Secure: Threat Intelligence Weekly Roundup (December 1-5, 2025)
Five critical security incidents this week—including a maximum-severity React vulnerability and Chinese state-sponsored espionage—demand immediate action from security teams worldwide.
Five critical security incidents this week—including a maximum-severity React vulnerability and Chinese state-sponsored espionage—demand immediate action from security teams worldwide.

During the first week of December 2025, a convergence of critical security incidents has already given security leaders pause.
We will be looking at a maximum-severity vulnerability affecting millions of web applications and a sophisticated Chinese state-sponsored espionage campaign with year-long persistence, among other security threats.
This week's threats span the full spectrum of modern cybersecurity challenges. This roundup covers five major incidents that CISOs, CTOs, IT Managers, DevOps teams, and Security Analysts must understand and act upon.
A critical remote code execution vulnerability has sent shockwaves through the web development community. Disclosed on December 3, the CVE-2025-55182 vulnerability affects React Server Components with a CVSS score of 10.0 (Critical severity), enabling unauthenticated attackers to execute arbitrary code via specially crafted HTTP requests.
The flaw stems from unsafe deserialization in the React Server Components "Flight" protocol.
Security researchers at Wiz achieved near-100% exploitation reliability in testing - affecting React 19 and downstream frameworks including Next.js 15-16. Critically, default configurations are vulnerable - standard Next.js applications created with create-next-app are exploitable without any developer mistakes.
Within the first 24 hours of disclosure, proof-of-concept exploits circulated and the vulnerability was added to scanning tools. Major cloud providers including Cloudflare, Google Cloud, and Vercel deployed WAF rules, but these are temporary mitigations only.
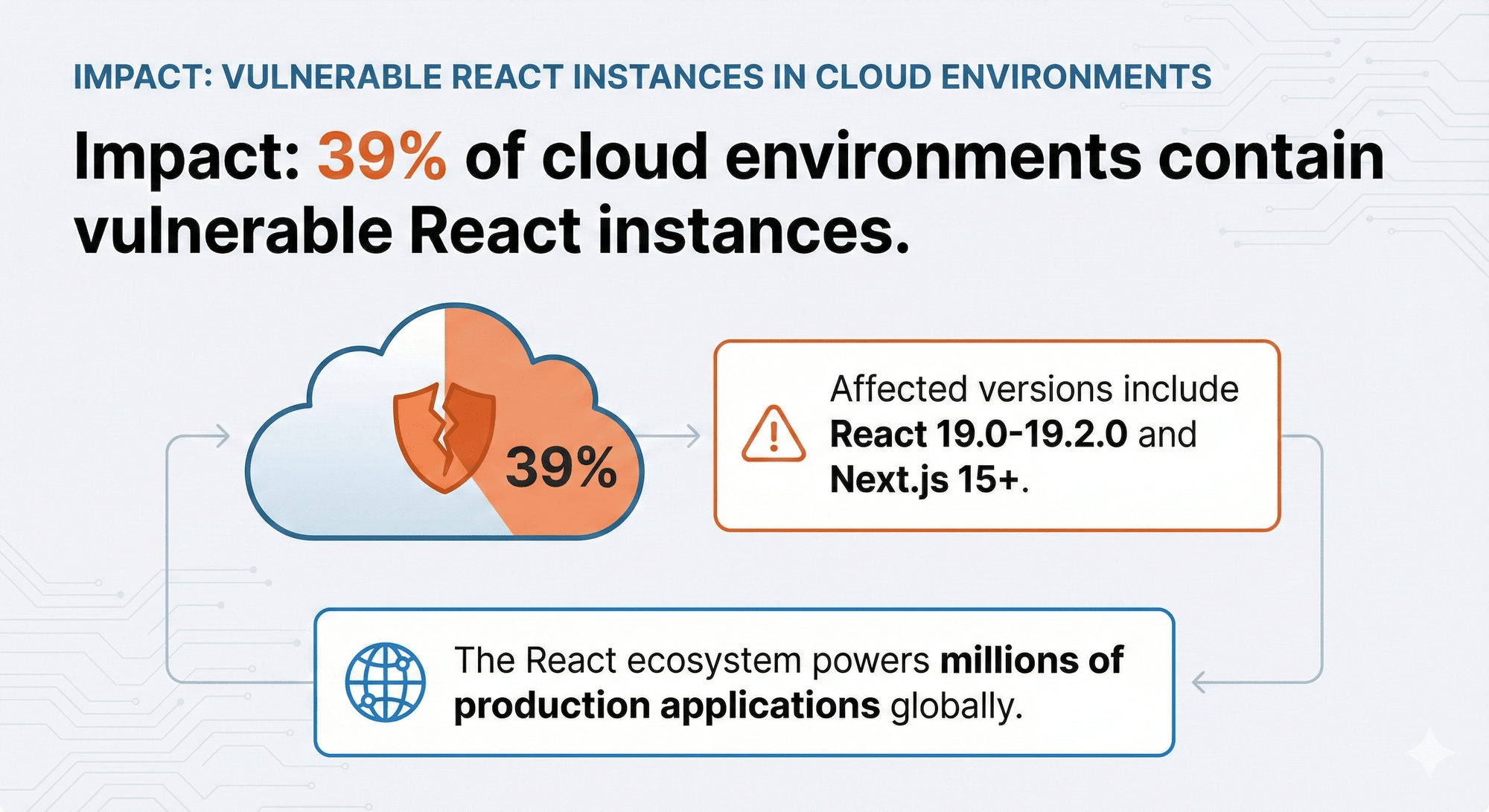
Impact: 39% of cloud environments contain vulnerable React instances. Affected versions include React 19.0-19.2.0 and Next.js 15+. The React ecosystem powers millions of production applications globally.
Organizations like CISA, NSA, and the Canadian Centre for Cyber Security (CCCS) have issued a joint alert on December 4, warning of ongoing intrusions by Chinese state-sponsored actors using BRICKSTORM malware. The sophisticated backdoor targets VMware vSphere and Windows environments, maintaining stealthy long-term access to US government agencies, IT firms, and legal services organizations.
Threat Group Warped Panda has been attributed to the BRICKSTORM campaign. The malware uses multiple encryption layers (HTTPS, WebSockets, nested TLS) for command and control communications, DNS-over-HTTPS for covert communications. It also comes with self-monitoring functions that automatically reinstall the malware in case of disruption. Each victim receives unique C2 domains, making detection and blocking exceptionally difficult.
The malware targets edge devices without traditional EDR support, then pivots to internal VMware vCenter servers. Attack chains identified so far include Active Directory database compromise, AD FS (Active Directory Federation Services) server exploitation, and credential harvesting for lateral movement.
South Korean e-commerce giant Coupang revealed on December 1 that 33.7 million customer accounts - 66% of South Korea's population - were compromised between June and November 2025. This makes it South Korea's biggest e-commerce breach - with exposed names, emails, phone numbers, addresses, and order histories. Payment credentials remained secure reportedly.
Investigators identified an unpatched internal API connecting authentication and logistics systems as the entry point. The police have identified a former Chinese Coupang employee - who now resides abroad - as a suspect, with evidence suggesting unrevoked access tokens enabled data exfiltration.
Under South Korea's Personal Information Protection Act, breached companies could face fines up to 3% of total sales. Given Coupang's $30.3 billion revenue in 2024, potential penalties could exceed $900 million (3% of $30.3B revenue).
British fiber broadband provider Brsk confirmed on December 1 that 230,105 customer records were stolen and advertised for sale on dark web forums. The breach includes names, contact details, addresses, installation data, geolocation coordinates, and - most concerning - flags identifying vulnerable customers with special needs or telecare requirements.
The vulnerable customer indicators create exceptional phishing risks, allowing attackers to craft highly targeted social engineering campaigns against individuals who may be more susceptible to manipulation.
Brsk has notified affected customers and engaged the Information Commissioner's Office (ICO) and law enforcement. For customers, it has offered 12 months of free Experian monitoring.
Security researcher Luke Marshall uncovered 17,430 verified live secrets across 5.6 million public GitLab repositories in a comprehensive scan completed in 24 hours for just $770. The exposed secrets affect 2,800+ organizations.
Commonly exposed credentials include Google Cloud Platform keys (5,200+), MongoDB credentials, Telegram bot tokens, and OpenAI API keys. Shockingly, some exposed secrets date back to as far as December 2009 - nearly 16 years old and still valid. These are basically "zombie credentials" that were imported from legacy systems and never rotated.
The research found GitLab repositories contain 35% higher secret density than Bitbucket repositories and an explosive growth in exposed secrets post-2018, correlating with the AI development boom. Marshall's responsible disclosure efforts - using automation to notify 120+ organizations - led to many credential revocations, though numerous secrets remain exposed.
For All Organizations:
API Security:
Insider Threat Programs:
Secret Management:
Detection Capabilities:
VMware Hardening:
Developer Security:
Compliance & Risk Management:
The incidents highlighted this week underscore that cybersecurity threats continue to evolve in sophistication and scale.
The React vulnerability (CVE-2025-55182) demonstrates how a single framework flaw can expose millions of applications overnight.
The BRICKSTORM campaign demonstrates how nation-state actors achieve year-long persistence through advanced evasion techniques. The Coupang and Brsk breaches expose insider threats and API security gaps that create massive exposure, while the GitLab secrets discovery reveals that developer security practices remain fundamentally inadequate.
Security leaders must recognize that traditional reactive approaches are insufficient. The convergence of supply chain risks, persistent nation-state threats, insider vulnerabilities, and developer security failures requires a multi-layered defense strategy combining rapid patching capabilities, continuous threat hunting, automated access controls, and cultural transformation around security practices.
These systemic security challenges are not isolated incidents. Organizations need executive commitment to security investments, security-first development practices, and continuous validation that security controls perform effectively under real-world conditions.