
OT Asset Discovery: Complete Visibility for Security Risks
Gain real-time visibility into every machine, endpoint, and legacy system without disruption. Reduce blind spots across IT and OT to enhance resilience and protect critical infrastructure.

The OT Visibility Gap: Where IT Tools Fall Short
Traditional IT discovery tools weren't built for industrial networks. They miss critical devices, disrupt operations, and leave OT environments dangerously exposed.
Legacy Limitations
Most asset discovery tools rely on active scanning that can disrupt sensitive OT systems or fail to detect proprietary protocols. This leads to scattered inventories and dangerous blind spots.
Disjointed Visibility
Without unified insight and a CMDB, OT asset data becomes scattered across tools, spreadsheets, and manual processes. Security teams struggle to track what they own, weakening response and resilience.
Compliance Pressures
Regulations demand proof of monitoring and control across OT environments. Incomplete visibility creates audit gaps, operational fatigue, and increased organizational risk.
Modern vs. Traditional Discovery
Traditional Asset Discovery
Periodic & Manual - Relies on infrequent network scans and manual spreadsheets that are tedious, error-prone, and quickly outdated.
Limited Scope - Often covers only on-premise IT assets while completely missing cloud resources, SaaS applications, and shadow IT.
Lack of Context - Provides raw technical data (like IP addresses) but lacks business context, ownership, and interdependency insights.
Modern Asset Discovery with Secure.com
AI/ML-Driven Discovery - Leverages machine learning for asset classification and for determining Asset Criticality Value based on system parameters and business context.
API-Based & Agentless - Uses advanced automated discovery through API polling and an agentless architecture, enabling organizations to be up and running within 30 minutes.
CMDB Integration - Builds a Configuration Management Database (CMDB) aligned with international standards and applies ML-based classification, improving accuracy by 40%.
Real-Time Visual Map
See your entire asset ecosystem mapped in one interactive view. Track relationships, identify shadow IT, and prioritize risk across thousands of assets in real time.
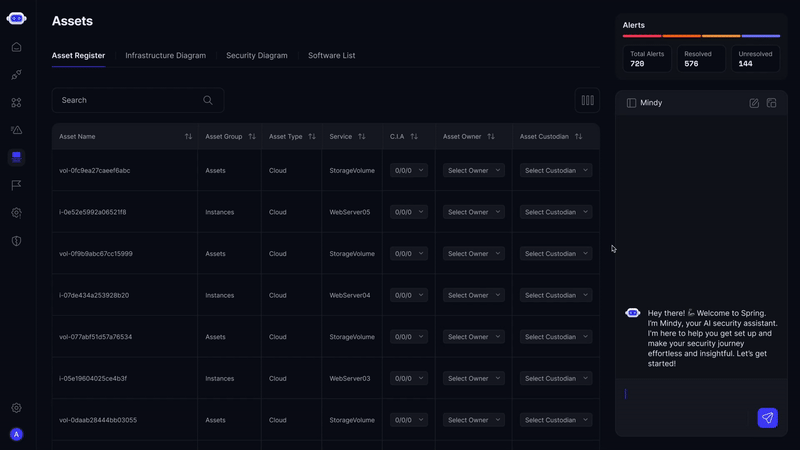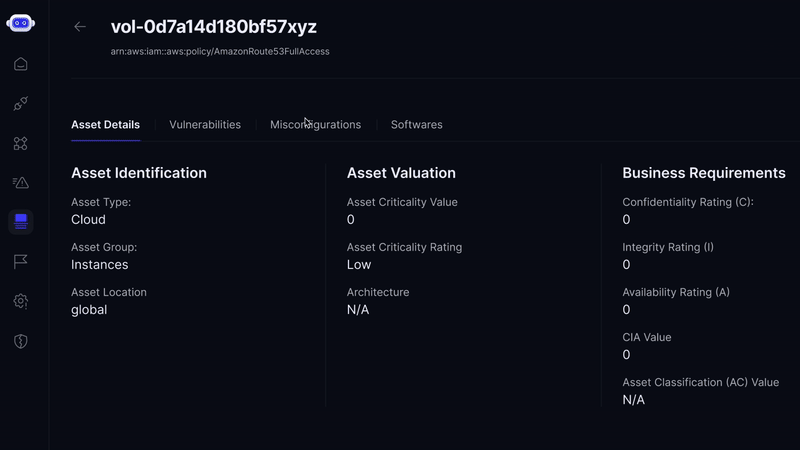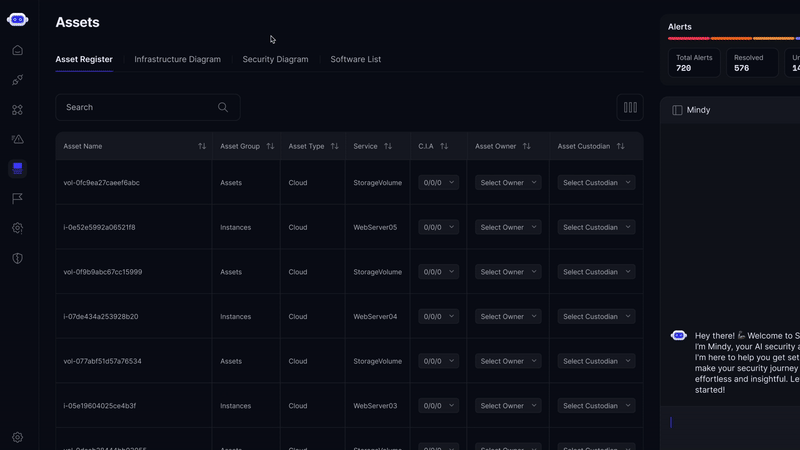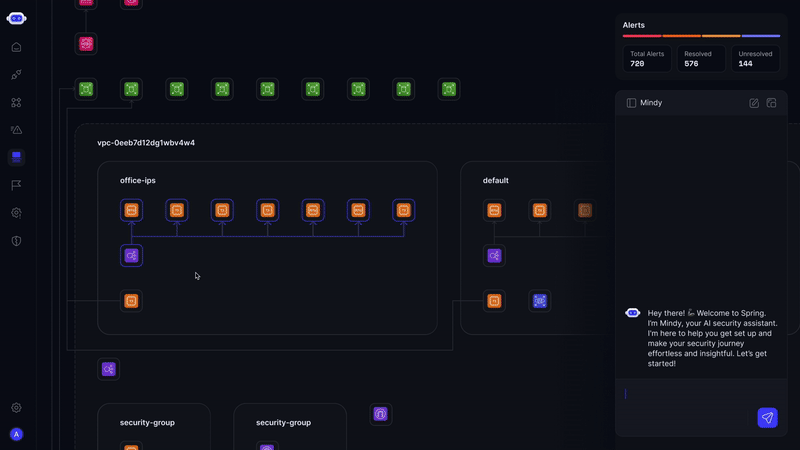

How Secure.com Helps
Our AI-native platform is purpose-built to address the complexities of asset discovery, transforming how lean teams achieve full visibility across OT and IT environments.

Comprehensive Automated Discovery
Our agentless architecture uses advanced API polling to map machines, applications, and relationships. Get up and running within 30 minutes by connecting your existing tools, SaaS apps, and cloud infrastructure.

Intelligent Classification & CMDB
We use machine learning to classify assets, determine criticality, and construct a CMDB aligned with international standards—improving classification accuracy by 40%.

Real-Time Attack Surface Map
View a real-time map of your attack surface, plotting assets, risks, and misconfigurations. This reduces blind spots by 40% and enhances decision-making.

Context-Aware Insights
Instead of showing raw data, we map assets, identities, and business context to highlight what truly matters—ensuring your security posture stays adaptive.
Frequently Asked Questions
Let Your Team Focus on Growth,Not Grunt Work.
Secure.com gives you the firepower of a full security team—without the headcount.
Explore More Asset Discovery Solutions
Discover specialized pages to learn how Secure.com empowers every environment and asset type:
OT Asset Discovery
Complete visibility for operational technology
Asset Intelligence
Intelligent asset classification and insights
IT Asset Discovery
Comprehensive IT asset visibility
Cloud Asset Discovery
Discover all cloud resources
Enterprise Asset Discovery
Enterprise-wide asset visibility
SaaS Asset Discovery
Discover all SaaS applications
Agentless Asset Discovery
Agentless discovery architecture
ICS Asset Discovery
Industrial control system discovery
Automated Asset Discovery
Fully automated discovery workflows
Continuous Asset Discovery
Continuous monitoring and discovery
Network Asset Discovery
Network-based asset discovery
Real-Time Asset Discovery
Real-time asset visibility
