t have to break rules to survive.

Security posture assessment evaluates your organization's overall cybersecurity strength, identifying vulnerabilities and providing a roadmap to enhance your defense against evolving threats.

A major source code leak exposes how routine age-verification selfies for popular apps are feeding a massive government surveillance and reporting machine.

A severe vulnerability in popular Grandstream desk phones gives attackers root access to listen to calls and pivot into corporate networks—highlighting a major blind spot for small businesses.