Built for Speed: Deploy in Days, Not Quarters
Deploy SOC-level security in days, not quarters. Secure.com's Digital Security Teammates plug in fast, automate 95% of triage, and give lean teams the leverage they've been missing.
Deploy SOC-level security in days, not quarters. Secure.com's Digital Security Teammates plug in fast, automate 95% of triage, and give lean teams the leverage they've been missing.

Secure.com's Digital Security Teammates deliver full-spectrum SOC capabilities—triage, investigation, remediation while augmenting your team without replacing analysts. Built for lean teams, they plug into your existing stack in 30 minutes to a few days depending on integration complexity, start working immediately, and give your analysts time to focus on real threats instead of alert noise. Speed meets security without shortcuts.
Most security tools promise protection but deliver months of process. Six weeks of discovery calls. Three months of integration work. Another quarter for playbook tuning. And you're still not covered.
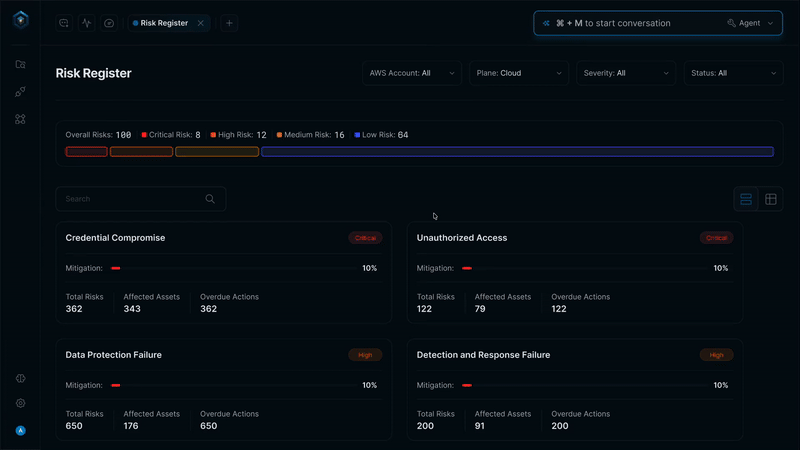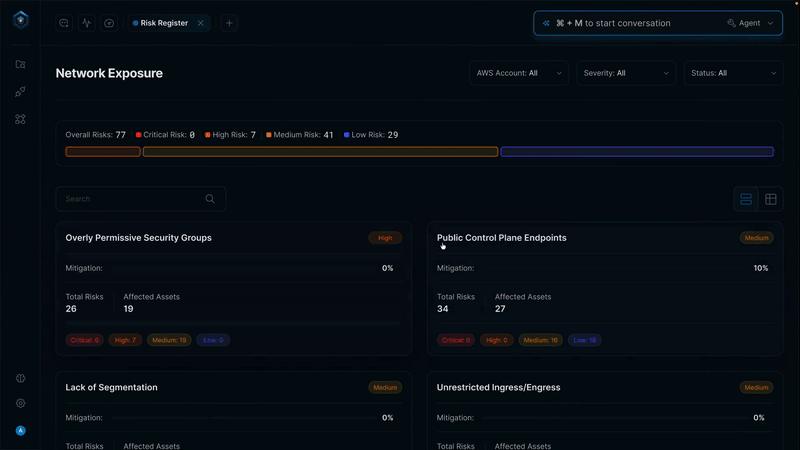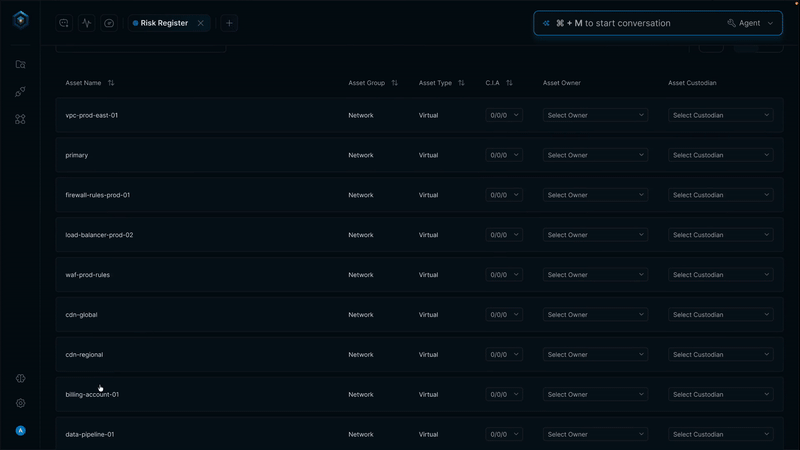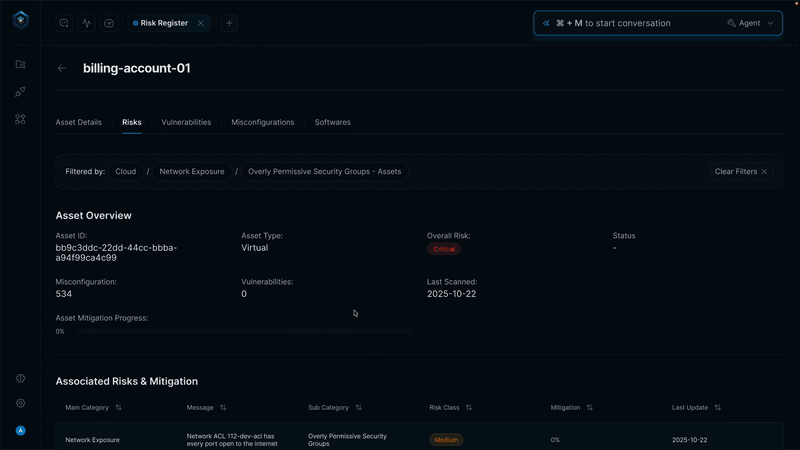
Meanwhile, your attack surface keeps growing. Threat actors don't wait for your rollout timeline, and your two-person security team can't keep up with 10,000 alerts a week, and according to industry data, 70% of those alerts go ignored due to volume.
According to Dark Reading, it takes an average of 90 to 180 days to fill a cybersecurity role—if you can even hire at all.
Secure.com flips this model. Our Digital Security Teammates don't need months to onboard. They plug into your environment in days, start triaging alerts immediately, and deliver SOC-level coverage without the SOC-level headcount. This is cybersecurity for teams doing the actual work, not just building org charts.
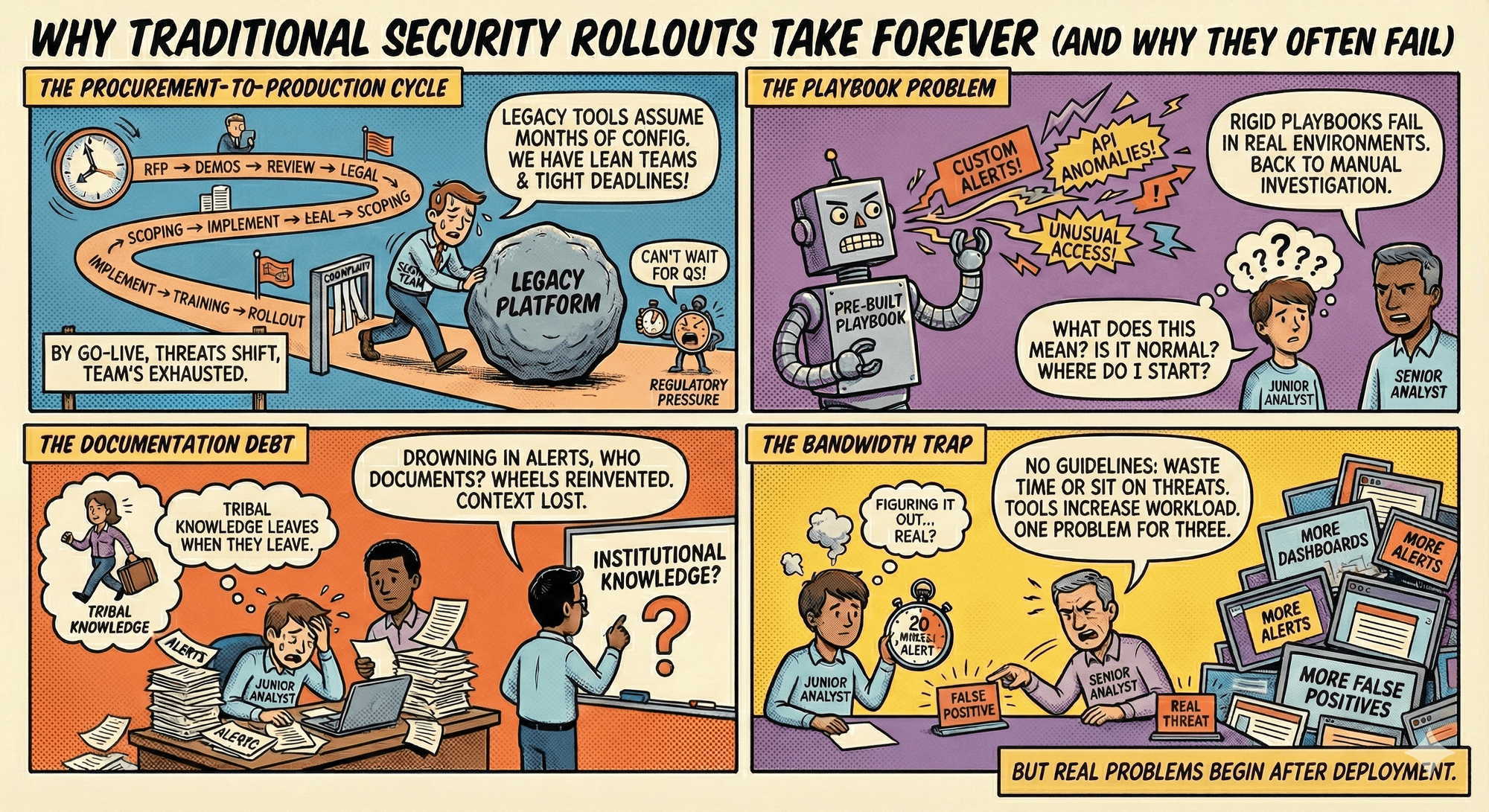
The procurement-to-production cycle for most security tools looks like this:
RFP → vendor demos → procurement review → legal negotiations → integration scoping → implementation → playbook development → analyst training → production rollout.
By the time you go live, the threat landscape has shifted, and your team is exhausted.
Legacy platforms assume you have dedicated integration engineers, a fully staffed SOC, and months to burn on configuration. They don't account for the realities most mid-market teams face: lean headcount, aggressive timelines, and regulatory pressure that won't wait until Q3.
But here's where the real problems start showing up, even for teams that make it through deployment.
Most vendors promise pre-built playbooks that'll solve your alert fatigue. Sounds great until your alerts hit production. Your environment generates custom alerts that lack uniformity.
One CloudTrail API anomaly looks nothing like the next. What worked for suspicious login attempts doesn't apply to unusual S3 bucket access patterns. Rigid playbooks designed for generic scenarios fail when faced with the variation your actual infrastructure produces.
Instead of automated responses, you're back to manual investigation—except now you're doing it inside a new tool you spent three months implementing.
Junior analysts are left asking:
Every investigation should build institutional knowledge. Document findings, record normal baselines, and capture investigation paths that worked. But when your team is drowning in alerts and racing through triage, who has time to maintain that documentation?
The result?
Time and attention are finite resources. If your junior analysts spend 20 minutes per alert figuring out whether it's real, you're burning analyst-hours faster than you can replace them. Without clear escalation guidelines, they either waste senior analysts' time with false positives or sit on real threats trying to "figure it out."
Even after deployment, these tools add to your workload instead of reducing it. More dashboards to monitor. More alerts to triage. More false positives, your analysts don't have time to investigate. You traded one problem for three new ones.
Secure.com's Digital Security Teammates deploy in 30 minutes, with most customers achieving full production readiness within days. No six-month integration roadmap. No vendor-dependent playbook development. No "we'll get back to you after implementation."
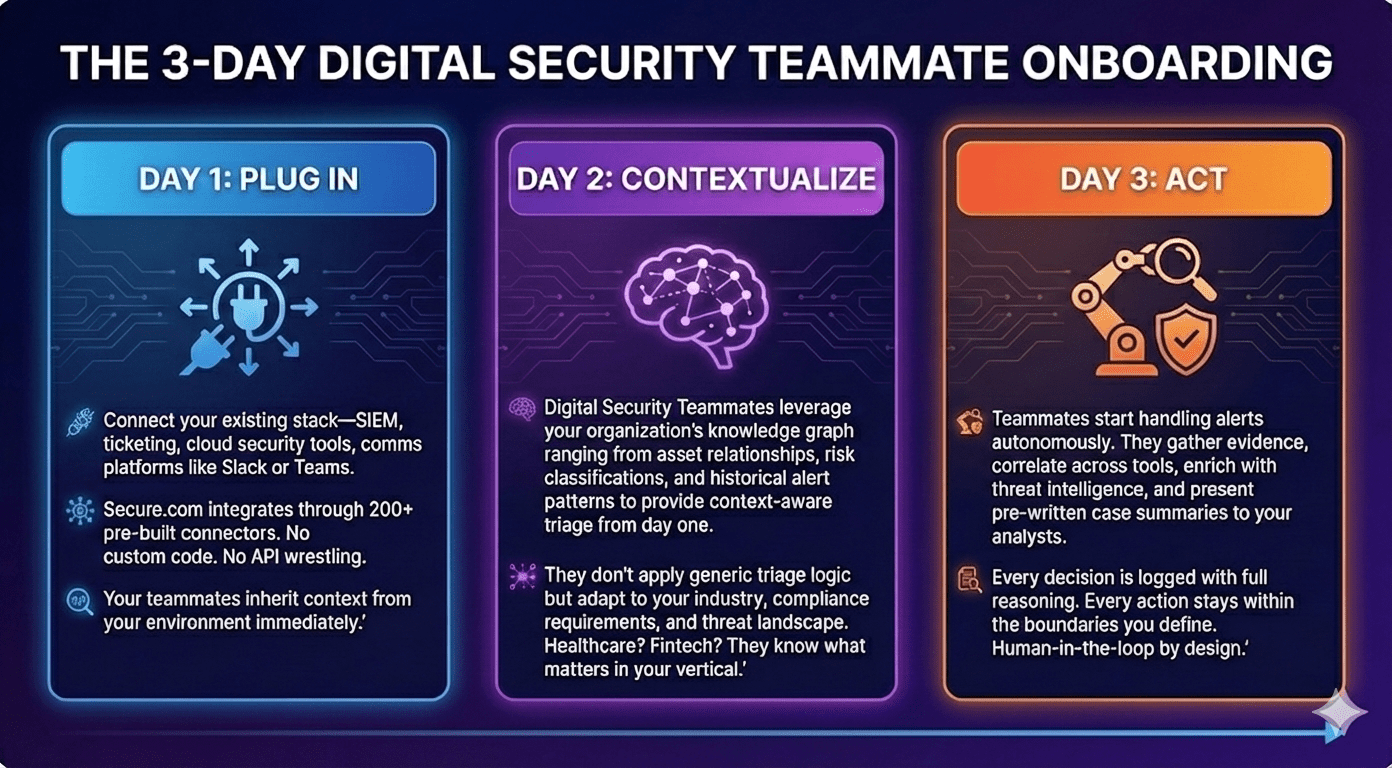
Here's how it works:
Connect your existing stack—SIEM, ticketing, cloud security tools, comms platforms like Slack or Teams. Secure.com integrates through 200+ pre-built connectors. No custom code. No API wrestling. Your teammates inherit context from your environment immediately.
Digital Security Teammates leverage your organization's knowledge graph ranging from asset relationships, risk classifications, and historical alert patterns to provide context-aware triage from day one. They don't apply generic triage logic but adapt to your industry, compliance requirements, and threat landscape. Healthcare? Fintech? They know what matters in your vertical.
Teammates start handling alerts autonomously. They gather evidence, correlate across tools, enrich with threat intelligence, and present pre-written case summaries to your analysts. Every decision is logged with full reasoning. Every action stays within the boundaries you define. Human-in-the-loop by design.
No six-week ramp. No analyst training sessions. No playbook documentation phase. You're covered before most vendors finish their kickoff call.
Traditional security platforms give you features. Digital Security Teammates give you outcomes.
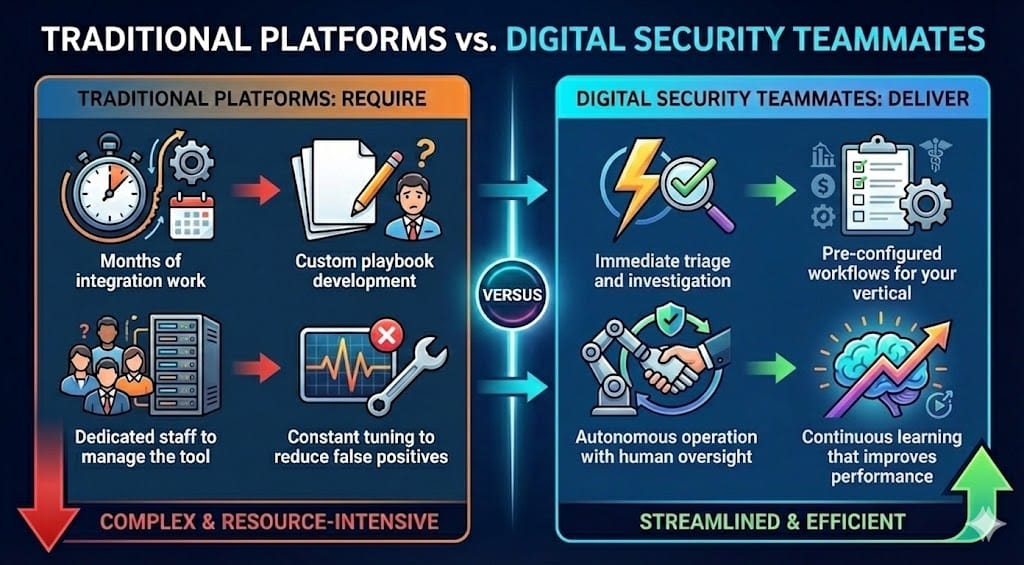
The shift is from "here's another dashboard" to "here's a teammate who already knows what to do." They don't need training. They don't burn out. They don't miss alerts at 3 AM. And they free up your analysts to focus on the work only humans can do—strategic threat hunting, incident response planning, and security posture improvements.
Fast deployment doesn't mean cutting corners. Every action Digital Security Teammates take is governed by explainability, auditability, and reversibility.
Every triage decision includes context-aware reasoning with full transparency traces showing which signals were evaluated, what data was checked, and what logic was applied. This isn't just for compliance; it's how your team builds institutional knowledge and improves over time.
Immutable logs capture every workflow execution, every API call, every automated response. Leadership and auditors can trace exactly what happened, when, and why. This isn't just for compliance—it's how your team learns and improves over time.
If the teammate takes an automated action your analyst disagrees with, it can be reviewed, modified, or rolled back. Mistakes become learning opportunities. The platform captures feedback and refines workflows accordingly.
This is governed autonomy—automation with guardrails. Your teammates act fast, transparently, and stay within the boundaries you control.
Organizations deploying Digital Security Teammates see measurable impact within weeks:
Whether you're the lone IT manager at a 50-person company or the VP of Security at a 500-employee organization, Secure.com adapts to your reality. No bloated onboarding process. No assumption that you have a team of six analysts waiting for work.
Digital Security Teammates scale with your needs:
The headcount crisis won't fix itself. CISOs can't magic new hires into existence, and they can't stretch two analysts across three shifts indefinitely. Secure.com gives your team the leverage to move faster, work smarter, and deliver security outcomes that matter—without waiting for next quarter's hiring budget.
Most customers live within 48-72 hours. Key integrations connect through pre-built APIs, and Digital Security Teammates come pre-configured for your industry and organization size. No custom code required.
No. Teammates ship with built-in triage logic, investigation workflows, and remediation playbooks tailored to your vertical. You can customize workflows if you want, but it's not required to start.
White-glove onboarding is included from day one. Our team helps with integration, configuration, and tuning. After deployment, 24/7 support ensures you're never blocked. We don't just deploy—we partner.
Yes. We support 200+ integrations, including SIEM platforms, ticketing systems, cloud security tools, EDR solutions, and collaboration platforms like Slack and Teams. If it has an API, we can connect to it.
Every decision the Digital Security Teammates make is logged with full reasoning, context, and evidence trails. Your analysts can review every triage call, every investigation step, and every automated action. Transparency is architectural, not optional.
Every action can be reviewed, modified, or reversed. When analysts provide feedback, the platform captures it and refines workflows. Mistakes become training data, not recurring problems. Human oversight is built into the system.
Threats don't wait for your deployment timeline. Your defense shouldn't either. Traditional security rollouts take quarters—Secure.com delivers full-scope SOC support in days.
This isn't about deploying another tool. It's about deploying a teammate that thinks like a CISO, acts like a SOC analyst, and works 24/7 without burning out. A teammate that triages alerts while you sleep, investigates anomalies while your analysts focus on strategic work, and documents everything so you're audit-ready by default.
You don't need a bigger team. You need leverage. Digital Security Teammates give you that leverage, starting this week, not next quarter.
Ready to skip the integration slog and start protecting your organization today? Book a demo and see what same-week deployment actually looks like.

Security posture assessment evaluates your organization's overall cybersecurity strength, identifying vulnerabilities and providing a roadmap to enhance your defense against evolving threats.

A major source code leak exposes how routine age-verification selfies for popular apps are feeding a massive government surveillance and reporting machine.

A severe vulnerability in popular Grandstream desk phones gives attackers root access to listen to calls and pivot into corporate networks—highlighting a major blind spot for small businesses.