There's a New Way to Scale Cybersecurity Teams: Digital Security Teammates
Digital Security Teammates cut manual SOC work by 70% and improve MTTR by 45–55% with full transparency, not black-box automation.
Digital Security Teammates cut manual SOC work by 70% and improve MTTR by 45–55% with full transparency, not black-box automation.

Threats scale infinitely. Humans don't.
You've probably felt this if you work in security ops or IT management. Maybe you're staring at 747 unread alerts this morning. You may have been asked to monitor internal threats on your own. Your team has been trying to hire a mid-level analyst for six months with no luck, while your alert backlog grows by hundreds each week.
This isn't just burnout; it's a broken model. According to Gartner's 2025 Hype Cycle for Security Operations, AI SOC Agents are emerging to solve this exact problem. But here's what Gartner doesn't tell you: many "AI SOC" claims feel tool-centric or opaque; our approach is human-in-the-loop, explainable, and governable so that teams can trust the outcomes.
Digital Security Teammates are different. They're AI-backed colleagues that handle 70% of repetitive SOC work and improve MTTR by 45–55%, while explaining every decision so you stay in control.
The cybersecurity industry has a headcount crisis. Not because there aren't enough smart people in the world, but because the way we've built security programs —stacks of disconnected tools, each demanding attention, each generating its own queue of work —requires an impossible number of humans to operate effectively.
Which is why the industry is now trying something different: Digital Security Teammates.
Here's what it's not:
❌ A dashboard
❌ An "AI-powered" tool
❌ A black-box system
Imagine sitting at your desk on Monday, 9:47 AM, with your morning coffee, when a suspicious login alert pops up for [email protected] from an IP address in Iceland. Normally, this lands in your usual queue. You'd spend 10 minutes checking: Is this user traveling? What's their regular login pattern? Is the IP malicious? Has this device been seen before?
By 9:48 AM, your teammate has already:
You click "Approve" in Slack, the teammate revokes John's session, forces a password reset, notifies John via email, creates a ticket, and logs everything with a complete audit trail.
All within minutes.
That's a Digital Security Teammate. Not a dashboard to check. Not a report to read. A colleague who does the work.
Your analysts spend 20% of their time on actual investigation and decision-making.
The other 80%?
Alert triage. Evidence collection. Baseline enforcement. Checking whether that suspicious login is actually Dave from accounting, who forgot his laptop and is working from his phone.
Again!

The teammate can independently create and execute complex workflows ranging from correlating data across your entire environment to following up with users about suspicious activity. Everything it does gets tracked in a transparent activity monitor. If it hits a blocker (like missing access to a system), it autonomously escalates rather than failing silently.
Real example: When a critical CVE drops (e.g., Log4Shell-class), the teammate:
Omnichannel communication addresses a fundamental truth about security work: context-switching between tools is exhausting and error-prone. So teammates meet you where you already work. They proactively reach out via Slack or Gmail, share updates, and deliver insights without requiring you to open yet another tab.
Real example: Instead of opening seven tabs every morning to check SIEM, ticketing, OKTA, CMDB, compliance dashboards, and vulnerability scanners, you open Slack:
"Morning! Here's your security briefing:
That's context-switching eliminated. One interface. One teammate.
Context-aware intelligence leverages your organization's knowledge base and your real-time context. The teammate knows what you're currently looking at on the platform and proactively highlights relevant insights. No more hunting through documentation or trying to remember which dashboard shows identity correlation.
Real example: You're investigating an alert for "unusual data transfer." In a traditional tool, you'd manually piece together:
With a Digital Security Teammate, you can see context automatically in a Context Card the moment you open the alert:
User: Sarah Chen (Marketing Manager, 3 years tenure)
Asset: customer_database.csv (Critical - contains PII)
Baseline: Sarah typically accesses 50MB/week; this transfer was 2.4GB
Blast radius: 140,000 customer records
Recommendation: Escalate to L2 and notify Sarah's manager
That's intelligence, not just random and scattered data or siloed telemetry.
Admin personalization recognizes that every security team has its own culture and workflows. Security leaders can customize the teammate's behaviors, define approval requirements, set auto-action boundaries, essentially teaching it to work the way your team works, not the other way around.
Real example: Maria, a Security Team Lead, sets up her teammate "Cybie" in 5 minutes:
Result: Cybie works exactly like Maria's team, not the other way around. And when the team culture changes, Maria adjusts Cybie's settings in the UI—no vendor support ticket required.
The unified command interface provides a developer-friendly way to interact. You can think of it like a command-line interface for security operations: simple text commands can trigger complex analyses, navigate the platform, and interact with teammates without interrupting your flow.
Real example: Instead of clicking through 6 dashboards, you type in the command bar:
The deployment pattern is straightforward. First, you connect your existing infrastructure — cloud platforms, SaaS applications, endpoints — through secure connectors. These feed into a live knowledge graph of your environment: every asset, every identity, every relationship, and risk pathway.
Then you deploy a Digital Security Teammate (Cybie) suited to your organization's maturity level. You may be a lean team establishing baseline coverage. You may be a growing SOC that needs deeper investigative capabilities. You may be a security leader who needs to prove continuous compliance to external auditors.
Here's what the first week actually looks like:
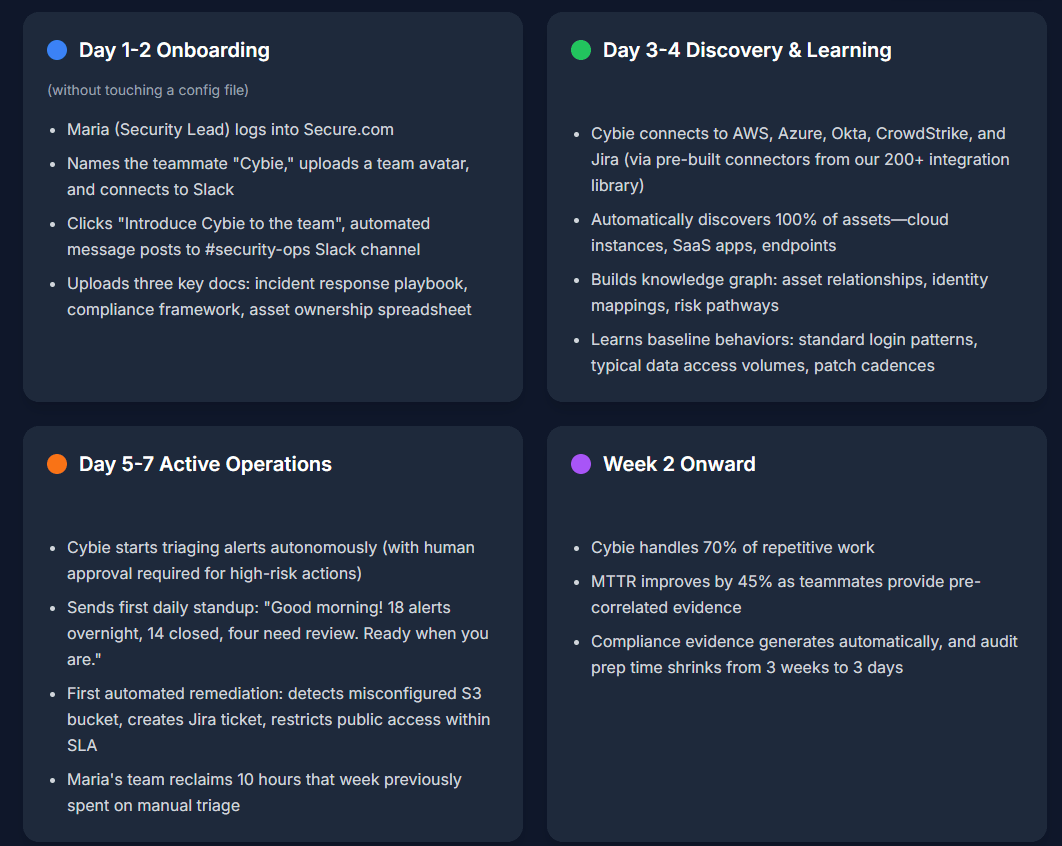
This is what "time to value" actually means: not quarters of integration hell, but days to measurable impact.
Once deployed, the teammate runs continuously. It discovers new assets as they appear. It triages alerts based on your defined priorities. It collects evidence, patches vulnerabilities, and enforces security baselines, all while logging every action with its rationale.
Here's the critical part: It surfaces only what needs human judgment.
That suspicious login? The teammate has already gathered the relevant context, recent access patterns, geolocation data, and device fingerprints and presents it with a recommendation. You make the call. It executes and documents.
When it takes automated action, like isolating a compromised endpoint or revoking a credential, it does so within the guardrails you've defined and with full explainability. Every decision includes its reasoning. Every outcome aligns with your compliance frameworks.
During a significant attack, digital security teammates prioritize response using AI models that calculate business impact, asset criticality, and likelihood of escalation. Instead of reacting to alert volume, they focus on what can cause the most harm or disruption. They coordinate containment, assign responsibilities, and maintain a real-time operational picture for leadership. This approach allows organizations to make decisions quickly while minimizing damage and downtime.
Here's where Digital Security Teammates diverges sharply from the "AI SOC" marketing you've probably seen elsewhere.
Many security tools have started adding "AI" features that are really just repackaged rules or simple workflows. Others use opaque machine learning models that make decisions you can't explain. Neither approach works when you need to show an auditor why you took a specific action, or when something goes wrong and you need to understand why the system behaved the way it did.
Let's be specific about what makes Digital Security Teammates different from the wave of "AI SOC" tools flooding the market:
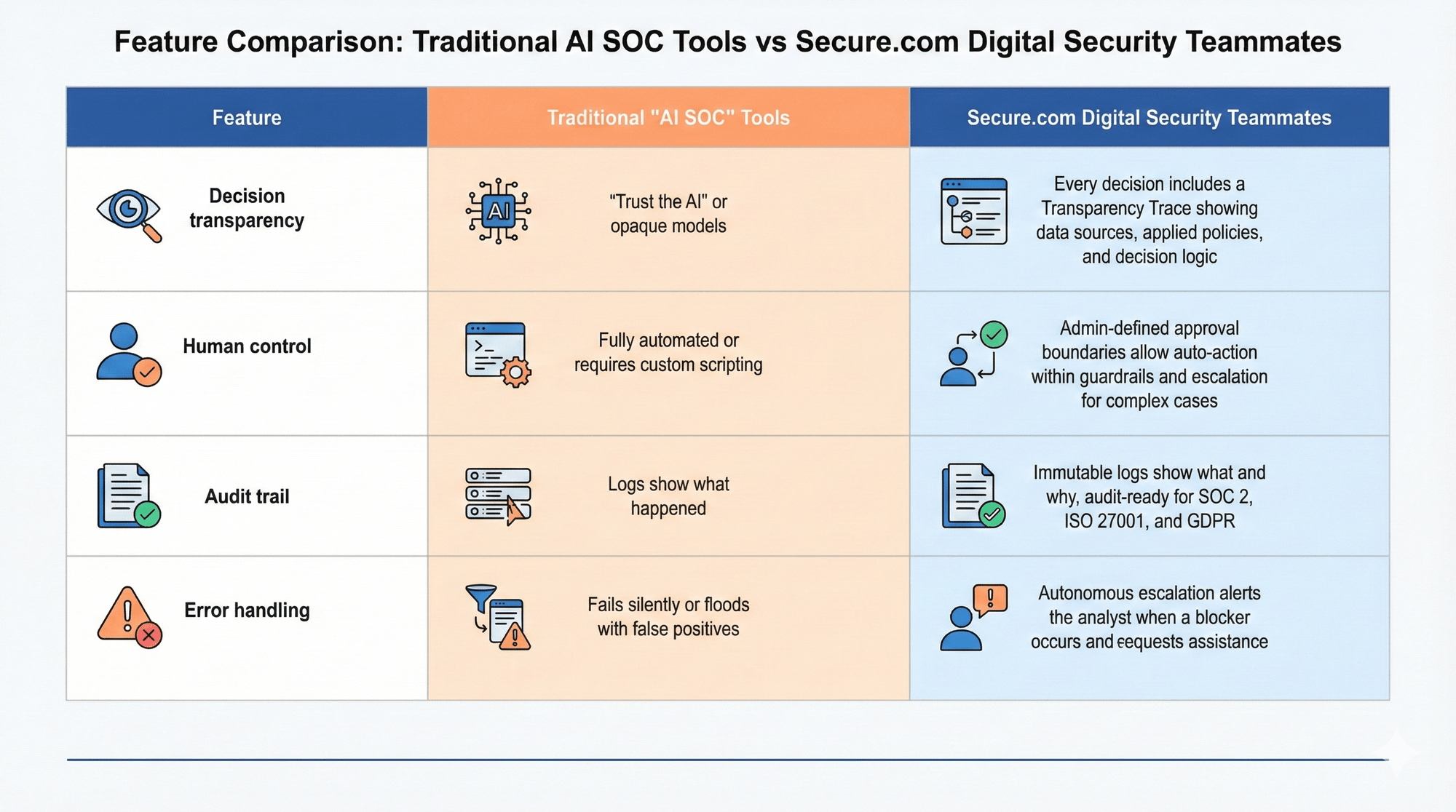
The difference: Gartner's 2025 Hype Cycle cites "AI SOC Agents" as an Innovation Trigger; success hinges on explainability, governance, and human oversight. That's Digital Security Teammates by design.
Digital Security Teammates include what Secure.com calls a "Transparency Trace"—immutable logs that show not just what happened, but why. Which signals triggered the analysis? Which policies applied? Which decision paths did the teammate consider?
This isn't just about compliance, though that matters. It's about trust. Your security program can't run on faith. You need to be able to look under the hood, verify the reasoning, and adjust the behaviors when your environment or requirements change.
Because every action is logged and aligned to compliance frameworks, organizations can measure what they're getting. Here's what early adopters report:
"We reclaimed 2,000+ analyst hours per year."
— Security Operations Lead, FinTech (Series B)
"Our 3-person SOC was drowning in 400+ daily alerts. Our Digital Security Teammate now handles 70% of the triage autonomously. The team has enough time to hunt threats instead of chasing false positives."
"Incident response dropped materially with automated containment and pre-correlated evidence."
— CISO, Healthcare SaaS
"When ransomware hit a dev environment, our teammate isolated the endpoint, revoked compromised credentials, and notified stakeholders before I even saw the alert. 45-55% faster MTTR isn't marketing—it's what we're actually seeing."
"Audit prep used to take 3 weeks. Now it takes 3 days."
— Compliance Manager, Cloud Infrastructure
The math is simple:
This isn't about replacing humans. It's about giving them leverage.
The headcount gap isn't going away because the threat landscape isn't getting simpler, and the tool sprawl problem won't solve itself.
But Digital Security Teammates represent a fundamental shift in how security work gets done, from a model that requires impossible human scale to one that gives humans leverage.
You stop drowning in alert queues. You stop burning out from repetitive tasks like checking if "suspicious login" is actually Dave from accounting. You start doing the work you're actually trained for: investigating complex incidents and hunting sophisticated threats.
You get measurable ROI: 70% reduction in manual work, 45-55% faster response times, and continuous audit-readiness. You prove security's business value to the board. You retain your best analysts because they're no longer burning out.
You reclaim time for proactive defense. Instead of spending 6 hours gathering data for an investigation, your Digital Security Teammate delivers pre-correlated evidence in a few minutes. You build workflows without waiting for dev resources.
The promise isn't "autonomous security". It's something more practical and achievable: security teams that work like teams are supposed to, with digital colleagues handling baseline operations while humans handle strategic thinking.
And unlike traditional hiring (247 days average time-to-fill), your Digital Security Teammate is operational within a few hours of connecting your first systems.
Digital security teammates rely on platforms that combine SIEM data, endpoint telemetry, and AI-driven correlation. These tools provide contextual detection rather than static, rule-based alerts, helping teams focus on actual threats rather than noise.
They leverage adaptive learning models that understand the expected behavior of systems and users. By correlating multiple data points, they can mitigate false positives and ensure analysts focus on genuine risks.
They lead recovery efforts by prioritizing critical systems, validating restored data, and coordinating with business units to resume operations safely. They also conduct post-incident reviews to strengthen future response plans and improve overall resilience.
After detecting the threat, Digital Security Teammates rebuild clean environments from validated baselines and reapply essential security controls. They verify system integrity, ensure credentials are reset, and monitor for residual indicators of compromise before systems are fully restored to production.
They maintain continuous compliance monitoring dashboards and automatically collect evidence throughout the year. This preparation means that when auditors request proof, the organization already has verified documentation ready, minimizing disruption and reducing audit preparation time.
Book a 15-minute demo and watch how a Digital Security Teammate can make your life easier:

The irony is stark: the Netherlands' privacy regulator tasked with protecting citizen data has itself become a victim of sophisticated zero-day attacks.

Insider threats exploit trusted access and everyday behavior, making them harder to detect and often more damaging than external cyberattacks.

Track the right SOC metrics to catch threats faster, work smarter, and prove your security program is actually working.